Introduction
Decoding the Topic
Every developer, at some point in their journey, is entrusted with the monumental task of ensuring data security, especially passwords. The weight of this responsibility cannot be emphasized enough. How we handle this task, choosing between hashing and encryption, can be the defining line between a rock-solid application and a security disaster.
The Nitty-Gritty of User Passwords in Web Development
The Achilles’ Heel: Plain Text Passwords
We often hear tales of a breached system with passwords stored in plain text. This, to developers, is the equivalent of a nightmare. Not only does this compromise user security instantaneously, but it also tarnishes the reputation of our software solutions.
The Shield and Sword: Encryption and Hashing
To counter the vulnerabilities of plain text, developers are equipped with two powerful tools: encryption and hashing. Both techniques transform passwords into intricate data strings, impeding unauthorized access.
A Deep Dive into Hashing
Unraveling Hashing
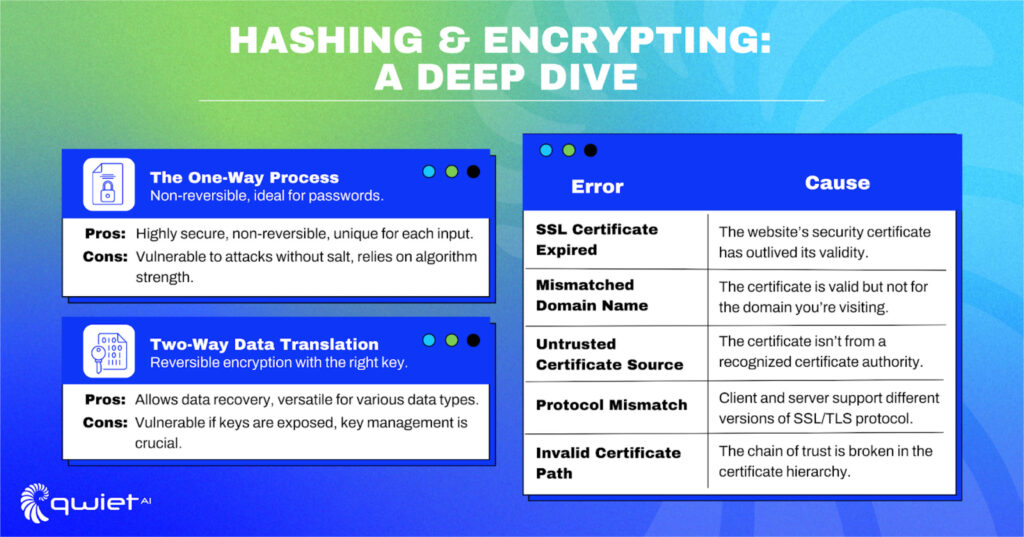
Hashing is a process that converts input, like passwords, into a fixed-size, random-looking string. A crucial aspect of hashing for developers is its non-reversible nature. No matter how sophisticated the adversary, a hashed value can’t be reverted to its original state.
Algorithms We Trust: bcrypt and SHA-256
Over time, various hashing algorithms have been introduced, but bcrypt and SHA-256 remain developer favorites. Bcrypt, especially, has carved a niche in password hashing due to its built-in salting functionality, offering enhanced security.
Hands-on with bcrypt
| # Python example: Hashing a password using bcrypt import bcrypt password = input(“Enter user password: “).encode() hashed_password = bcrypt.hashpw(password, bcrypt.gensalt(12)) # Higher salt rounds for added security print(f“Hashed Password: {hashed_password.decode()}”) |
Hashing’s Strengths and Vulnerabilities
Hashing’s uniqueness lies in its one-directional nature, making it ideal for passwords. However, developers must remain wary of attacks, such as rainbow table attacks, emphasizing the importance of salting hashes.
The Science of Encryption
Encryption Explained
Contrary to hashing, encryption is reversible. It involves translating data into a secret code, retrievable only with the correct decryption key. This method is crucial for developers for data we need to access in its original form.
Trusted Encryption Algorithms: AES and RSA
AES and RSA stand as two encryption giants in our toolkit. While AES is symmetric, employing the same key for encryption and decryption, RSA is asymmetric, involving a public and private key pair—each for one of the processes.
Crafting Encryption with AES
| # Python example: Encrypting data using AES from Crypto.Cipher import AES from Crypto.Random import get_random_bytes key = get_random_bytes(16) cipher = AES.new(key, AES.MODE_EAX) ciphertext, _ = cipher.encrypt_and_digest(b‘UserSensitiveData’) print(f“Encrypted Data: {ciphertext}”) |
Encryption’s Power and its Achilles’ Heel
Encryption’s biggest strength is its reversibility, but its most considerable potential weakness lies therein. If malicious actors access the encryption keys, they can decrypt the data. This emphasizes the importance of stringent key management for developers.
Hashing vs. Encrypting: Navigating the Maze
Contrasting Mechanisms
The primary distinction lies in the core nature: hashing is one-way, while encryption is two-way. Developers need to evaluate their requirements and make a choice accordingly.
The Developer’s Decision Matrix
Passwords typically get hashed since we merely verify matches. But encryption becomes the methodology of choice for other user data—like messages or personal details—because we might need to read the actual content.
Code Showdown: Hashed vs. Encrypted
| # Python example: Comparing hashed and encrypted data encrypted_data = cipher.encrypt(b’UserPassword’) print(f”Encrypted: {encrypted_data}”) hashed_data = bcrypt.hashpw(“UserPassword”.encode(), bcrypt.gensalt()) print(f”Hashed: {hashed_data.decode()}”) |
Weighing Security Implications
Both methods excel in security, but developers must be aware of potential vulnerabilities, such as unsalted hashes or weak encryption keys, to make informed decisions.
Developer-Centric Best Practices
Elevating Security with Salt
Introducing random data (salt) before hashing can drastically amplify password security by producing unique hashes, even for identical passwords.
| # Python example: bcrypt with salt salt = bcrypt.gensalt(12) hashed_with_salt = bcrypt.hashpw(password, salt) print(f“Salted Hash: {hashed_with_salt.decode()}”) |
Guarding the Encryption Keys
Developers must ensure encryption keys are securely stored, rotated periodically, and backed up. Managed services or hardware modules can simplify this task.
The Multi-factor Authentication (MFA) Advantage
Beyond just password protections, integrating MFA can significantly bolster security. By providing an additional verification layer, unauthorized access becomes exponentially harder.
Championing Strong Password Policies
A system is only as robust as its weakest password. Developers should ensure applications enforce stringent password guidelines—length, complexity, and unpredictability.
Conclusion
Securing passwords through hashing or encrypting is both a technical and ethical imperative. As the digital landscape becomes more intricate, so do its associated threats. Understanding encryption and hashing is essential, but comprehensive application security requires more. With Qwiet AI you can achieve that next-level protection tailored for the modern web. Prioritize your application’s defenses by booking a demo with us today, ensuring unwavering trust and reliability for your users.