Introduction
Diving into the depths of application development often reveals the lurking dangers of sensitive information exposure. Secure management of environment variables, often used to store secrets like API keys and credentials, becomes a pivotal practice in navigating these treacherous waters. In this deep dive, we will explore the intricacies, best practices, and common pitfalls in the secure management of environment variables from a developer’s standpoint.
Plumbing the Depths: The Silent Role of Environment Variables
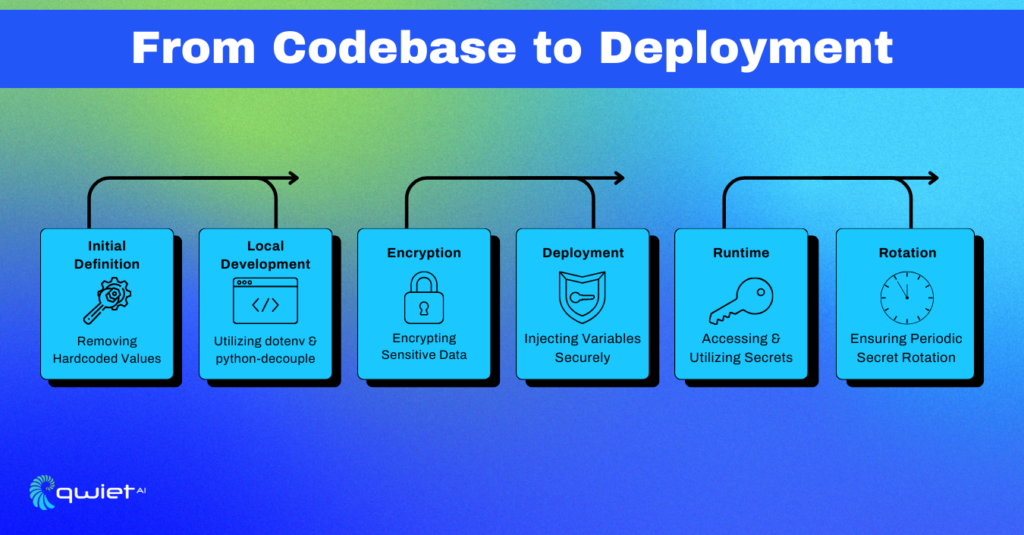
Environment variables act as a foundational pillar in the architecture of secure application development. They provide a structured mechanism to store and access sensitive data, such as API keys, database credentials, or other configuration settings that are crucial for the application’s operation. The principal advantage of using environment variables is the segregation of this sensitive data from the codebase, which is imperative for several reasons:
- Security: Storing secrets within the code or under version control is a significant security risk. If the codebase is accidentally shared or becomes public, the embedded secrets are exposed, leading to a potential security breach. Environment variables, on the other hand, remain on the server and are not exposed in the code, reducing the risk of exposure.
- Portability: Environment variables allow for a more portable setup since developers can easily change the environment the application runs in without modifying the code.
- Maintenance: It simplifies maintenance. When secrets are changed, there’s no need to alter the codebase; only the environment variables need updating.
Exploring the Abyss: The Paramount Importance of Secret Security
Say ‘No’ to Hard-Coding:
Hardcoding secrets within the code is akin to leaving your keys under the doormat. It’s an open invitation for security issues. When secrets are hard-coded, they become part of the codebase and can be exposed inadvertently through version control systems or by being shared publicly.
By segregating secrets from the code and placing them in environment variables, the risk of exposure is markedly reduced. The example below illustrates the preferred practice of segregating secrets from the code.
| // Avoid const API_KEY = ‘YOUR_API_KEY’; // Adopt const API_KEY = process.env.API_KEY; |
Secure Management with Variable Managers:
Tools such as dotenv for Node.js or python-decouple for Python are instrumental in facilitating the secure management of environment variables. They provide a structured and secure mechanism to load and access environment variables within the application, ensuring they are only accessible during the application’s runtime, thereby enhancing the security posture.
| from decouple import config API_KEY = config(‘API_KEY’) |
Enigma of Encryption:
Encryption adds a formidable layer of security by transforming the secrets into unreadable ciphertext. Before storing secrets, encrypting them ensures that even if there’s an unauthorized access, the exposed data remains incomprehensible without the decryption key. Demonstrating the encryption of an API key using a cipher and an encryption key, securely stored as an environment variable, epitomizes the augmentation of security measures.
Below demonstrates encrypting an API key using a cipher and an encryption key, which is also securely stored as an environment variable.
| from cryptography.fernet import Fernet cipher_suite = Fernet(os.environ.get(“ENCRYPTION_KEY”)) encrypted_api_key = cipher_suite.encrypt(b“Actual_API_KEY”) |
Probing Deeper: Additional Safeguards and Best Practices
Segregating the Depths: Separate Environments:
Segregating environments for development, testing, and production is a prudent practice. It ensures that each environment has its unique set of variables, preventing accidental overlap or misuse which could lead to configuration errors or exposure of sensitive data.
Safeguarding Access: Guarding the Precious:
Implementing stringent access control policies is essential to ensure that only authorized entities can access or modify environment variables. Employing audit logs provides a traceable record of every access and modification, which is invaluable for monitoring and investigating unauthorized access.
Guardian of Secrets: Employing Secret Management Solutions:
Utilizing secret management solutions like AWS Secrets Manager or HashiCorp Vault provides a centralized and secure hub for managing secrets. These tools not only offer secure storage but also enable fine-grained access control, audit logging, and automatic rotation of sensitive data, significantly elevating the security framework surrounding secret management.
In-depth Exploration: The Hidden Challenges of Managing Secrets
Balancing Act: Security vs. Usability:
Finding the right balance between strong security and easy use for developers is crucial. High security is needed to keep sensitive data safe, but if the system is too hard to use, developers might find workarounds that could weaken security.
The goal is to have a security system that is strong yet easy for developers to use. Solutions like user-friendly secret management systems with clear instructions can help maintain good security while ensuring usability.
Migration and Rotation Quandaries:
Moving to a new secret management system or updating (rotating) secrets can be complex tasks. They require a well-planned strategy to avoid service interruptions or accidental data exposure. When migrating, it’s important to carefully move all existing secrets to the new system and ensure every part of the application can access the secrets it needs.
Regularly updating secrets is also important to keep data safe. Through using automated tools like Qwiet and thorough testing in a controlled setting before full deployment can help manage these tasks more smoothly.
Compliance and Regulation Navigation:
There are many compliance requirements and regulations that dictate how secret management should be handled. It’s not just about following these rules, but understanding them and preparing for any changes in the regulations.
Working closely with legal and compliance experts, and using secret management systems with built-in compliance features, can help ensure that the secret management practices are always in line with the necessary regulations. This will help avoid any legal issues and keep the secret management system up to standard.
Conclusion
In the world of secret management, developers work to make sure applications run smoothly and keep important information safe. By not using hardcoding, working with variable managers, making data unreadable to unauthorized users, separating environments, following access rules, and using secret management tools, they help keep applications secure from risks. Navigating through secret management can be tricky, but with the right approaches, it can be done safely amidst digital hurdles. Looking to improve how you handle secret management? Schedule a call with our team to strengthen your application’s security.
