The Background
Cybercriminals are currently exploiting a vulnerability in the popular server administration tool Control Web Panel (CWP). This vulnerability allows for a fairly trivial remote code execution (RCE), requiring no authentication. A recent Shodan search shows over 426,000 servers currently running CWP (down from around 435,000 servers a couple days ago) around the globe.
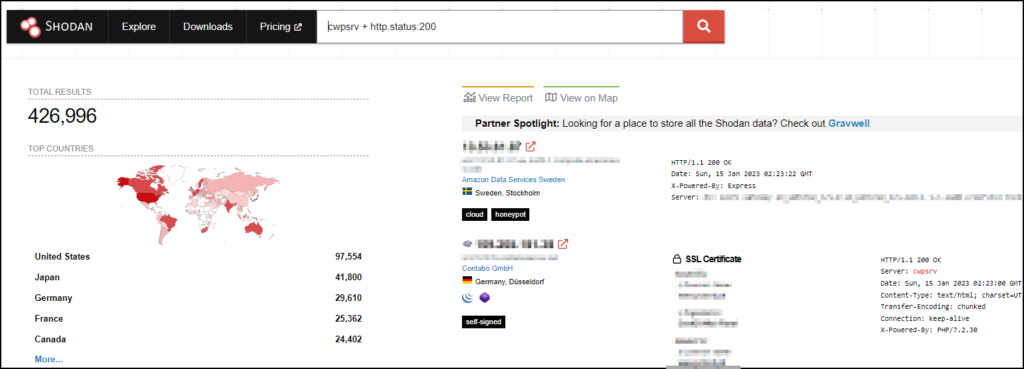
This vulnerability was actually discovered in July of 2022 by Numan Türle, a security engineer at Gais Security who discovered it during security testing on 3rd party applications used by their customers. CWP responded with a patch in 2 days to fix the affected versions, with a code fix later released in October. On Jan 3, 2023 CVE-2022-44877 for the vulnerability (severity score of 9.8 out of 10) was published including a proof of concept exploit and a video showing how it worked. While a sizable amount of time passed between disclosure, patch, and advisory, numbers of exploits of this vulnerability started increasing on Jan 7, 2023, an indication that many of the servers in the wild have not yet been patched for this vulnerability.
CVEs and Application Security Testing
Any exploit in the wild shows the need for robust application security testing. While creating after the fact detection rules for whatever flavor of intrusion detection/prevention tool you prefer (Network IPS, Next Gen Firewalls, EDR, etc…), these are all “after the fact” security measures. Ultimately these vulnerabilities are all the result of applications that were released with bugs in their code that allows them to be exploited. Application security testing is the closest we can get in the security industry to stopping these vulnerabilities from being released in the first place.
Of course even rigorous security testing can have its blindspots. Most application security testing tools rely on a combination of known vulnerabilities (typically based on CVEs) and heuristic detections to find the bugs that ultimately end up being exploited by cybercriminals. This incident is a prime example of one of the shortcomings in the Static Application Security Testing (SAST) space. The vulnerability existed long before a CVE was available, so if you are relying on a signature based approach that looks for known vulnerabilities, there was a solid 6 month gap where this insecure code was sitting out in the ether and would have gone unnoticed by most SAST tools. This is why a different approach is needed.
The Role of AI in Application Security Testing
We’re still in the relative infancy of AI, but if an AI can produce art, write essays, code, and of course, provide endpoint security protection, why can’t we utilize it to proactively look for vulnerabilities in code?
The biggest benefit to utilizing AI in SAST is speed. An AI-based scanner can analyze large amounts of code quickly and accurately, and detect patterns and anomalies that humans themselves might not be able to detect. AI can also be trained on known vulnerabilities and bugs to help them discover new vulnerabilities and “unknown unknowns”, improving their accuracy and efficiency.
Of course today, AI does require human guidance. Taking a look at the hands of most AI art serves as a good illustration of the need for human intervention. So while AI can serve as a force multiplier for detection, until it can collect a sufficient data corpus, human security analysts will be needed to validate the findings and ensure that AI isn’t creating a large amount of false positives. Of course the beauty of applying AI to code is that as the human analysts validate the findings, they can be fed back into the AI, ultimately improving the analysis and detection capabilities. This kind of reinforcement learning will be essential to training and building to the 99.9%+ accuracy needed to find broad commercial acceptance.
The Future of AI Powered SAST
The dwell time of the CWP vulnerability serves as a stark indicator that relying on known vulnerabilities (and even heuristics) isn’t enough to fully protect against the unknown. The SAST market will need to openly embrace AI as a method for quickly and accurately finding those zero day vulnerabilities. Of course AI detection will only be as good as the data it has to work with, so it’s of utmost importance to have the best and brightest security analysts and data scientists training the detection models. When the application security testing market embraces AI, we might see a shift from “zero day” to “pre zero” vulnerability detection.