Introduction
Dive into online security with a closer look at authentication and authorization. This article unravels how these key processes verify your identity and manage your access rights, acting as the frontline defenses for your data.
What are Authentication and Authorization?
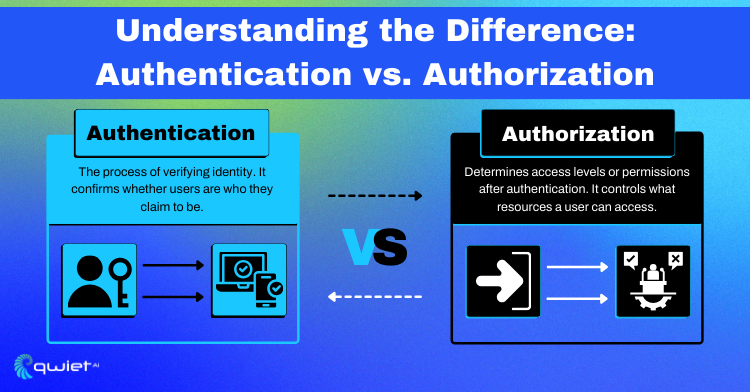
Authentication verifies a user’s identity with things like passwords or fingerprints. It’s about making sure you are who you say you are. Then, authorization decides what you can do or see after you’re authenticated. It’s about giving you the right access based on who you are.
These two steps are key for keeping apps safe. They work together to ensure only the right people can get in and do what they need to do, protecting everyone’s private information and preventing unauthorized access.
Principles of Authentication and Authorization
Identity Verification:
Identity verification is crucial for security. It uses specific methods like passwords, biometric scans (like fingerprints or facial recognition), or unique codes to confirm someone’s identity.
This step ensures that only authorized users can access an application or system. It’s a way to check that individuals are who they claim to be, providing a secure gateway before allowing any further interaction with the system.
Access Control:
Once identity is verified, access control comes into play. This process involves setting up rules defining what verified users can do within the application. It’s akin to determining which doors a user can open within a system, based on their role or status.
Access control ensures that users can only reach the information and features relevant to them, effectively managing who gets to see what or perform specific tasks. This layer of security helps to safeguard sensitive information from being accessed by unauthorized individuals.
Least Privilege:
The principle of least privilege is about limiting user access rights to the bare minimum necessary to complete their tasks. This approach minimizes potential risks by ensuring that users don’t have more access privileges than they need.
By applying this principle, organizations can significantly reduce the likelihood of malicious access or accidental misuse of information. It’s a strategy that tightens security by precisely controlling access levels, thus making the system safer for all users by preventing unnecessary exposure of sensitive data or critical functions.
Benefits of Effective Authentication and Authorization
Strengthened Security Posture:
Robust authentication and authorization mechanisms act as formidable barriers against cyber attacks. By verifying identities and controlling access to resources, these mechanisms fortify applications, making it harder for unauthorized users to breach security measures.
Regulatory Compliance:
Effective authentication and authorization practices are crucial for organizations to adhere to data protection and privacy laws. By implementing secure access controls and identity verification processes, organizations can ensure compliance with regulations, safeguard sensitive data, and maintain stakeholders’ trust.
Enhanced User Trust:
Secure authentication and authorization processes inspire confidence in users by demonstrating a commitment to protecting their information. When users know their data is being handled securely, they are more likely to trust the application and continue using its services.
Risk Mitigation:
Proper implementation of authentication and authorization significantly reduces the risk of data breaches and unauthorized access. By enforcing strict access controls and adhering to the principle of least privilege, organizations can mitigate potential risks, safeguarding against financial losses and reputational damage.
Key Practices in Authentication and Authorization
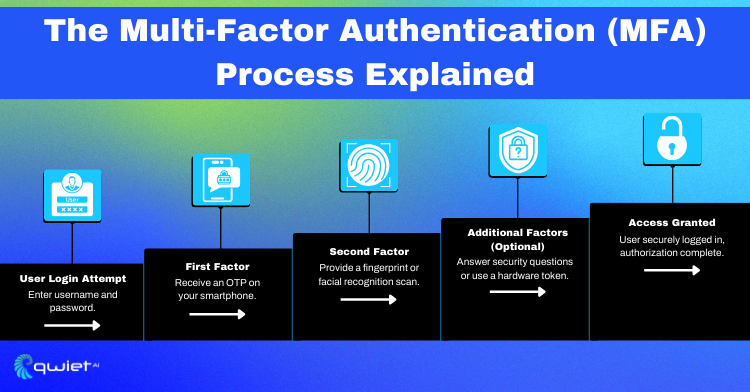
Multi-Factor Authentication (MFA):
MFA is essential for adding an extra layer of security beyond traditional passwords. By requiring users to provide multiple verification forms, such as passwords, biometric scans, or security tokens, MFA significantly reduces the risk of unauthorized access, enhancing overall security posture.
Role-Based Access Control (RBAC):
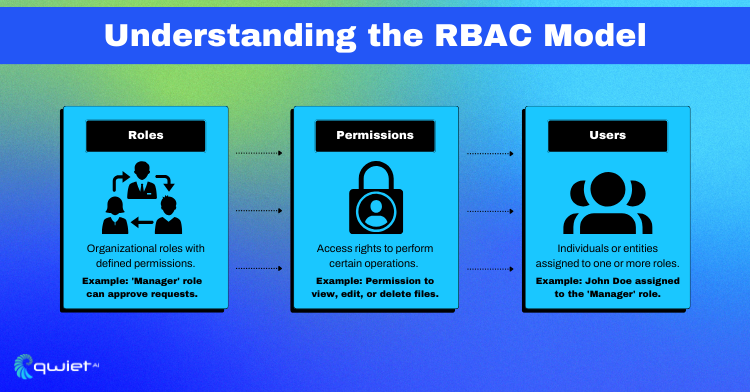
RBAC simplifies authorization by managing user permissions through predefined roles. By assigning specific roles to users based on their responsibilities or job functions, RBAC streamlines access control processes, ensuring that users only have access to the resources and functionalities necessary for their roles, thereby reducing the risk of misuse or unauthorized access.
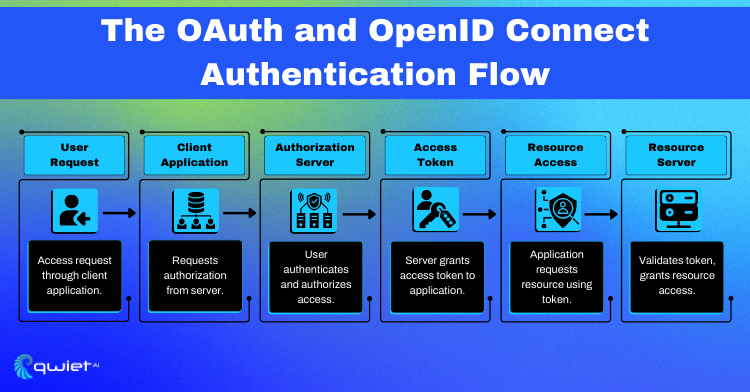
OAuth and OpenID Connect:
These standards provide secure, delegated access in modern applications. OAuth allows users to grant third-party applications limited access to resources without sharing their credentials, while OpenID Connect facilitates single sign-on authentication. Implementing OAuth and OpenID Connect enhances security by enabling secure resource access and simplifying user authentication processes.
Token-Based Authentication:
Token-based authentication mechanisms offer several benefits, including enhanced security and scalability. By issuing tokens to authenticated users, token-based authentication eliminates the need to store sensitive user credentials on servers, reducing the risk of credential theft. Additionally, tokens can be easily revoked or refreshed, improving security posture and mitigating the impact of security breaches.
Conclusion
Simply put, authentication and authorization are the keys to keeping online stuff safe. They check who’s who and keep everyone out of places they shouldn’t be. To make things even safer, using a tool that checks for security problems, like a Qwiet, is a smart move. Think of it as having an extra set of eyes to catch anything that might slip through. Curious to see how it works? Book a demo with us. Let’s make sure your online world is locked down tight.
