Introduction
Imagine clicking a link and unintentionally giving a cyber thief access to your data. This article dives into the silent threat of CSRF, where your trusted web session becomes a hacker’s tool. You’ll learn what CSRF is, how it operates, and how you can protect against its deceptive maneuvers.
What is Cross-Site Request Forgery (CSRF)?
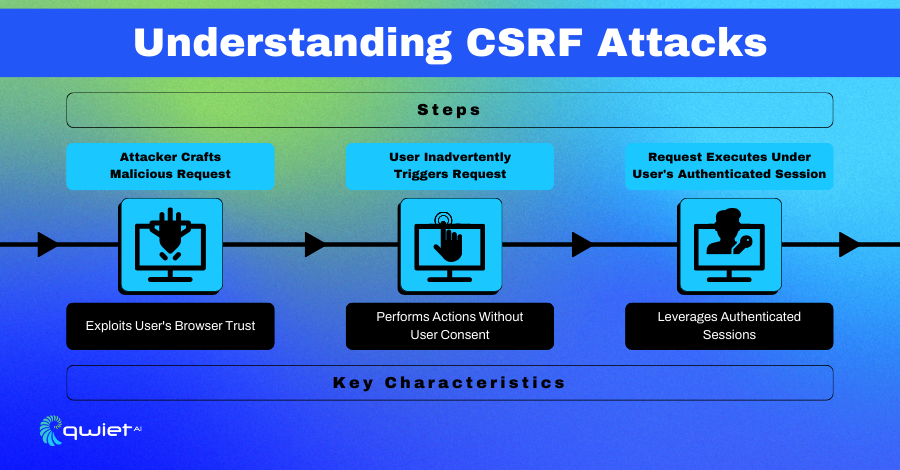
Cross-site request Forgery (CSRF) is a web security vulnerability that tricks users into executing unwanted actions on a web application where they are authenticated.
Unlike other attacks that rely on directly injecting malicious scripts, CSRF exploits the trust a web application has for the user’s browser. It deceives the web application into believing that its rogue actions come from the legitimate user, not the attacker.
CSRF attacks leverage authenticated sessions by sending unauthorized commands from the user to the application without the user’s knowledge. Imagine a scenario where a user is logged into their bank account; a CSRF attack could potentially submit a transaction request if the user clicks a link or loads an image from a malicious site.
Here is a simple code example that could be exploited via a CSRF attack:
| <!– A form on a bank website for transferring funds –> <form action=“http://bank.com/transfer” method=“POST”> <input type=“hidden” name=“amount” value=“1000”> <input type=“hidden” name=“account” value=“12345”> <input type=“submit” value=“Transfer Funds”> </form> |
This code snippet has a form for transferring funds on a banking website. If a user is authenticated and this form lacks CSRF protections (like a token), a similar form could be placed on an attacker’s site. When the user visits the attacker’s site, the form could be automatically submitted through JavaScript, causing the user to unwittingly perform a transfer on the legitimate bank site using their authentication credentials.
CSRF is distinct from other vulnerabilities like XSS, as it does not involve injecting malicious scripts into the web application. Instead, it sends legitimate requests without the user’s consent, exploiting the fact that the user has an active session with the application. This attack can be mitigated by implementing anti-CSRF tokens that validate the user’s intention to submit the request.
Core Components / Process Description of CSRF
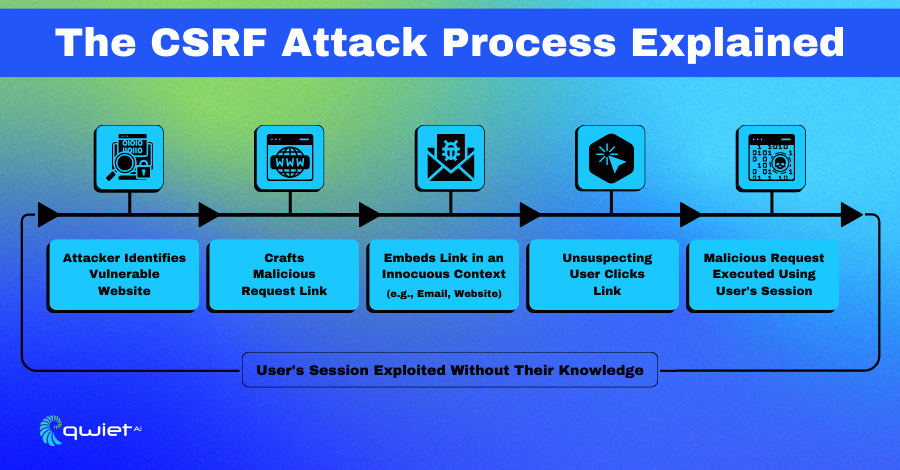
The anatomy of a CSRF attack lies in the exploitation of a web application’s trust in the user’s browser. By crafting malicious requests, attackers can deceive the browser into performing actions with the user’s authenticated session on another site. The CSRF attack hinges on three main conditions: a valid user session, a predictable and scriptable action, and the absence of robust anti-forgery measures.
Process of a CSRF Attack
- The Attacker Crafts the Malicious Request: This involves creating a URL or script that performs an action on the target website using the user’s current session. The attacker then embeds this request into an image tag, hidden form, or JavaScript triggered when the user visits a malicious site or clicks a malicious link.
- The Malicious Request is Triggered: When the victim navigates to the attacker’s controlled environment (such as a web page or an email), the malicious request is automatically sent to the target web application without the user’s conscious action.
- The Target Site Executes the Request: The user’s browser sends the request along with any authentication cookies to the target site, which may process the request as a legitimate action because it appears to come from the authenticated user.
Best Practices for CSRF Mitigation

To safeguard web applications from Cross-Site Request Forgery (CSRF) attacks, several proven strategies should be systematically implemented:
Anti-CSRF Tokens
Anti-CSRF tokens are the most effective measure against CSRF attacks. These random tokens are unique to each user session and verified for authenticity with every state-changing request. By embedding these tokens in web forms and validating them upon submission, applications can ensure that the request is genuine and initiated by the intended user.
Code Example
| # Generate an anti-CSRF token from secrets import token_hex token = token_hex(16) # Validate the token on form submission if form_token == session_token: # Process the request |
This code snippet generates a unique anti-CSRF token using Python’s secrets module and validates it during a form submission. The token ensures that the user makes every request intentionally, effectively preventing CSRF attacks by verifying each state-changing request’s authenticity.
Validate Request Origins
Validating the Origin or Referer HTTP headers is crucial when dealing with state-changing operations. These headers typically indicate the site from which the request originated. Checking these headers helps to confirm that requests to the server are coming from trusted and expected sources, adding another layer of security against CSRF.
Code Example
| # Validate the Origin header in an HTTP request origin = request.headers.get(‘Origin’) if origin not in allowed_origins: raise Exception(“Invalid origin”) |
This snippet checks the Origin header of an incoming HTTP request to ensure it’s coming from a trusted source. By verifying the origin of requests, especially for state-changing operations, the application adds an extra security layer against CSRF by ensuring that requests are made from allowed origins.
Strict Session Management
Adopting strict session management policies can significantly enhance security. Sensitivity or critical actions—like changing a password or making a transaction—require users to re-authenticate. This ensures the impact is limited even if a session has been hijacked and critical functions are protected.
Code Example
| # Re-authenticate before sensitive operations if not is_authenticated(session): # Prompt user re-authentication |
The code requires users to re-authenticate before performing sensitive or critical actions. This strict session management practice limits the damage that could be done if a session were hijacked, protecting important operations like password changes or transactions.
Leverage Framework Protections
Many modern web development frameworks have built-in CSRF defenses, including generating and validating anti-CSRF tokens, setting same-site cookie attributes, and more. Using these features is recommended rather than creating custom security measures, as they are tried and tested against common vulnerabilities.
Code Example
| # Using framework features for CSRF protection @app.before_request def check_csrf_token(): # Framework’s built-in method to validate CSRF token |
This example illustrates utilizing a web framework’s built-in CSRF protection features, such as generating and validating anti-CSRF tokens. Leveraging these tested and secure features provided by frameworks offers robust defense against CSRF attacks, avoiding the need for custom, potentially less secure solutions.
Conclusion
CSRF is a hidden danger in web security, turning routine actions into unintended commands. You can safeguard your online interactions by embracing strategies like anti-CSRF tokens and vigilant session management. Book a demo to see how Qwiet can help implement preventative methods to protect against CSRF in your codebase.
