 Introduction
Introduction
Have you ever wondered how your private info stays safe online? In a world where cyber threats are rising and we share more data than ever, data encryption is our digital guardian angel. This article will take you through how encryption works to protect your information and why it’s more important now than ever. You’ll learn the basics and how to apply the best practices to keep your data locked down tight.
What is Data Encryption?
Data encryption protects information by scrambling it into a code that only someone with the right key can read. It’s a bit like a secret language that keeps data safe from anyone who isn’t supposed to see it. This process helps keep personal details, financial information, and other important data hidden from hackers and cybercriminals.
The importance of encryption shows up in all the places where data lives. Whether it’s sitting on your computer, being sent over the internet, or being used by an app, encryption acts like a security guard.
It keeps your information private and ensures it doesn’t get changed or corrupted along the way. As we share more and more of our lives online, using encryption is like putting a lock on your personal information, giving you peace of mind that your digital stuff is well-protected.
Core Principles of Data Encryption
At the heart of data encryption are encryption algorithms, which are like complex math puzzles that scramble and unscramble data. These algorithms come in two main types:
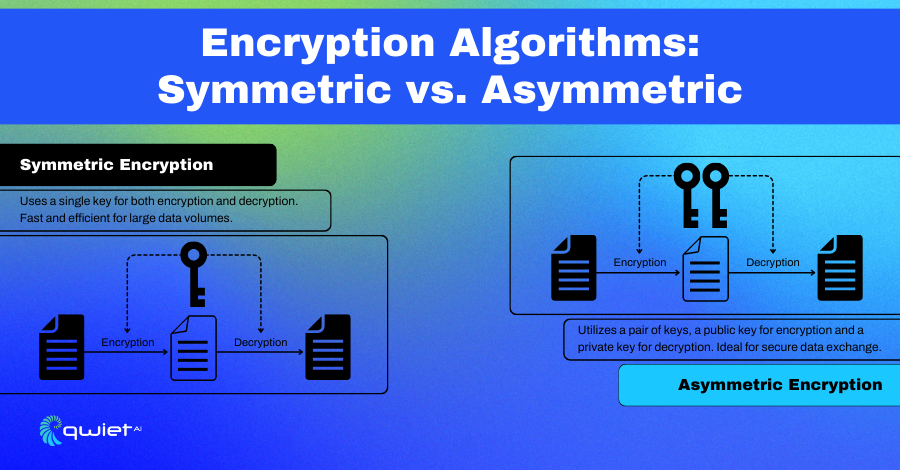
- Symmetric encryption uses one key for locking (encrypting) and unlocking (decrypting) the data.
- Asymmetric encryption: uses a pair of keys – one public key that anyone can see and use to lock the data and a private key that only the owner has to unlock.
This is a bit like a mailbox at the post office: anyone can drop a letter in (encrypt data with the public key), but only you can take it out with your unique key (decrypt with the private key).
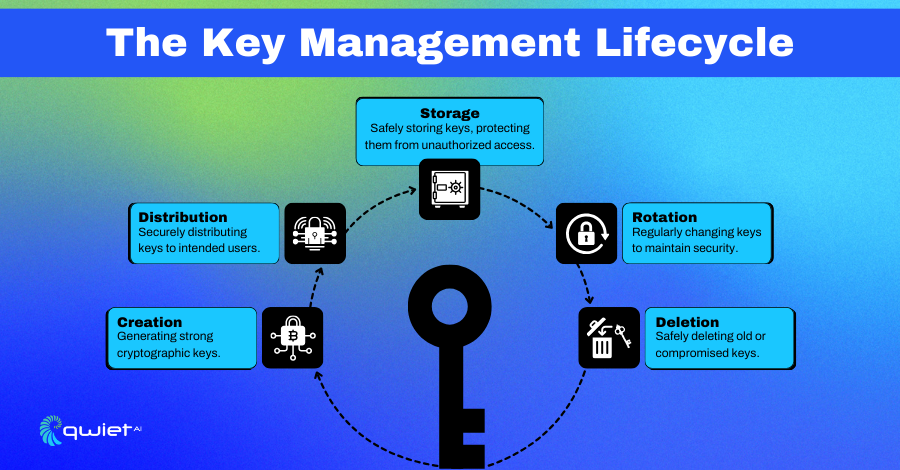
Key management is the art of handling these cryptographic keys. It’s crucial because the security of encrypted data is only as good as the security of the keys.
If keys are mishandled or fall into the wrong hands, it’s like giving a thief the keys to your house. That’s why managing keys securely – making sure they’re generated, stored, and destroyed properly – is a top priority in data encryption practices.
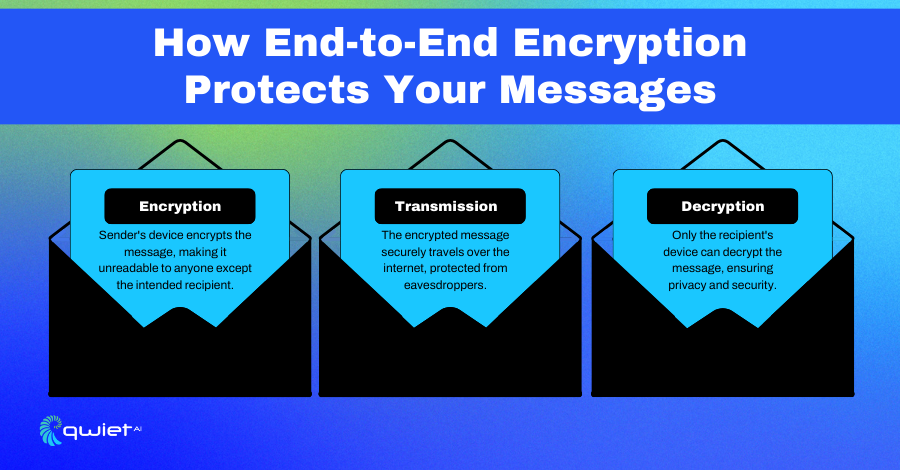
End-to-end encryption is the process where data is encrypted on the sender’s system and only decrypted on the recipient’s system. Imagine a conversation where the words turn into gibberish as soon as they leave the speaker’s mouth and only reassemble into something understandable in the listener’s ear.
That’s how end-to-end encryption works; it ensures that no matter where the data travels, it stays protected and unreadable to anyone snooping in between, from when it’s sent to when it’s received. This keeps private communications private, from texts and emails to video calls.
Benefits of Data Encryption
Protection of Sensitive Information: Encryption acts as a digital vault for sensitive information, safeguarding personal and financial details. It ensures that even if data falls into the wrong hands, it remains gibberish without the right key. Imagine your private information is a treasure, and encryption is the map that only you can read.
Compliance and Regulatory Adherence: By encrypting data, organizations can navigate the complex seas of data protection laws and regulations. It’s like a badge of honor showing they’re committed to protecting data, which keeps them clear of legal penalties and showcases their dedication to privacy.
Trust and Credibility: Customers value their security, and when companies use encryption, it’s a sign that they take that security seriously. It’s like a company promising that they’ll guard your secrets as if they were their own, strengthening customer relationships and building trust.
Mitigation of Data Breach Impact: In the event of a data breach, encryption minimizes the damage. Encrypted data is a locked door that keeps thieves out, even if they manage to break into the house. This not only protects individuals’ information but also helps maintain a company’s good standing, acting as a crucial damage control tool.
Best Practices in Data Encryption
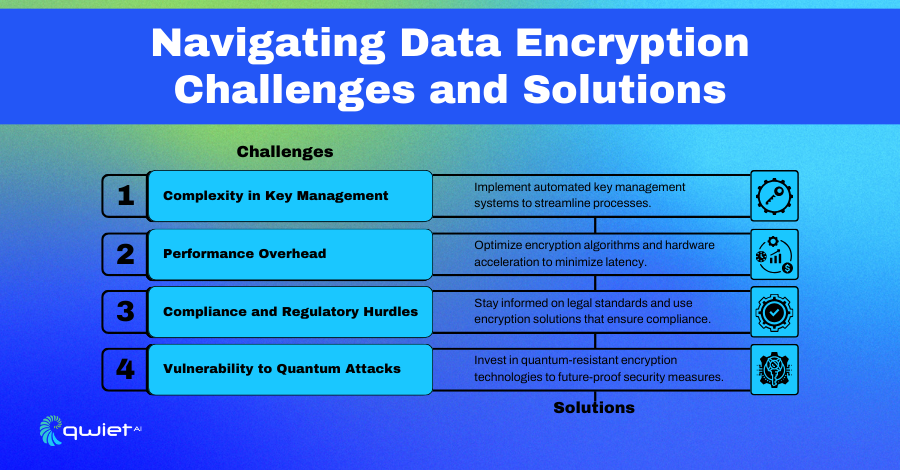
- Choosing Strong Encryption Standards: Just like you wouldn’t use a flimsy lock on your front door, it’s important to choose strong encryption standards to protect data. This involves selecting time-tested and robust encryption algorithms, which act as complex locks that only the right key can open. Following best practices in cryptographic security ensures the locks on your data remain unbreakable.
- Regular Key Rotation and Management: Encryption keys are like keys to a safe. Regularly changing these keys and keeping them in secure locations is crucial. Think of it as routinely changing your locks to stay ahead of lock-pickers. Periodic key rotation and secure management practices ensure that even if a key is somehow compromised, it won’t be useful for long.
- Data-at-Rest and Data-in-Transit Encryption: There are two types of data to protect: data-at-rest (like the money in your bank) and data-in-transit (like the money you send online). Using different strategies to secure both ensures that data is protected, whether in storage or moving across the internet. This is akin to having both a safe at home and a secure way to send money to someone else.
- Public Key Infrastructure (PKI): PKI is like the postal system for secure communications. It manages keys and digital certificates, ensuring that when you send a message, it can only be opened by the intended recipient with the right key. This infrastructure is essential for establishing and maintaining a high level of security in electronic communications.
Conclusion
We’ve seen how important data encryption is for securing our digital lives. It’s like having a secret code that only you and the intended recipient can understand, ensuring your private information stays that way. With cyber threats becoming more sophisticated, staying informed and using strong encryption practices is key.
Enhance your application’s security with Qwiet and protect your data through preventative measures, schedule a demo to learn more.