Introduction
Have you ever wondered how safe your code is in a world full of digital threats? This article dives into the world of secure coding, revealing how it’s essential for keeping software safe from cyber threats. Learn why secure coding matters and how it fits into every stage of software development to protect against data theft and ensure your application works exactly as it should.
What is Secure Coding?
Secure coding is the practice of writing software to guard against the introduction of security vulnerabilities. Its primary goals are to protect data from theft or corruption and ensure that applications operate as intended. This approach is critical in developing applications that can withstand attacks and function securely.
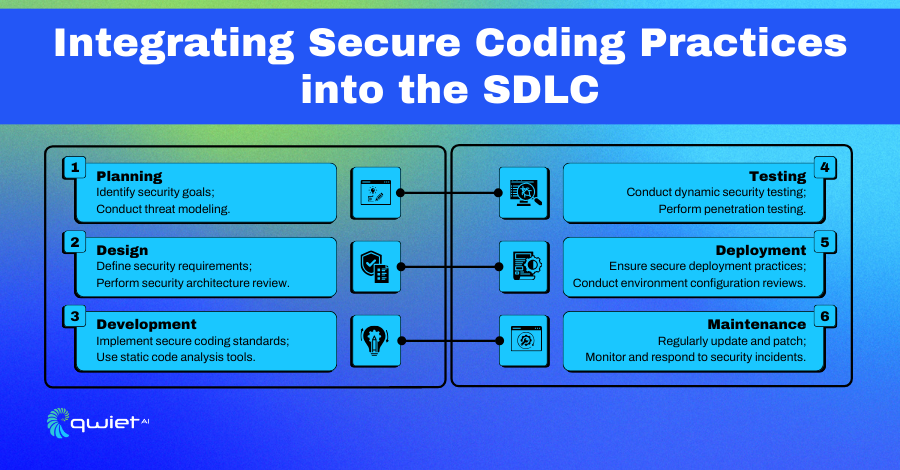
Within the Software Development Life Cycle (SDLC), secure coding is integral, woven into every phase from design to deployment. By incorporating security considerations early and throughout the SDLC, teams can identify and mitigate risks more effectively, ensuring that security is not an afterthought but a foundational component of software development.
Principles of Secure Coding
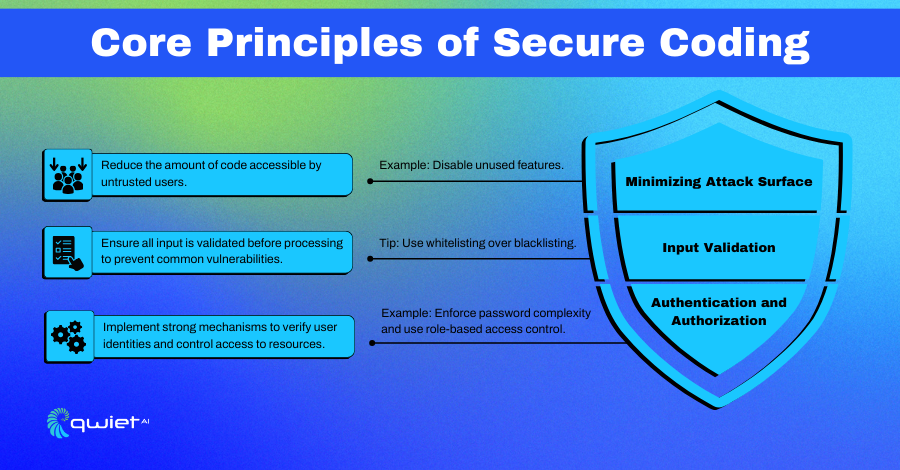
Minimizing Attack Surface:
This principle involves crafting your codebase to limit the parts that attackers could exploit. Strategies include removing unnecessary features, disabling unused services, and restricting access to the software’s components. Such practices help in creating a tighter, more secure application environment.
Input Validation:
Ensuring all external data the application receives is checked, validated, and sanitized is crucial. This step is fundamental in preventing attacks like SQL injection and cross-site scripting (XSS), which exploit input vulnerabilities to compromise data or hijack user sessions. A rigorous input validation routine is the first defense against such threats.
Authentication and Authorization:
Strong authentication and authorization mechanisms are essential for controlling access to sensitive data and application functions. Authentication verifies user identities, while authorization ensures they can only access what they’re permitted to. Together, they form a robust barrier protecting user data and application integrity.
Key Practices in Secure Coding
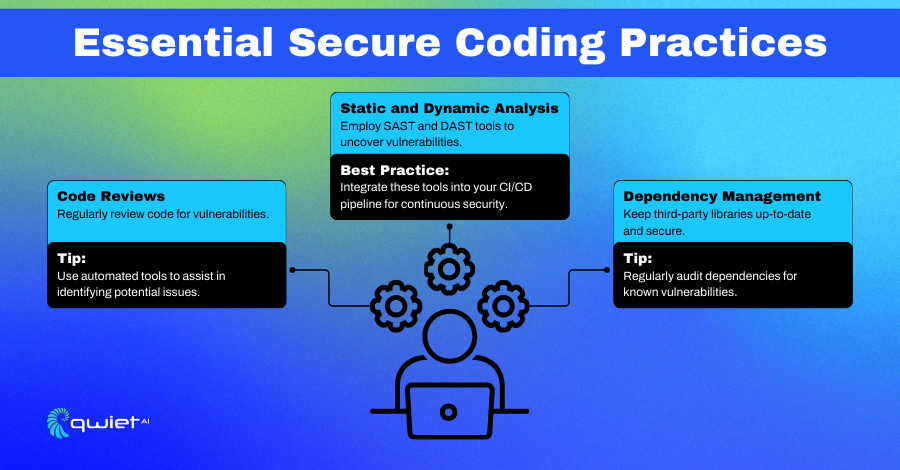
Code Reviews:
Code reviews are a cornerstone of secure coding practices. They involve meticulously examining written code by one or more developers to spot and correct security vulnerabilities before the software is deployed. This collaborative process helps identify potential security issues early and fosters knowledge sharing and adherence to coding standards, significantly enhancing the software’s security posture.
Static and Dynamic Analysis:
Developers leverage tools for static application security testing (SAST) and dynamic application security testing (DAST) to bolster security further. SAST tools analyze source code at rest to detect vulnerabilities without running the program, while DAST tools test the application during runtime to identify security flaws.
Together, they provide a comprehensive view of the application’s security health, enabling developers to detect and rectify potential threats efficiently.
Dependency Management:
In today’s development environment, relying on third-party libraries and dependencies is common practice. However, these external components can introduce security vulnerabilities if not properly managed.
Effective dependency management includes regularly updating libraries, using trusted sources, and auditing dependencies for known security issues. This proactive approach ensures that the software remains secure against vulnerabilities from its external dependencies.
Common Challenges in Secure Coding
Keeping Up with Emerging Threats:
One of the most significant challenges in secure coding is the rapid evolution of cyber threats. Hackers continually devise new methods to exploit vulnerabilities, making it important for developers to stay informed about the latest security risks. This dynamic landscape requires constant vigilance and adaptation of security practices to protect against novel attacks.
Integration into Agile and DevOps:
Incorporating secure coding practices into fast-paced Agile and DevOps environments can be challenging. These methodologies emphasize speed and efficiency, sometimes at the expense of thorough security measures.
Finding a balance between rapid development cycles and the need for comprehensive security assessments is essential. It involves integrating security checks and tests into the continuous integration and delivery pipelines to ensure that security is maintained without sacrificing speed.
Education and Training:
A consistent challenge in secure coding is ensuring all developers have the knowledge and skills to implement security best practices. The complexity of security concepts and the constantly changing threat landscape make continuous education and training imperative.
Organizations must prioritize security awareness and provide developers with the resources and tools to code securely, fostering a culture where security is a shared responsibility.
Conclusion
We’ve covered the nuts and bolts of secure coding, from its key principles to overcoming new cyber threats and integrating security in fast-paced development environments. Secure coding is important for any developer looking to protect their work. If you’re ready to take your application security to the next level, see how Qwiet can help. Book a call with us today to see how you can secure your application.