Introduction
How does a website recall your digital footprints during each visit? This article dives into session management, the silent guardian of web navigation, ensuring our virtual moves are remembered and protected. You’ll be equipped with essential insights on maintaining secure and fluid online experiences through robust session management practices.
What is Session Management?
Cross-Site Request Forgery (CSRF) is a security flaw that lets attackers force end users to execute unintended actions on a web application where they are currently authenticated. It is a treacherous exploit that takes advantage of an application’s trust in the user’s browser, allowing the attacker to issue commands to the application that appear to be legitimate requests fro
m the user.
A CSRF attack manipulates a user’s authenticated session to perform actions without their knowledge or consent. For instance, if a user is logged into their social media account, a CSRF attack could silently post a status or send messages to the user while they visit a malicious website.
This differs from other web vulnerability types, like XSS, because CSRF does not involve injecting malicious code into the web application. Instead, it hijacks the user’s browser to perform actions on the web application, exploiting the existing authenticated session.
CSRF Code Example:
| <!– This is a malicious website’s HTML which targets a bank’s fund transfer service –> <img src=“http://bank.com/transfer?amount=1500&toAccount=attacker” width=“0” height=“0” border=“0”> |
In the code above, an image tag is used to craft a GET request to the bank’s fund transfer URL. The user who visits the malicious website doesn’t see anything because the image dimensions are set to zero. However, suppose the user has already authenticated with their bank.
In that case, the browser will attempt to load the image by making a GET request, inadvertently executing a fund transfer to the attacker’s account.
This type of attack exploits the fact that the browser automatically sends along any cookies associated with the bank’s domain, including the user’s session cookie.
The bank’s server may interpret this request as a legitimate transaction initiated by the user because it would come with the user’s credentials.
It demonstrates how CSRF can leverage the authenticated state to conduct unauthorized actions. Protecting against CSRF requires measures such as anti-CSRF tokens, which ensure that the request is being made intentionally by the user, not by a third party.
Core Components / Process Description of Session Management
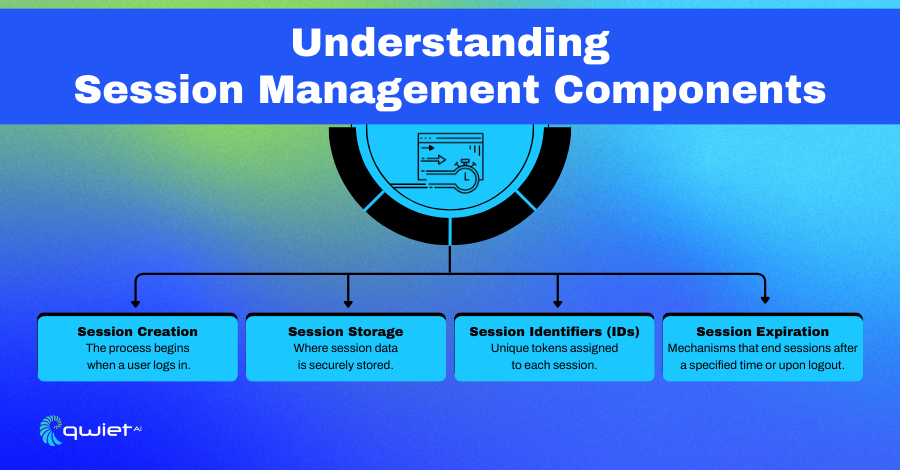
Session management is integral to maintaining a secure and efficient user experience on the web. It encompasses several key elements that work together to track users’ activities across web applications from when they log in to when they log out.
Session Creation
When a user logs into a web application, a session is created. This is the process where the server generates a unique session identifier (ID) for the user’s interactions. This session ID is usually stored in the user’s browser, often in a cookie, and sent with each subsequent request to the server. This way, the server recognizes the requests from the same user.
Session Storage
The server must store session data to maintain the state between stateless HTTP requests. This can be done in various locations: on the server, in a database, or memory caches like Redis. The data associated with a session ID will contain relevant user information and any state related to the user’s interactions.
Session Identifiers (IDs)
A session ID is a unique string assigned to a user during session creation. To prevent attackers from guessing or predicting an ID, which can lead to session hijacking, these IDs must be generated using secure, random methods.
Session Expiration
Sessions can’t last forever; they must expire to prevent unauthorized access from an abandoned session. Session expiration can be based on a timeout period of inactivity or a fixed time limit since the session was initiated. When a session expires, the server will no longer recognize the session ID, and the user must log in again.
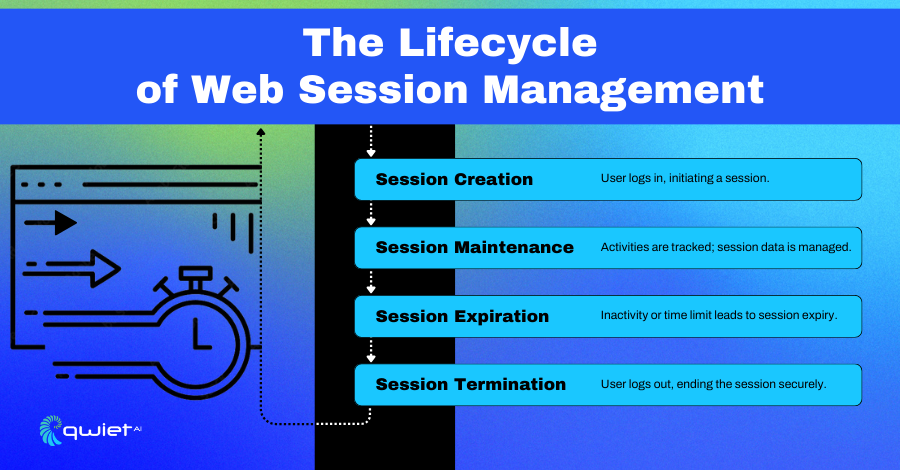
Process Flow of Session Management
- Session Initiation: A user enters their credentials into a login form. Upon successful authentication, the server generates a new session ID for that user.
- Session Tracking: As the user navigates the application, their session ID is sent along with every request to the server. The server uses this ID to retrieve the stored session data and maintain the user’s state across the web application.
- Session Handling: Any changes the user makes, such as updating preferences or adding items to a shopping cart, are recorded in the session data.
- Session Protection: Throughout this process, the session ID must be protected from interception (using secure transmission like HTTPS) and from other attacks like fixation, hijacking, or XSS.
- Session Termination: When the user logs out, the session is terminated. The session ID is invalidated on the server, and the session data is either deleted immediately or marked for deletion. Instructing the user’s browser to delete the session cookie is also best practice.
Good session management ensures a secure and seamless user experience, preventing unauthorized access and data loss. It is critical to uphold both security and usability in web application interactions.
Session Management Best Practices
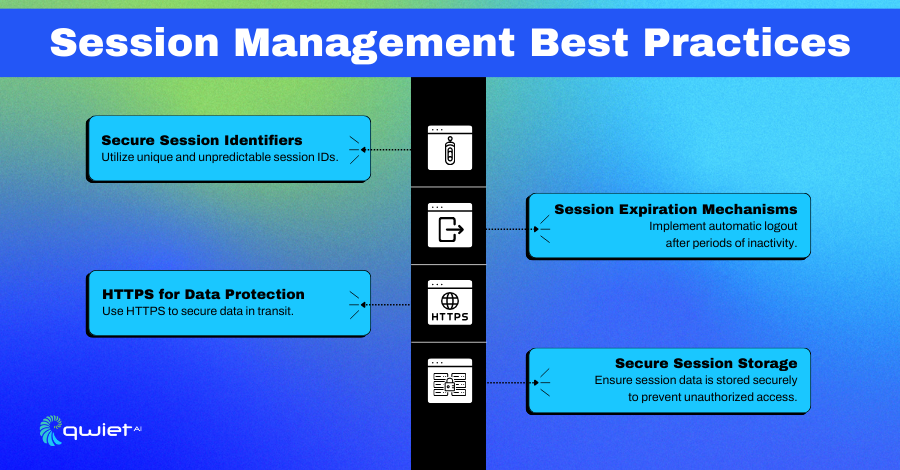
When managing user sessions securely, several critical best practices must be adopted to ensure the integrity and confidentiality of session data both in transit and at rest.
Secure Session Identifiers
A robust session management system begins with secure, unique session identifiers (IDs). These IDs should be generated using a secure random number generator that is sufficiently long to prevent brute-force attacks. The unpredictability of session IDs is crucial in preventing session hijacking and replay attacks.
Code Sample
| # Generating a secure, unique session ID in Python
import os |
This code snippet demonstrates generating a secure and unique session identifier (ID) using Python’s os.urandom function, which provides a secure way to generate random numbers. The generated session ID is unpredictable, making it difficult for attackers to guess, thereby preventing session hijacking and replay attacks.
HTTPS for Data Protection
HTTPS is vital for protecting session data as it travels across the network. Encrypting the data contained in the session, particularly the session ID mitigates the risk of man-in-the-middle attacks and eavesdropping. It also ensures that the session tokens are only visible to the end user and the web application, keeping them hidden from any third parties.
Code Sample
| # Enforce HTTPS in a Flask app from flask import Flask, redirect, request app = Flask(__name__) @app.before_request def before_request(): if not request.is_secure: url = request.url.replace(“http://”, “https://”, 1) return redirect(url) |
This snippet shows how to enforce HTTPS in a Flask application to protect session data during transit. It redirects any HTTP requests to HTTPS, encrypting the data and safeguarding it against eavesdropping and man-in-the-middle attacks, ensuring session tokens are secure.
Session Expiration Mechanisms
Implementing automatic logout or session expiration mechanisms can significantly improve security. Sessions should have a fixed lifetime and expire after a period of inactivity. This minimizes the window of opportunity for an attacker to use an old session token to gain unauthorized access.
Code Sample
| # Session expiration mechanism in Flask Python from flask import session, app @app.before_request def before_request(): session.permanent = True app.permanent_session_lifetime = timedelta(minutes=30) |
Here, we implement a session expiration mechanism in a Flask app, setting the session to expire after 30 minutes of inactivity. This reduces the risk of unauthorized access by limiting an attacker’s time to exploit an old session token.
Secure Session Storage
Secure session storage is paramount. It’s important to store session data securely to prevent unauthorized access. This can be achieved through encryption or secure, hardened storage systems. The session store should also be regularly backed up and protected from data loss.
Code Sample
| # Secure session storage example from flask import Flask from flask_session import Session app = Flask(__name__) # Configuration for secure session storage app.config[“SESSION_TYPE”] = “filesystem” app.config[“SESSION_FILE_DIR”] = “/path/to/secure/location” app.config[“SESSION_PERMANENT”] = False app.config[“SESSION_USE_SIGNER”] = True Session(app) |
This code configures a Flask application to store session data securely on the filesystem in a specified secure location. It uses session signing to protect the session data further, enhancing security against unauthorized access and ensuring that it is kept private and secure.
Conclusion
Session management is key to keeping web interactions both user-friendly and secure. It’s essential to handle sessions carefully to secure your application. If you are a developer wanting to boost your application security, book a demo to see how Qwiet can help fortify your codebase from beginning to end.