Are your Docker containers as secure as they should be? In this article, we delve into Docker and containerization, underscoring the paramount importance of security in this increasingly container-reliant era. By exploring best practices and common challenges, this piece equips you with the essential knowledge to safeguard your Docker environments against looming threats.
Understanding Docker and Containerization
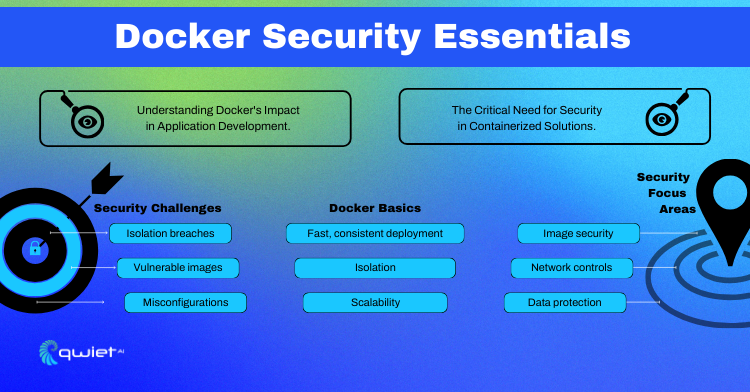
Docker stands as a cornerstone in the contemporary world of application development. It simplifies creating, deploying, and running applications by utilizing containers. These containers allow developers to package an application with all its dependencies into a single unit, ensuring it runs seamlessly across any environment. But with the convenience of containerization comes the critical need for security. In a Docker environment, security is not just an add-on; it’s an essential aspect that safeguards applications from emerging threats.
Basics of Docker and Container Technology
Docker containers operate on the principle of isolating applications from the host system. This isolation ensures that each container has its resources, including libraries and runtime environments, making it lightweight and efficient. However, this isolation also brings unique security challenges. Ensuring the security of containerized environments means understanding how Docker functions and the nature of threats specific to container technology.
The Necessity of Security in a Docker Environment
In Docker environments, security is paramount due to the shared nature of resources. A single vulnerability in a container can jeopardize the entire system. Therefore, adopting a proactive approach to security is essential. Understanding the architecture of Docker and how containers interact with the host and each other lays the foundation for a secure containerized environment.
Fundamentals of Application Security (AppSec) in Docker
Application Security (AppSec) in Docker involves a set of practices and tools designed to identify and mitigate security risks at the application level. These practices are essential in Docker environments, as containers often house critical applications exposed to various security threats.
In Docker, AppSec takes a specific approach, focusing on container images, the orchestration of containers, and network security. Ensuring that container images are free from vulnerabilities, managing how containers are deployed and communicated, and securing the network channels through which containers interact are key aspects of AppSec in Docker.
Docker Security Best Practices
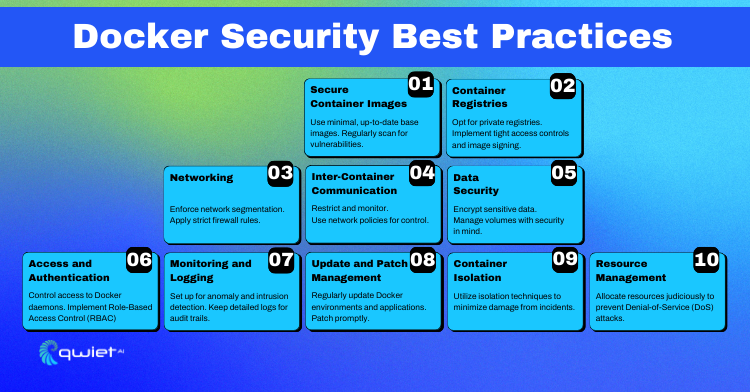
Several best practices must be followed to maintain a robust security posture in Docker environments—from securing container images to monitoring and logging activities within the Docker ecosystem.
Securing Container Images
Creating secure container images is the first step towards a secure Docker environment. This involves using minimal and secure base images and regularly scanning these images for vulnerabilities.
Creating Minimal and Secure Base Images
The choice of base image is a critical first step in securing your Docker environment. By opting for a minimal base image, you significantly reduce the attack surface of your application. This is because minimal images include only the essential packages and libraries required to run your application, leaving out unnecessary components attackers could exploit.
For instance, images like Alpine Linux are popular due to their minimal footprint. When creating your Docker images, removing any temporary files or unnecessary layers that could add vulnerabilities is essential.
Regularly Scanning Images for Vulnerabilities
Regular vulnerability scanning of Docker images is a proactive measure to identify and remediate potential security issues before they are exploited. Integrating vulnerability scanning into your continuous integration and deployment (CI/CD) pipeline ensures that every image is checked for vulnerabilities before deployment.
Tools like Trivy, Clair, or Docker Bench can be used for this purpose. These tools can scan for vulnerabilities in the operating system packages and the application dependencies, offering a comprehensive view of the potential security risks.
Managing Container Registries
Employing private Docker registries, like Harbor, AWS Elastic Container Registry (ECR), or Azure Container Registry (ACR), provides greater control over your container images. These private registries enable you to manage who can push or pull images, ensuring only authorized, vetted images are used in your environment.
This control is crucial for maintaining the integrity of your Docker images and preventing the introduction of potentially harmful third-party images. Additionally, private registries often provide additional security features, such as vulnerability scanning, access logs, and integration with your organization’s identity management systems.
For example, if you look at the command below:
| aws ecr create-repository –repository-name myapp-repo |
This AWS CLI command creates a new repository named myapp-repo in AWS ECR, illustrating how to set up a private registry in a cloud environment. Once the repository is created, you can push your Docker images to it, ensuring they are stored securely and accessible only to authorized users within your organization.
Using Private Registries for Control Over Images
Private registries offer better control over the container images. Organizations can ensure that only authorized images are used in their Docker environments by hosting images in a private registry.
Implementing Access Controls and Image Signing
Access control mechanisms restrict who can push and pull images from the registry. Image signing provides an additional layer of security by ensuring that only images signed by trusted sources are used.
Secure Networking Practices
In Docker, it’s crucial to manage network segmentation to control how containers communicate with each other and the outside world. By dividing the Docker network into smaller segments and applying specific firewall rules to each, you can limit the potential damage caused by a compromised container.
This reduces the risk of lateral movement in the event of a breach. Docker allows you to create custom networks and apply rules that govern inter-container communication, effectively isolating parts of your application for enhanced security.
| docker network create –driver bridge isolated_network docker run –network=isolated_network myapp |
This snippet demonstrates creating a custom Docker network named isolated_network using the bridge driver. A container running the myapp image is then started on this network. Containers on isolated_network can only communicate with each other unless specifically configured otherwise, providing a layer of isolation and security.
Limiting Inter-Container Communication
Limiting communication between containers is crucial in minimizing the impact of a compromised container. Docker’s network policies allow you to control traffic flow between containers, ensuring they only communicate as necessary.
For instance, a frontend container should not be able to directly communicate with a database container if it’s not required. Implementing these policies helps create a tightly controlled network environment where the risk of a breach spreading across containers is minimized.
Data Security in Docker
Data security in Docker involves protecting data both at rest and in transit. Encrypting data ensures its confidentiality and integrity, even if an unauthorized party accesses it. Docker volumes should be managed carefully to safeguard sensitive data.
Persistent data storage, which Docker volumes facilitate, allows data to be stored independently of container lifecycles. When using Docker volumes, it’s important to consider encryption options and to regularly back up critical data to prevent data loss and ensure data integrity.
Understanding Common Security Challenges in Docker
Here are some of the most common security challenges developers should know when configuring and maintaining docker containers:
Insecure Handling of Secrets
| ENV API_KEY=‘your-api-key’ |
Storing sensitive information like API keys or passwords directly in the Dockerfile or in environment variables can lead to security vulnerabilities. This information can be easily extracted from the image or seen by anyone accessing the Dockerfile or the running container.
Improper Network Configuration
| services: webapp: ports: – “0.0.0.0:5000:5000″ |
Binding the application to 0.0.0.0 exposes it on all network interfaces, including potentially unsecured external networks. This could allow unauthorized access to the application.
Running Containers as Root
| FROM ubuntu RUN apt-get update && apt-get install -y nginx EXPOSE 80 CMD [“nginx”, “-g”, “daemon off;”] |
By default, many Docker containers run as the root user. If an attacker gains access to the container, they could have root privileges on the container, potentially leading to severe security issues.
Using Outdated Images
Using an outdated or no longer supported base image can introduce vulnerabilities. Older images might not have the latest security patches, making them susceptible to attacks.
Including Unnecessary Packages in Images
| FROM node:latest RUN apt-get install -y python3 python3-pip python3-dev build-essential |
Installing unnecessary packages increases the attack surface, especially in a base image that does not require them. Every additional package could contain vulnerabilities or become a vector for an attack.
Hardcoded Credentials
| database_password = “password123” |
Hardcoding credentials in the code or Dockerfile can lead to severe security breaches, as these credentials can be easily extracted and misused.
Unrestricted Inter-Container Communication
| services: db: image: mysql app: image: myapp links: – db |
Allowing unrestricted communication between containers can lead to security risks, especially if one of the containers is compromised. Attackers could exploit this to gain access to other containers.
Insecure Volume Permissions
| volumes: – type: bind source: ./data target: /var/app/data read_only: false |
Mounting host directories without read_only set to true can lead to security risks, especially if the application within the container is compromised. This could give attackers access to the host filesystem.
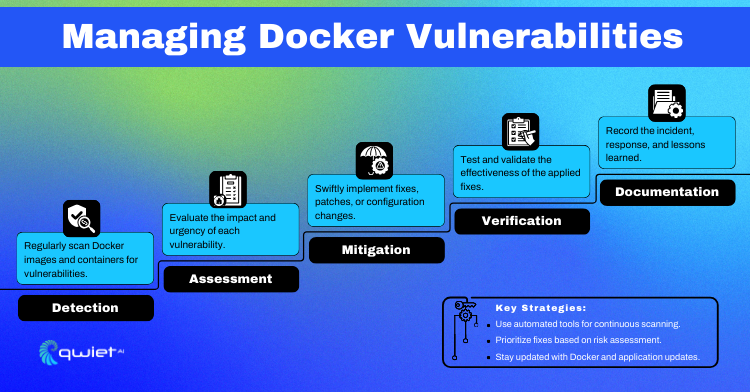
Conclusion
we’ve traversed the vital terrain of Docker security, from securing container images to mastering network segmentation and addressing common security pitfalls. These practices are pivotal for the integrity and safety of Docker environments. Remember, the landscape of threats is continually evolving; staying informed and adaptable is key to enduring protection.
For help identifying these security threats, book a demo with our team to see how Qwiet can help secure your development process.