What is Access Control?

Access Control is all about managing who can access specific data, systems, and resources within an organization. It uses structured mechanisms to regulate and restrict access, ensuring only authorized individuals or systems can interact with sensitive resources. To achieve this, organizations use different types of Access Control, such as Role-Based Access Control (RBAC), where access is granted based on a person’s role; attribute-based Access Control (ABAC), which considers specific user or resource attributes; Discretionary Access Control (DAC), where access is defined by the owner of the resource, and Mandatory Access Control (MAC), which enforces strict policies for highly secure environments. These methods provide flexibility and security to protect resources while allowing appropriate access.
Why Does Access Control Matter?
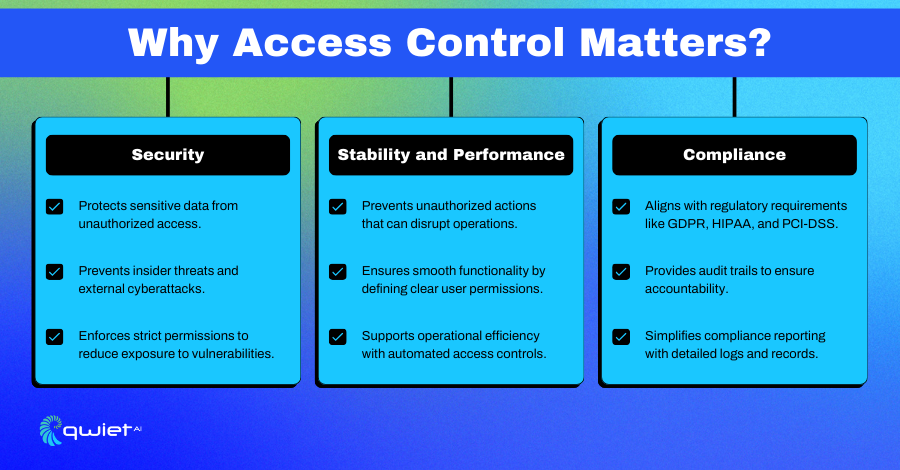
Security
Access Control is like a gatekeeper for your organization’s most sensitive data and resources. It ensures that only the right people have access, keeping unauthorized users, internal or external out of places they shouldn’t be. This reduces the chances of insider threats, data breaches, or cyberattacks. Giving users access only to what they truly need lowers the risk of exploitation and protects your organization from unnecessary vulnerabilities.
Stability & Performance
When access is clearly defined, everything runs more smoothly. Unauthorized actions, whether accidental or malicious, can disrupt operations or damage critical systems, but strong access controls stop those issues before they happen.
It’s not just about preventing harm; it’s about creating an environment where users can do their work without delays or interruptions, with permissions tailored to their needs. This clarity and control help keep systems stable and performing as they should.
Compliance
Staying compliant with regulations like GDPR, HIPAA, or SOX can feel overwhelming, but Access Control makes it much more manageable. With well-defined access policies, you’re automatically following many of the rules these regulations require.
Plus, having a detailed log of who accessed data and when makes audits and investigations far simpler; it’s a practical way to handle the complexities of compliance while keeping your systems secure and your operations transparent.
Components of Access Control

Authentication Methods
Authentication methods verify that the person or system requesting access is who they claim to be. This can be as simple as entering a password or as advanced as using biometrics like fingerprints or facial recognition. Multi-factor authentication (MFA) adds another layer of security by requiring more than one verification method, such as a password and a one-time code. Single Sign-On (SSO) makes things easier by allowing users to log in once and access multiple systems securely, reducing the need for juggling multiple passwords.
Authorization Models
Authorization models decide what a user can do once authenticated:
- Role-Based Access Control (RBAC) assigns permissions based on a user’s role in the organization, like manager or developer.
- Attribute-Based Access Control (ABAC) looks at specific details, such as the user’s department, location, or the type of resource they’re accessing, to decide permissions.
- Policy-based access Control (PBAC) takes things further by applying organizational rules dynamically adapting access based on conditions like time, device, or risk level. Together, these models create a flexible and secure way to manage access.
Access Management Policies
Access management policies clearly define who can access resources, under what conditions, and for how long. Tools like Identity and Access Management (IAM) systems help automate these policies, making it easier to enforce them consistently. But policies shouldn’t stay static. Regular reviews and updates are important to reflect changes in user roles, job functions, or security needs. This keeps access permissions relevant and minimizes potential risks over time.
Monitoring & Auditing
Access control doesn’t stop once permissions are set. Continuous monitoring tracks who’s accessing what and flags unusual activity. Logging all access attempts, changes, and actions creates a clear record that can be reviewed if there’s ever a question or problem. Regular audits of these logs help identify compliance gaps or potential security weaknesses, allowing you to fix them before they become bigger issues. Monitoring and auditing are about staying proactive and informed to keep systems secure.
Conclusion
Access Control is key to securing your systems and staying compliant. It limits access to sensitive data and resources, prevents unauthorized actions, and keeps operations running smoothly. With strong authentication, clear policies, and regular monitoring, you can reduce risks and adapt to changing needs. A secure app starts with strong Access Control, but vulnerabilities in code can undermine it. Qwiet AI helps by identifying weak spots in your code that could be exploited. Sign up for a demo with Qwiet AI today to see how it can protect your critical resources.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com