Key Takeaways
- Automated Compliance: AI-driven security policy enforcement ensures adherence to industry regulations and internal security protocols.
- Real-Time Threat Mitigation: AI continuously monitors for policy violations and security risks.
- Seamless Integration: Works within DevSecOps workflows to enforce security without disrupting development.
What is AI-Powered Security Policy Enforcement?
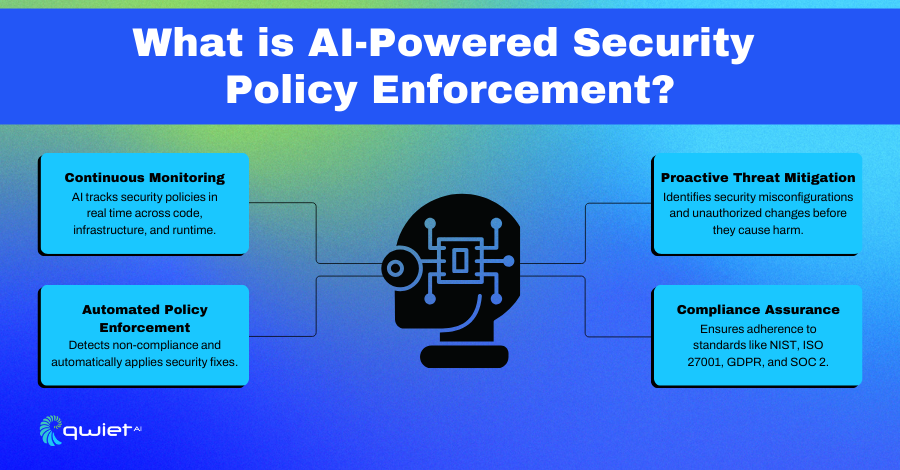
AI-powered security policy enforcement helps teams automatically apply and manage security policies across development, deployment, and operations. Instead of relying on manual reviews or static rule sets, AI continuously monitors systems, detects policy violations, and takes action in real time. It adapts as new threats emerge, making security enforcement more flexible and responsive.
Traditional security policies often create bottlenecks, leaving room for misconfigurations and human error. AI removes that friction by catching security gaps early and preventing unauthorized changes before they cause problems. Since it works alongside development workflows, it keeps security in check without hindering productivity.
Why Does AI-Powered Security Policy Enforcement Matter?
Security
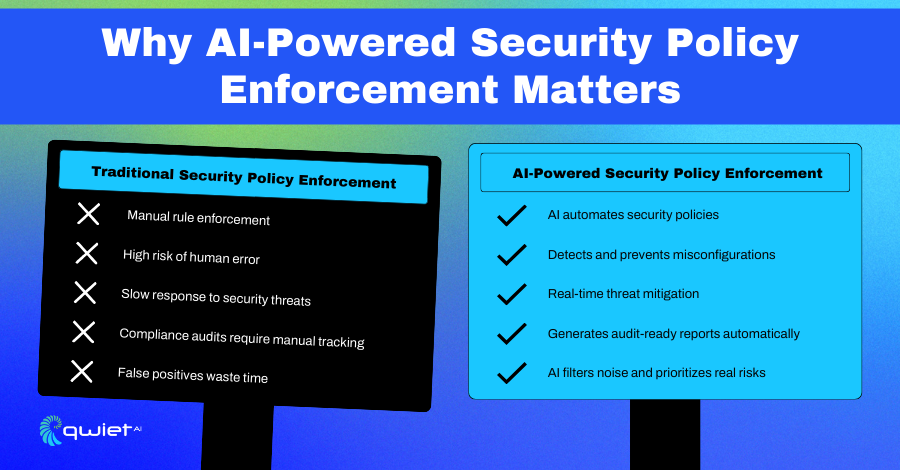
Misconfigurations and unauthorized changes are some of software development’s most significant security risks. AI-powered security policy enforcement helps catch these issues the moment they happen, blocking potential threats before they become real problems. It automatically monitors policy violations and ensures security rules remain so nothing slips through the cracks. Since AI handles enforcement in real time, teams don’t have to rely on manual checks, which means fewer mistakes and a stronger security posture.
Operational Benefits
Security shouldn’t slow teams down. AI-powered enforcement works in the background, applying security policies automatically so developers don’t have to stop and fix issues manually. It also reduces false positives so security teams aren’t flooded with unnecessary alerts. When something does need attention, AI provides developers with clear remediation steps, making it easier to fix issues without derailing their work.
Compliance and Governance
Meeting security and compliance standards like NIST, ISO 27001, and GDPR can be overwhelming, but AI makes it more manageable. It keeps security policies in check, generates audit-ready reports, and automates license compliance, so teams don’t have to stress about tracking every detail manually. Instead of scrambling to meet regulatory requirements, organizations always have an up-to-date security record at their fingertips.
Key Components of AI-Powered Security Policy Enforcement
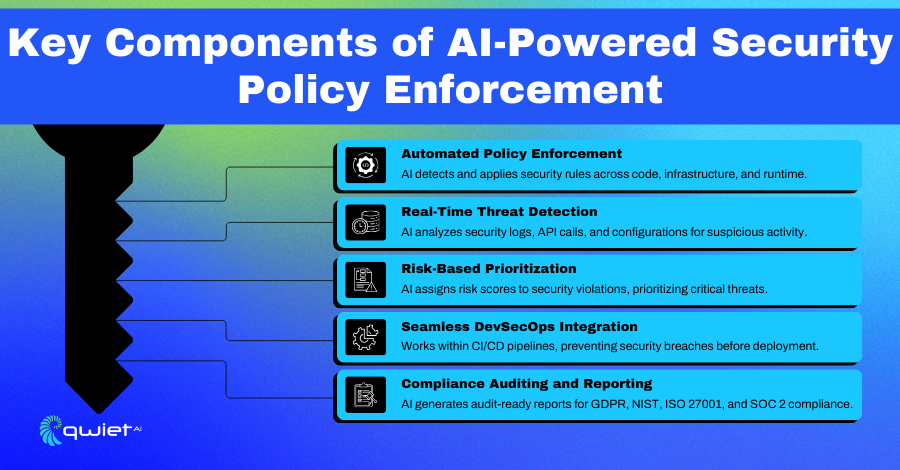
Automated Policy Enforcement
Security policies must be applied consistently across code, infrastructure, and runtime environments. AI automates enforcement by continuously scanning configurations, access controls, and system settings to check for policy violations. If it detects a misconfiguration or an unauthorized change, it can block, revert, or remediate the issue in real-time. This reduces the need for manual intervention and ensures security standards are met across every development and deployment stage.
Real-Time Threat Detection
Attackers move fast; traditional security checks don’t always catch evolving threats. AI continuously monitors security logs, API requests, and infrastructure configurations, scanning for anomalies that could indicate an attack or policy violation. Instead of flagging known vulnerabilities, AI-driven detection looks at behavioral patterns, privilege escalations, and unusual system activity. This helps security teams catch threats early, minimizing the risk of breaches.
Risk-Based Prioritization
Not all security issues carry the same level of risk. AI assigns risk scores based on factors like exploitability, impact on critical systems, and historical attack data. If a policy violation exposes sensitive data or affects a high-risk system, it gets flagged for immediate action. Low-risk issues that don’t pose an immediate threat can be scheduled for later remediation. This way, security teams focus on what matters rather than being overwhelmed by endless alerts.
Seamless DevSecOps Integration
Security needs to move at the speed of development. AI-powered policy enforcement integrates directly into CI/CD pipelines, checking for security violations at every stage of the software lifecycle. Whether it’s scanning infrastructure-as-code templates, monitoring container security, or validating access policies, AI automates enforcement without slowing down development. It also provides real-time remediation guidance, helping developers fix security issues as they code rather than waiting for manual reviews.
Compliance Auditing and Reporting
Regulatory compliance requires clear, consistent documentation of security controls, but manually tracking every change is time-consuming. AI simplifies this by maintaining a continuous log of security policies, violations, and remediations. It generates audit-ready reports aligned with frameworks like NIST, ISO 27001, and GDPR, giving teams a real-time view of their compliance status. AI can also automate license compliance checks, preventing unauthorized software use and reducing the risk of legal issues tied to open-source dependencies.
Conclusion
Manually enforcing security policies is time-consuming and leaves too much room for mistakes. Threats evolve quickly, and traditional methods struggle to keep up. AI-powered security policy enforcement changes that by automating security checks, catching misconfigurations in real-time, and making compliance easier to manage. Instead of slowing teams down, it keeps security running in the background so developers can focus on building while security stays strong. Learn more by booking a demo with Qwiet AI today.
FAQ
What is AI-powered security policy enforcement?
It’s an automated way to apply and maintain security policies across development, deployment, and operations. AI continuously monitors for policy violations, misconfigurations, and unauthorized changes, taking real-time action to enforce security policies without slowing teams down.
How does AI improve policy enforcement?
AI catches security violations the moment they happen rather than relying on periodic manual checks. It automatically prioritizes risks based on severity and impact so security teams can focus on real threats instead of getting lost in a flood of alerts. AI can provide remediation steps or even fix issues automatically when they are detected.
How does AI-powered security policy enforcement help with compliance?
AI tracks security policies and generates audit-ready reports that align with frameworks like NIST, ISO 27001, and GDPR. Instead of manually documenting compliance, teams always have an up-to-date record of security enforcement, making audits faster and easier.
Does AI-powered security policy enforcement reduce false positives?
Yes, AI analyzes security events in context, reducing unnecessary alerts. Instead of flagging every minor issue, it filters out low-risk findings and prioritizes real threats so teams don’t waste time chasing false alarms.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com
