What are Application Layer Protocols?
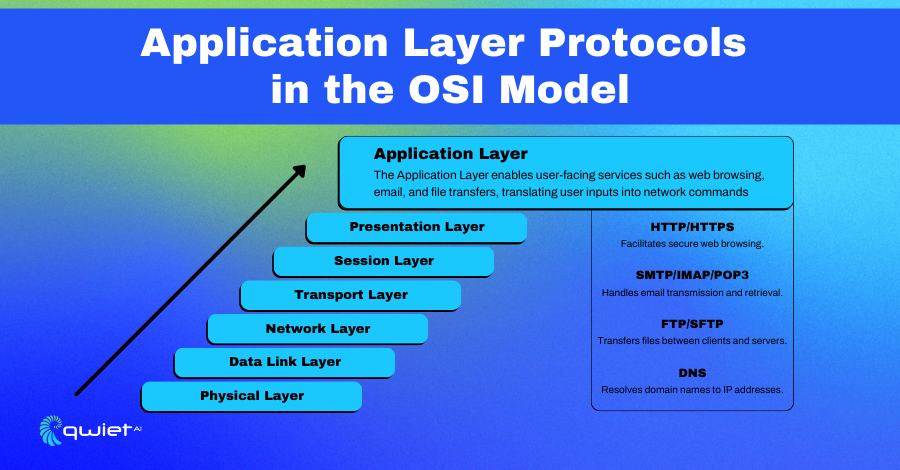
Application layer protocols operate at the highest layer of the OSI (Open Systems Interconnection) model, facilitating communication between applications over a network. They are responsible for enabling the interaction between user-facing applications and the network, translating commands into a format that can be transmitted and understood across different devices.
These protocols define how data is formatted, transmitted, and processed by application software, handling everything from web browsing to email. They structure the data, dictate how it moves across the network, and convert user commands into instructions that computers can interpret, enabling smooth communication between diverse systems.
Why Application Layer Protocols Matter
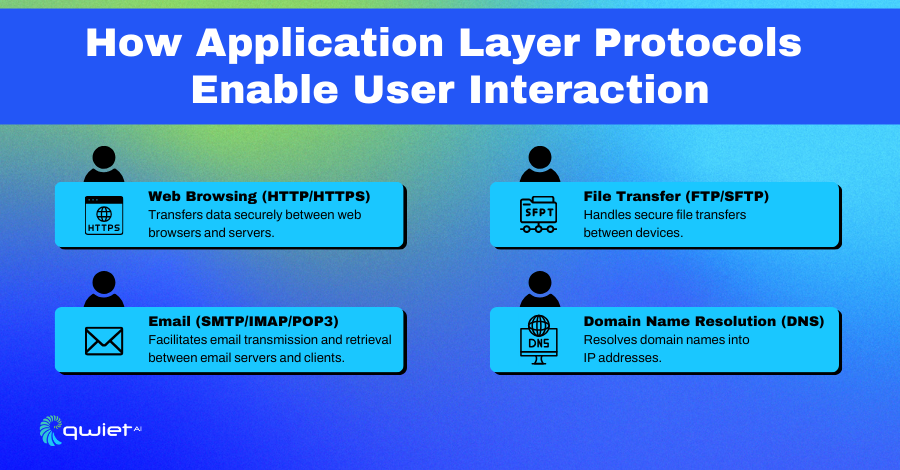
User Interaction
Application layer protocols enable services that people use every day, such as web browsing, email, and file transfers. When you access a website or send an email, these protocols handle the communication between your device and the server, ensuring the data is correctly transmitted. Without these protocols, everyday online services wouldn’t function smoothly, as they manage user interaction and network-based services.
For example, when you load a webpage using HTTP or HTTPS, the protocol ensures that your browser can request the necessary data from a web server and then display the content correctly. Similarly, protocols like SMTP or IMAP are used when sending or retrieving emails, guiding the data transfer between email clients and servers.
Data Handling
These protocols also ensure that data is properly formatted and transmitted between applications. They manage how information is structured, specifying headers, payloads, and other components of data packets. This guarantees that the information is readable and usable by the receiving application.
By carefully managing how data is sent and received, application layer protocols safeguard data integrity during transmission. For example, when transferring a file using FTP, the protocol makes sure that the data arrives intact and in a format that the receiving system can process. If there’s a disruption during transmission, the protocol manages retries or corrections to maintain data integrity.
Interoperability
Application layer protocols enable communication between different systems, platforms, and applications. These protocols standardize how data is transferred, allowing various devices and software to interact without compatibility issues. They enable seamless communication across networks by creating a consistent way for information to move between different systems.
This cross-platform compatibility is critical in environments where diverse systems must work together. For instance, DNS protocols help resolve domain names to IP addresses, allowing users on different platforms to access websites. Similarly, protocols like HTTP or FTP ensure that files and data can be exchanged across different systems, regardless of the software or operating system.
Security
Some application layer protocols integrate security features, such as encryption and authentication mechanisms, to protect data during transmission. HTTPS, for example, adds a layer of encryption to the standard HTTP protocol, making sure that data transferred between a web browser and a server is secure and protected from unauthorized access.
These protocols also manage authentication, ensuring only authorized users or systems can access certain data or services. This is especially important in applications like email or financial transactions, where sensitive information needs to be transmitted securely. By incorporating security measures at the application layer, these protocols help protect data from threats like eavesdropping or tampering.
Components of Application Layer Protocols
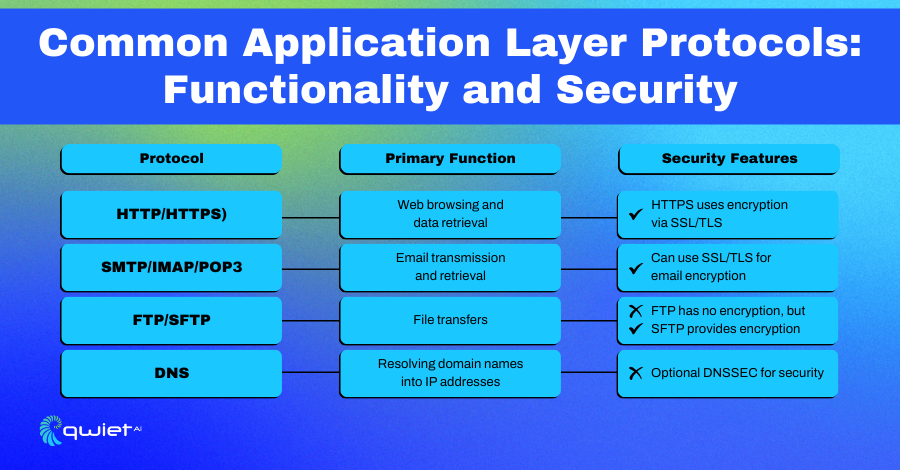
Application layer protocols come in many forms, each designed for specific types of network communication. These protocols handle tasks ranging from web browsing to email transmission, and they make it possible for different applications and services to interact over a network.
- HTTP/HTTPS: Used for web browsing, these protocols manage the communication between your browser and web servers, transmitting data such as web pages and files.
- SMTP/IMAP/POP3: These protocols facilitate the transmission and retrieval of emails, allowing messages to move between email clients and servers.
- FTP/SFTP: Used for file transfers, these protocols enable users to upload or download files between computers or servers, with SFTP adding a layer of security through encryption.
- DNS: This protocol resolves human-readable domain names into IP addresses, allowing users to access websites using familiar names instead of numeric addresses.
Data Exchange
Application layer protocols handle the structuring of data and the management of communication sessions. They define how data is organized into headers, payloads, and other components, ensuring that the receiving system understands how to process the information. These protocols also control how communication sessions are initiated, maintained, and terminated, allowing devices to establish and sustain a connection before cleanly closing it when the data exchange is complete.
Error Handling and Recovery
Some application layer protocols include mechanisms for detecting errors and managing recovery when data is lost or corrupted during transmission. These protocols monitor the data moving between systems, checking for issues like packet loss or corruption. If an error occurs, the protocol may request that the data be retransmitted or attempt to correct the issue, ensuring that the end-to-end data transfer remains accurate and reliable.
Protocol Standards
The structure and behavior of application layer protocols are often governed by standards set by organizations such as the IETF (Internet Engineering Task Force) or W3C (World Wide Web Consortium). These standards help maintain consistency across different platforms and vendors, allowing for uniform implementation of the protocols. This consistency is essential for ensuring that diverse systems can communicate with one another and that the protocols function reliably across a wide range of environments.
Conclusion
Application layer protocols enable smooth communication between applications, handling tasks like data exchange, error correction, and security for web browsing, email, and file transfers. These protocols operate under established standards to ensure compatibility across platforms. Understanding and properly managing them helps maintain secure and efficient network operations. For an added layer of security in your development process, consider using Qwiet to detect vulnerabilities in your code early. Book a call with the Qwiet team today to enhance your application security.
Read Next
Spring Boot Security Mechanisms
Introduction As businesses increasingly rely on web applications and microservices, securing them becomes important. Spring Boot is popular among developers for creating efficient microservices. This article will guide you through Spring Boot’s security options, from basic setups to advanced configurations. You’ll learn how to integrate these tools to enhance your application’s security.. Basics of Security […]
Data Encryption
Introduction Have you ever wondered how your private info stays safe online? In a world where cyber threats are rising and we share more data than ever, data encryption is our digital guardian angel. This article will take you through how encryption works to protect your information and why it’s more important now than ever. […]
Securing Python Applications with PyCrypto
Introduction Python is widely used in applications and must be protected from common security threats. This guide introduces PyCrypto, a powerful library for implementing cryptographic techniques in Python applications. You’ll learn how to encrypt and decrypt data, generate secure keys, and ensure data integrity. By reading this post, you’ll gain practical knowledge and step-by-step instructions […]