What is Cloud Security?
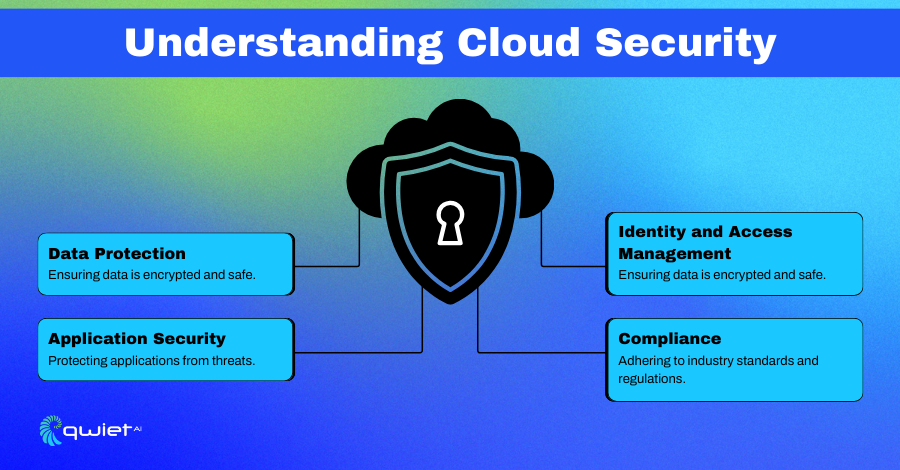
Cloud security involves using policies, technologies, and controls to protect data, applications, and infrastructure in the cloud. Its goal is to keep information confidential, maintain its integrity, and ensure it’s available when needed, all while protecting against online threats.
- Data Protection: This means keeping data safe from unauthorized access by encrypting it when stored and during transfer. It ensures that only authorized users can access sensitive information.
- Application Security: This focuses on safeguarding cloud-based applications from cyber threats. It includes practices like secure coding, regular vulnerability checks, and using application firewalls to prevent attacks.
- Identity and Access Management (IAM): IAM manages who can access cloud resources and what they can do with them. It involves verifying user identities, granting permissions, and tracking user activities to ensure proper access controls.
- Compliance: This ensures that cloud operations meet industry standards and legal requirements. Regular audits and adherence to frameworks like GDPR, HIPAA, and SOC 2 help maintain regulatory compliance.
Types of Cloud Environments
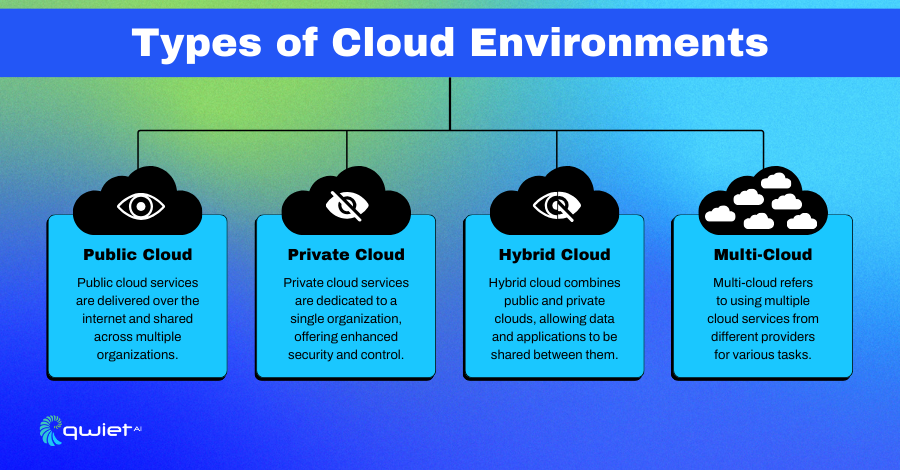
Cloud environments come in several forms, each offering unique advantages and considerations. Understanding these types helps organizations choose the best fit for their needs and security requirements.
Public Cloud
Public clouds are operated by third-party providers and offer services to multiple customers over the internet. They provide scalability and cost-efficiency, allowing businesses to pay only for the resources they use. However, data and workloads share infrastructure with other customers, necessitating robust security measures to ensure data isolation and protection.
Private Cloud
A private cloud is dedicated to a single organization, providing exclusive access to resources and infrastructure. This setup offers greater control over security configurations and compliance with internal policies. While it may involve higher costs due to the need for dedicated hardware and maintenance, it provides enhanced privacy and control over data and applications.
Hybrid Cloud
Hybrid clouds combine public and private cloud environments, allowing data and applications to move between them as needed. This model provides flexibility, enabling organizations to leverage the scalability of public clouds for non-sensitive operations while maintaining private clouds for critical workloads. Proper integration and management are essential to ensure seamless operation and security across both environments.
Multi-cloud
A multi-cloud strategy involves using multiple cloud services from different providers to avoid dependency on a single vendor. This approach enhances redundancy and resilience, allowing organizations to optimize performance and costs by selecting the best services from each provider. Effective management and interoperability between providers are crucial to address potential challenges in security and governance.
Security Challenges in the Cloud
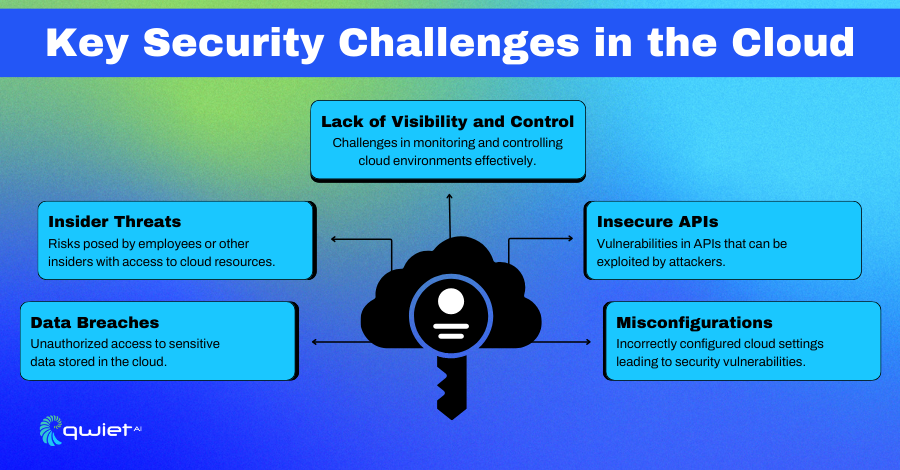
Cloud environments have unique security challenges that need to be addressed to keep data and applications safe. Understanding these challenges is essential for setting up effective security measures.
Data Breaches
What it is: A data breach is when unauthorized people access sensitive information.
How it happens in the cloud: In the cloud, data breaches can occur due to weak security controls, outdated software, or sophisticated cyberattacks. Since your data is stored on remote servers, using strong encryption, regular security checks, and strict access controls is crucial to keep it safe.
Insider Threats
What it is: Insider threats involve harmful actions taken by employees or others within the organization.
How it happens in the cloud: In cloud environments, insiders might misuse their access to cloud resources to steal or expose data, intentionally or by mistake. Organizations should implement strict access management policies to prevent this, continuously monitor user activities, and use tools to detect unusual behavior.
Insecure APIs
What it is: APIs (Application Programming Interfaces) allow different software applications to communicate.
How it happens in the cloud: Insecure APIs can be exploited by attackers to gain unauthorized access to cloud services and data. These vulnerabilities arise when APIs are not properly secured. Regularly testing APIs, using strong authentication, and following secure coding practices are essential to protect these interfaces.
Misconfigurations
What it is: Misconfigurations are incorrect settings that leave systems vulnerable.
How it happens in the cloud: Misconfigurations can occur in cloud environments when permissions are set incorrectly, data isn’t encrypted, or firewall rules are inadequate. These errors can lead to exposed data and unauthorized access. Regular configuration reviews, automated security tools, and best practices can help prevent these issues.
Lack of Visibility and Control
What it is: Lack of visibility and control means needing to monitor and manage cloud resources effectively.
How it happens in the cloud: In complex cloud environments, especially with multiple cloud services, it can be hard to track all resources and promptly detect security issues. Using centralized security management tools, continuous monitoring, and detailed logging can improve visibility and allow for quick responses to potential threats.
Shared Responsibility Model
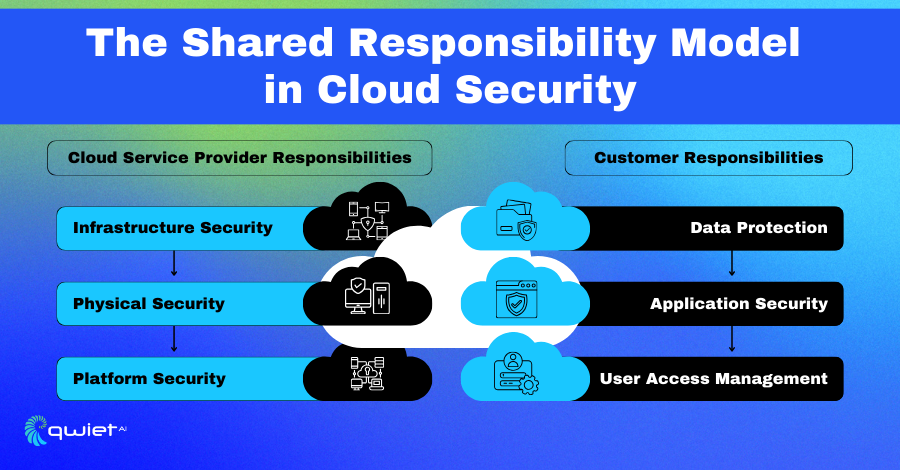
The shared responsibility model in cloud security outlines the distinct roles of cloud service providers and their customers in protecting the cloud environment. This clear division of responsibilities ensures that both parties can effectively contribute to maintaining security.
Responsibilities of Cloud Service Providers
Cloud service providers are responsible for securing the core infrastructure and cloud platform services. Their key responsibilities are:
- Infrastructure Security:
- Protecting servers, storage, and networking components from threats.
- Physical Security:
- Implementing strict access controls.
- Utilizing surveillance systems.
- Ensuring environmental protections to prevent physical breaches and damage.
- Platform Security:
- Securing the cloud platform, including operating systems and virtualization software.
- Applying regular updates and patches.
- Monitoring for vulnerabilities.
- Maintaining a robust security posture to protect against threats.
Responsibilities of Customers
Customers are responsible for securing their data and applications within the cloud environment. Their key responsibilities include:
- Data Protection:
- Encrypting data to safeguard it.
- Managing encryption keys securely.
- Ensuring that data access is restricted to authorized users.
- Application Security:
- Following secure coding practices.
- Performing regular security assessments.
- Using application-level security controls.
- User Access Management:
- Managing user identities.
- Defining and enforcing access policies.
- Implementing strong authentication and authorization mechanisms to ensure only legitimate users can access cloud resources.
Cloud Security Technologies and Tools
Protecting cloud environments requires advanced tools and technologies. When used together, these solutions help safeguard data and applications from threats.
Firewalls and Intrusion Detection/Prevention Systems (IDS/IPS)
Firewalls and IDS/IPS are essential for network security; firewalls act as barriers that block unauthorized access to your network. IDS/IPS systems detect and stop suspicious activities in real-time. Together, these tools keep your network traffic safe from external threats.
Security Information and Event Management (SIEM)
SIEM tools gather and analyze security data from various sources in your cloud environment. They provide real-time alerts and valuable insights into potential security issues. SIEM systems help you quickly detect and respond to unusual activities, comply with security regulations, and conduct detailed analyses for better security management.
Endpoint Protection Platforms (EPP)
EPP solutions protect devices that connect to the cloud, like laptops, smartphones, and servers. These platforms offer antivirus protection, anti-malware defenses, and data encryption. By securing these devices, EPPs help prevent breaches that could affect your entire cloud environment and ensure all devices adhere to security policies.
Cloud Access Security Brokers (CASB)
CASBs serve as go-betweens for cloud users and service providers, enforcing security policies and providing visibility into cloud usage. They help manage risks by offering data loss prevention and threat protection features. CASBs ensure that your data is secure and that access to cloud resources is properly controlled, helping you meet regulatory requirements.
Conclusion
This article covered the essentials of cloud security, including key components, types of environments, security challenges, and important tools. Strong cloud security is crucial for any organization using cloud services. Tools like Qwiet can help detect vulnerabilities in your applications before they can be exploited.
To improve your cloud security, book a demo today to see how Qwiet can secure your codebase and protect your application from threats.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com