What is Container Security?
Container security is applying security measures to protect containerized applications and their infrastructure. Containers are lightweight, portable units that package an application with all its dependencies, ensuring it can run consistently across various environments, whether on-premises or in the cloud.
Securing containers means focusing on several components, including container images, container runtime, orchestration systems like Kubernetes, and the underlying host infrastructure. Each layer needs protection to prevent vulnerabilities and ensure the applications’ integrity within containers.
Why Container Security Matters
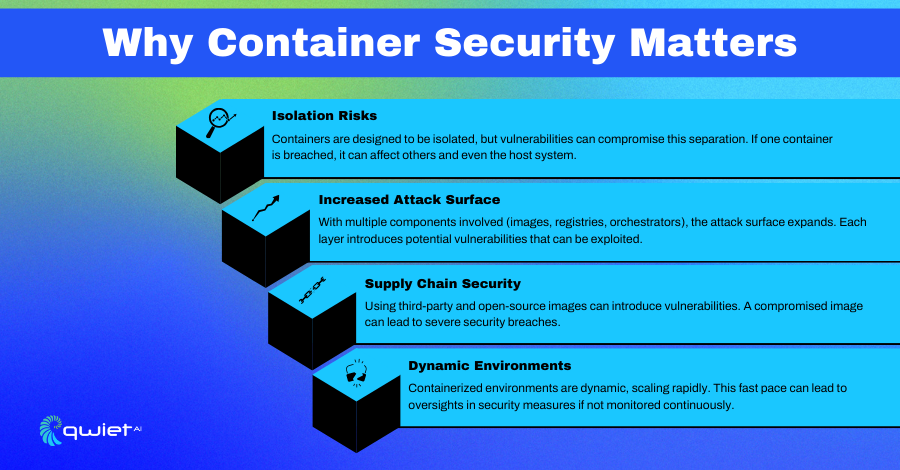
Isolation Risks
Containers share the host operating system’s kernel, making proper isolation between containers critical. Without strong security measures, a compromise in one container could potentially impact other containers or even the host system. Keeping containers isolated helps prevent lateral movement within the environment if one container is breached.
Increased Attack Surface
Using containers introduces many moving parts, from container images to registries and orchestration systems. Each of these components adds to the attack surface, meaning there are more potential entry points for attackers to exploit. Properly securing all these elements is necessary to reduce vulnerabilities and keep the system safe.
Supply Chain Security
Containers often rely on third-party images and open-source components, which may contain hidden vulnerabilities. Because these images are part of the application’s supply chain, assessing their security and trustworthiness is critical. This helps prevent the introduction of vulnerabilities that could be exploited during production.
Dynamic Environments
Containerized environments are highly dynamic, scaling up and down rapidly to meet application demands. This fast-paced nature requires continuous monitoring and automated security measures to keep up with potential changes or new threats. Having real-time visibility into the environment helps respond to risks as they emerge.
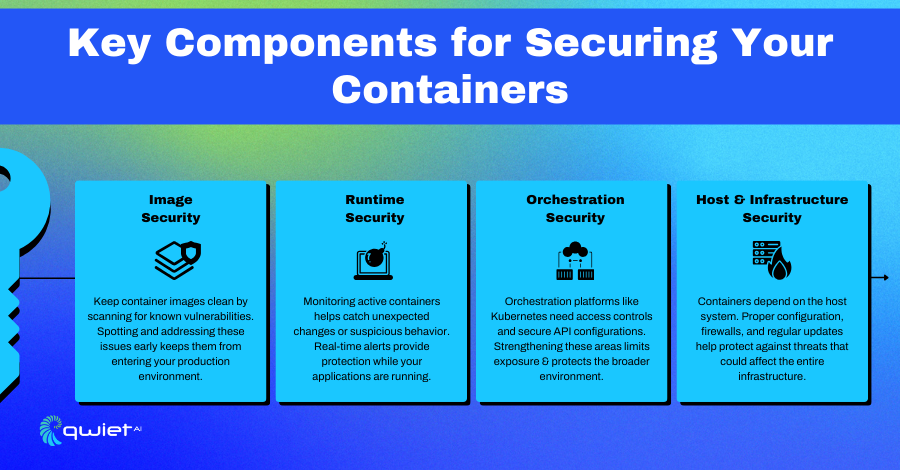
Components of Container Security

Image Security
Image security focuses on making sure the container images you use are safe and free from vulnerabilities. This starts with scanning images for known issues before they are deployed. Verifying the source of these images is just as important—using untrusted images can introduce security risks into your environment. Regularly reviewing and scanning these images reduces the chance of security gaps in your containers.
Storing these images in secure, well-maintained registries is another important aspect. Secure registries help prevent the use of compromised or outdated images. Regular updates and keeping a close watch on these images ensures that your containers start with a strong, reliable foundation.
Runtime Security
When containers are running, monitoring them for any unusual behavior is important. Runtime security tools help track containers in real time to detect potential threats or abnormal activity that could signal a security issue. This monitoring helps spot problems like misconfigurations or malicious actions, helping maintain a stable and secure environment.
Real-time threat detection tools can automatically alert teams to any issues during operation. These tools not only detect threats but can also trigger incident response actions, minimizing downtime and damage. Monitoring container behavior is essential to preventing threats from escalating once the containers are in use.
Orchestration Security
Orchestration systems, such as Kubernetes, simplify container management but require proper security controls. Securing access to these systems is important, especially through the APIs used to control them. By restricting access to these APIs, organizations can limit the chances of unauthorized users making changes or accessing sensitive areas.
Role-based access control (RBAC) is also key to controlling who can do what within the orchestration system. Giving users or services the right level of access while limiting unnecessary permissions reduces the risk of accidental or malicious activity. Network policies also play a role in securing communication between containers, further locking down the system.
Host and Infrastructure Security
The host system’s security, which runs the containers, is just as important as securing the containers themselves. Strong access controls should be in place to limit who can interact with the host system, preventing unauthorized access. Monitoring the health and status of the host is equally important, as any compromise here could affect the entire environment.
Ensuring secure communication between containers is another critical factor. Misconfigured communication or vulnerabilities in how containers interact can lead to serious security breaches. A strong focus on both host and infrastructure security helps prevent issues that could impact the entire containerized ecosystem.
Conclusion
Container security protects everything in a containerized environment, from scanning images for vulnerabilities to monitoring running containers and securing orchestration tools like Kubernetes and the host system. Regular scans and monitoring help reduce risks and keep applications safe as these environments get more complex. Qwiet can find vulnerabilities in your code early on for added protection. Reach out to the Qwiet team today to learn more.
Read Next
Microservices Security Overview
What is Microservices Security? Microservices security is the comprehensive approach to safeguarding each service within a microservices architecture. In this model, each service functions independently, which creates unique security requirements for each one. To secure these distributed services, microservices security involves methods to protect inter-service communications, secure APIs, and manage access and identity across multiple […]
Vulnerability Assessment Overview
What is a Vulnerability Assessment? A vulnerability assessment is a thorough check-up of your information systems to find any security weaknesses. This involves identifying, classifying, and prioritizing potential vulnerabilities in your computer systems, networks, and communication channels. The goal is to uncover any weak spots that might be targeted by cyber threats so you can […]
DevSecOps Overview
What is DevSecOps? DevSecOps stands for Development, Security, and Operations. It’s an approach that builds security into every part of the software development process. Instead of adding security measures at the end, DevSecOps makes security a key part of the workflow from the very beginning. This method encourages development, operations, and security teams to work […]