Key Takeaways
- Stay Ahead of Advanced Threats: Behavioral Threat Detection uncovers risks like zero-day attacks and insider threats by monitoring patterns and identifying suspicious behavior in real-time.
- Accurate and Actionable Insights: With machine learning and contextual analytics, it cuts down on false alarms and helps teams focus on real threats with clear guidance for response.
- Streamlined Threat Mitigation: It works seamlessly with tools like SIEM and SOAR to automate responses and make managing incidents faster and more efficient.
What are Critical Dependency Insights?
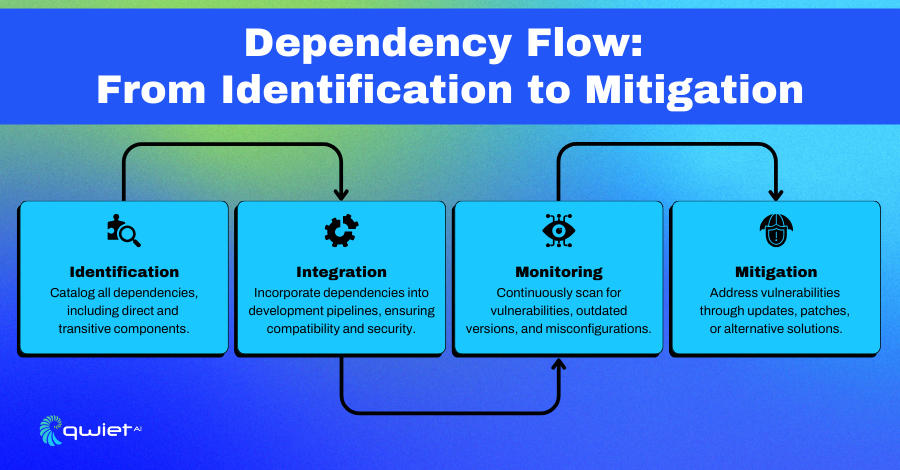
Critical Dependency Insights provide a structured approach to identifying, monitoring, and analyzing the dependencies that software systems, infrastructure, and supply chains rely on to operate effectively. These dependencies include third-party libraries, APIs, frameworks, and external systems that integrate with applications. By understanding how these components interact and contribute to the overall system, organizations can assess their criticality, identify potential vulnerabilities, and take action to minimize associated risks.
This methodology goes beyond cataloging dependencies by evaluating their impact on security, operational stability, and performance. It helps mitigate risks tied to external components, such as insecure libraries or outdated versions, which can introduce vulnerabilities or cause failures. Through detailed analysis, Critical Dependency Insights support proactive measures to address dependency-related issues, improve system resilience, and maintain continuity, even when individual components fail or face security threats.
Why Do Critical Dependency Insights Matter?
Security
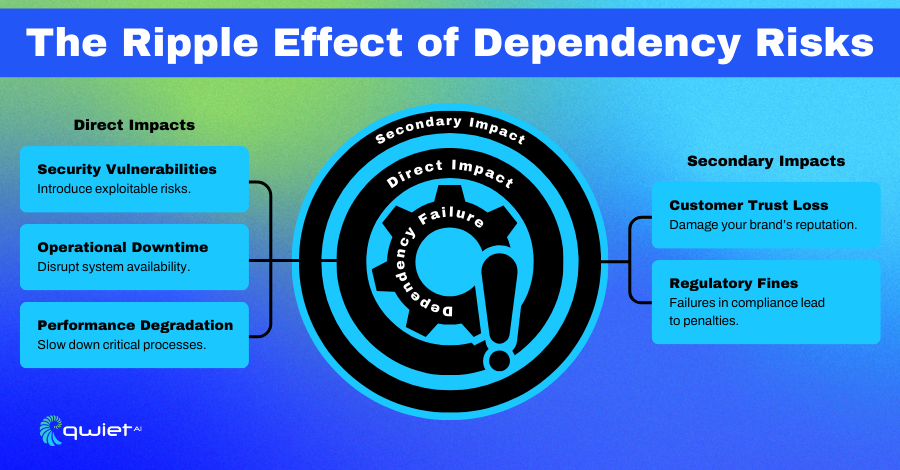
Critical Dependency Insights help organizations uncover vulnerabilities in third-party components like libraries, APIs, and frameworks, giving teams the tools to address issues before they become security risks. With this level of visibility, it’s easier to identify weak points in the supply chain and make timely fixes, keeping systems secure and reducing the risk of potential attacks.
They also play a big role in protecting against supply chain threats. By highlighting insecure components or vendors and monitoring for zero-day vulnerabilities, teams can respond quickly to emerging risks. This proactive approach helps safeguard systems from attackers looking to exploit these weaknesses.
Operational Resilience
Managing dependencies effectively is essential for keeping systems running smoothly. Critical Dependency Insights help identify risks tied to component failures so teams can address them before they cause disruptions. By analyzing how dependencies interact, they also reduce the chances of cascading failures that could impact multiple parts of the system.
Another benefit is version management. Monitoring updates and patches for dependencies ensures systems remain compatible and secure. This prevents downtime and strengthens applications’ overall reliability, allowing operations to continue without interruption.
Compliance and Governance
Meeting regulatory requirements is a lot easier with Critical Dependency Insights. They align dependency management practices with security standards like OWASP, ISO 27001, and NIST, providing the data needed to demonstrate compliance. These insights are especially helpful during audits, offering clear evidence of risk management efforts.
Another plus is the ability to create detailed reports documenting risks and the actions taken to mitigate them. This shows a proactive commitment to securing systems and protecting supply chains. This transparency not only reduces liability but also builds trust with stakeholders.
Components of Critical Dependency Insights
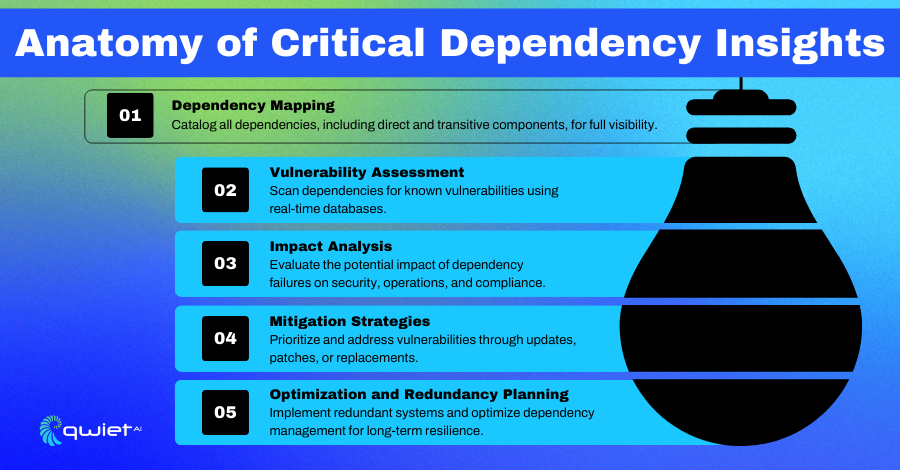
Dependency Mapping
Dependency Mapping provides a detailed inventory of all dependencies, including direct and transitive ones, giving teams a clear understanding of the software and systems they rely on. It uses visualization tools like dependency graphs to highlight critical paths and pinpoint areas where failures could occur. This level of insight helps teams identify risks and prioritize actions to strengthen their systems’ overall stability.
Vulnerability Assessment
Vulnerability Assessment focuses on continuously scanning dependencies to identify known vulnerabilities, leveraging databases such as NVD and CVE. It informs teams of real-time alerts when new vulnerabilities are discovered, enabling them to respond quickly. This proactive approach minimizes exposure to risks and reduces the time vulnerabilities remain in systems.
Impact Analysis
Impact Analysis evaluates the criticality of each dependency to the stability and security of the overall system. It prioritizes risks by analyzing their potential impact and simulates failure scenarios to understand how disruptions could affect operations. These insights help teams design failover strategies to mitigate risks and maintain system resilience.
Dependency Optimization
Dependency Optimization focuses on maintaining secure and stable versions by tracking and managing updates. It also identifies areas where alternative or backup solutions are needed to increase system resilience. By addressing these areas, teams can minimize downtime and ensure their systems operate smoothly, even when challenges arise.
Reporting and Insights
Reporting and Insights deliver actionable recommendations to reduce risks and improve the security of critical dependencies. These reports are tailored to support audits and regulatory reviews, providing clear evidence of dependency management practices. This transparency helps organizations meet compliance requirements and maintain trust with stakeholders.
Conclusion
Critical Dependency Insights help organizations manage risks tied to third-party components and supply chains by providing the tools to identify vulnerabilities, analyze dependencies, and strengthen system resilience. By adopting these practices, teams can focus on delivering secure, reliable software without unnecessary disruptions. Qwiet makes managing dependencies easier by offering clear insights and actionable solutions to reduce risks and improve security. Book a demo today to see how Qwiet can help protect your systems and keep your software dependable.
FAQ
1. What are Critical Dependency Insights?
Critical Dependency Insights refer to identifying, monitoring, and analyzing software and supply chain dependencies to mitigate risks. They help organizations uncover vulnerabilities, address dependency failures, and maintain operational stability.
2. Why are Critical Dependency Insights important for security?
They provide visibility into third-party components and supply chain vulnerabilities, enabling teams to address risks like insecure libraries, zero-day vulnerabilities, and potential supply chain attacks. This proactive approach strengthens overall system security.
3. How do Critical Dependency Insights support compliance?
They align with standards like OWASP, ISO 27001, and NIST by providing clear documentation of risks and the steps taken to mitigate them. These insights simplify audits and demonstrate adherence to regulatory requirements.
4. What role does dependency mapping play in risk management?
Dependency mapping catalogs all direct and transitive dependencies and creates visualizations to highlight critical paths and potential points of failure. This helps organizations identify high-risk areas and prioritize remediation efforts.
5. Can Critical Dependency Insights help with operational resilience?
Yes, by analyzing interdependencies and planning for failure scenarios, Critical Dependency Insights help prevent cascading failures, minimize downtime, and maintain system reliability, even when challenges arise.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com