What is Cryptography?
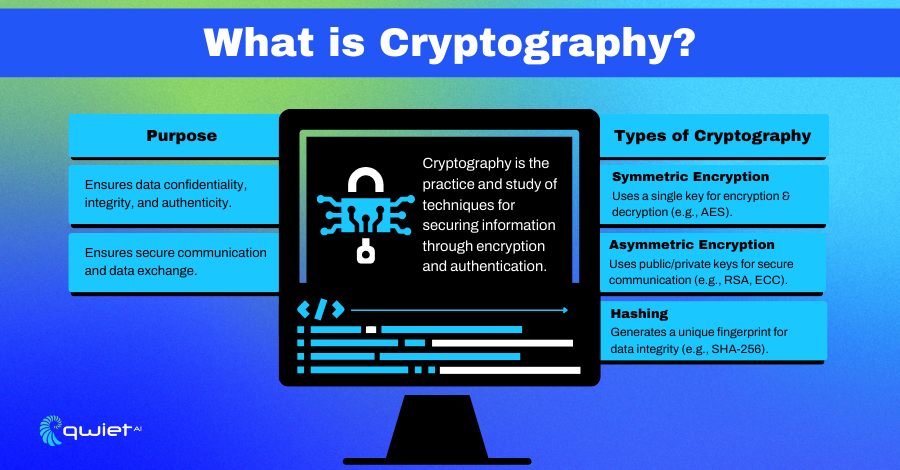
Cryptography is the practice and study of securing communication and data so that only authorized parties can access it, even when adversaries are present. It uses mathematical techniques to transform information into unreadable formats without proper authorization.
The main goal of cryptography is to protect data. It keeps information private (confidentiality), verifies its accuracy (integrity), and confirms the identity of the parties involved (authenticity). These protections are vital in maintaining trust in communications and securing sensitive information.
Cryptography is built on three main methods, each designed for specific security purposes:
- Symmetric Encryption: Uses the same key for encrypting and decrypting data, making it efficient and fast for large amounts of data. Examples include AES and DES.
- Asymmetric Encryption: Uses a pair of public and private keys to encrypt and decrypt information, ideal for secure communication.
- Hashing: Converts data into a fixed-length hash that uniquely represents the input, helping to detect any changes and maintain data integrity. Popular methods include SHA-256.
Why Does Cryptography Matter?
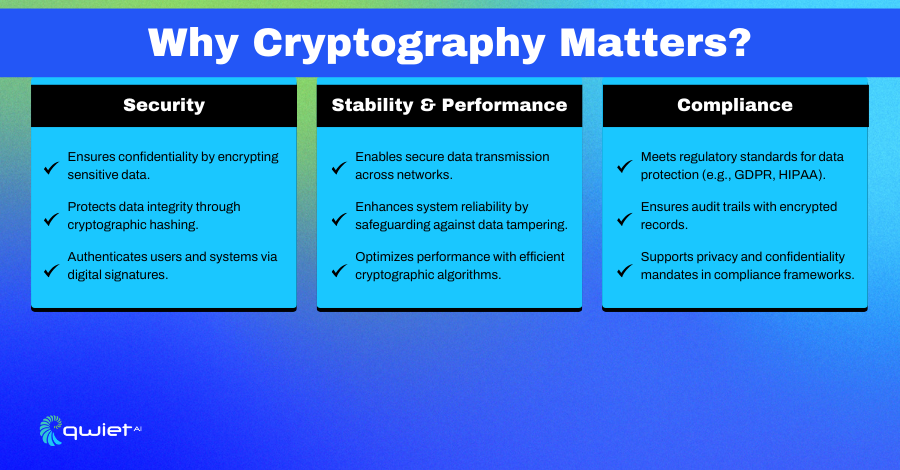
Security
Cryptography is central in securing data by making it accessible only to authorized parties. It protects confidentiality by encrypting information, so even if intercepted, it remains unreadable without the proper decryption key. Cryptographic hashes safeguard integrity by detecting any unauthorized changes to the data, ensuring what you send is exactly what is received. It also provides authentication, verifying the identity of users and confirming that communications or transactions are legitimate, which is essential for trust in digital interactions.
Stability & Performance
Strong cryptography keeps systems stable by protecting data from compromise, even in challenging or hostile environments. It allows sensitive information to move securely across networks, even those that may not be completely trustworthy. Modern cryptographic algorithms are optimized for large-scale operations, supporting efficient performance across systems and environments without sacrificing security.
Compliance
Cryptography is often a key component in meeting data protection requirements outlined by GDPR, HIPAA, and PCI-DSS regulations. Encryption standards protect data privacy during storage and transmission, keeping sensitive information safe from unauthorized access. Cryptographic tools also support compliance efforts by generating detailed and secure audit trails, making demonstrating adherence to regulatory standards easier.
Components of Cryptography
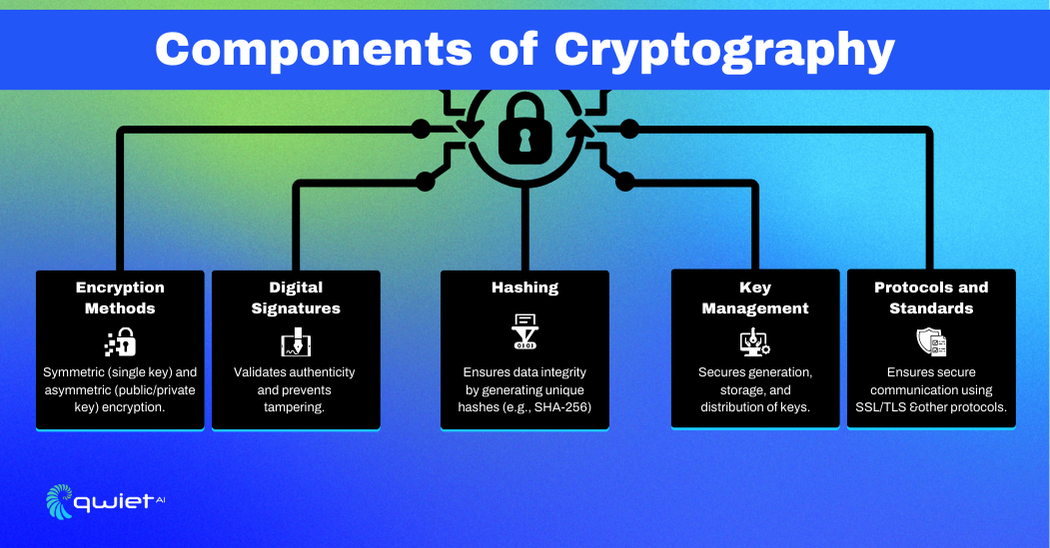
Encryption Methods
Encryption methods are the backbone of cryptography and have two primary types. Symmetric encryption uses a single key for encrypting and decrypting data, making it fast and efficient for large amounts of information. Popular examples include AES and DES.
On the other hand, asymmetric encryption works with a pair of keys—a public key for encryption and a private key for decryption. This method, used in systems like RSA and ECC, is ideal for secure communication and data exchange where sharing a single key isn’t practical.
Hashing
Hashing creates a unique, fixed-length string (or “hash”) from input data, no matter the original data size. This process is one-way, meaning the original data can’t be retrieved from the hash. Hashing is essential for maintaining data integrity; even the smallest change to the input data will produce a completely different hash. Algorithms like SHA-256 are widely used to detect tampering and verify that data hasn’t been altered.
Digital Signatures
Digital signatures validate the authenticity and integrity of messages, documents, or transactions. Cryptographic techniques act as a seal of trust, confirming that the sender is genuine and that the message hasn’t been altered. Digital signatures also offer non-repudiation, meaning the sender can’t deny their involvement once the signature is applied, which is critical in legal and financial contexts.
Key Management
Key management handles the generation, storage, and distribution of cryptographic keys. Since keys are central to encryption and security, managing them securely is a priority. Hardware security modules (HSMs) or dedicated software solutions are often used to protect keys from unauthorized access and ensure they’re available when needed. Proper key management ensures encryption systems function securely and reliably.
Protocols and Standards
Cryptographic protocols and standards set the rules for establishing and maintaining secure communications. Protocols like SSL/TLS safeguard data as it moves across networks, protecting sensitive information during transmission. Industry standards such as PKCS and X.509 ensure systems and devices can communicate securely and reliably, even from different vendors or organizations. These standards form the foundation of trust in secure communications.
Conclusion
Cryptography is essential for keeping data secure, authentic, and untampered with. It protects sensitive information, whether stored or shared, helps verify identities, and ensures trust in every interaction. Strong encryption and smart cryptographic practices safeguard your applications and systems. That’s where our tool, Qwiet, identifies weak encryption in your code and ensures your application uses strong, secure methods to protect your data. Ready to take the next step in strengthening your security? Book a demo with Qwiet today.
Read Next
Security Headers
What are Security Headers? Security headers are tools web servers use to protect web applications by dictating how browsers should behave when handling a website’s content. These headers enhance security by preventing common vulnerabilities like cross-site scripting (XSS), clickjacking, and other code injection attacks. By specifying certain policies directly in the HTTP response headers, web […]
Data Encryption
Introduction Have you ever wondered how your private info stays safe online? In a world where cyber threats are rising and we share more data than ever, data encryption is our digital guardian angel. This article will take you through how encryption works to protect your information and why it’s more important now than ever. […]
Authentication and Authorization
Introduction Dive into online security with a closer look at authentication and authorization. This article unravels how these key processes verify your identity and manage your access rights, acting as the frontline defenses for your data. What are Authentication and Authorization? Authentication verifies a user’s identity with things like passwords or fingerprints. It’s about making […]