What is Cybersecurity Compliance?
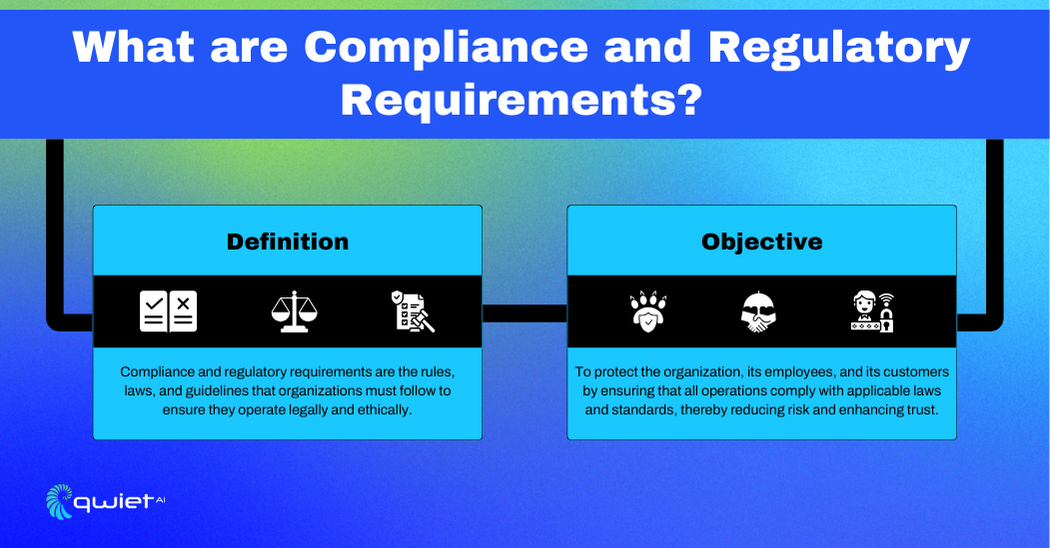
Cybersecurity compliance means following the rules, standards, and best practices that help protect your information systems and data from cyber threats. These regulations outline the minimum security steps organizations need to take to keep sensitive information safe and ensure their systems are secure and reliable.
Sticking to compliance and regulatory requirements is important for a few reasons. First, it helps protect your sensitive data and keeps you out of legal trouble. It also builds trust with your customers and partners because they know you’re serious about security. Plus, compliance pushes you to keep improving your security measures to stay ahead of new threats.
Main Cybersecurity Compliance Frameworks
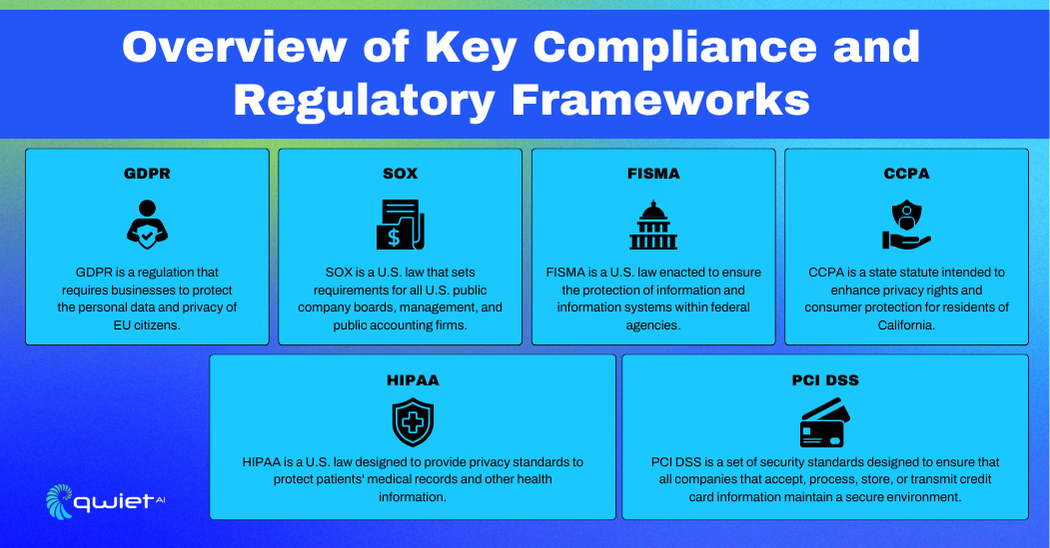
General Data Protection Regulation (GDPR)
The GDPR is a regulation in the European Union designed to protect the privacy and personal data of individuals. It sets out strict guidelines for how personal data should be collected, processed, and stored to ensure individuals’ privacy rights are upheld.
The GDPR includes data protection principles that organizations must follow, such as lawfulness, fairness, and transparency. It also outlines the rights of data subjects, including access to their data and the right to be forgotten. Non-compliance with GDPR can result in significant penalties.
Health Insurance Portability and Accountability Act (HIPAA)
HIPAA sets standards for protecting sensitive patient health information. Its main goal is to ensure that healthcare providers, insurers, and other entities safeguard the privacy and security of health data. HIPAA includes the Privacy Rule, which protects patient information; the Security Rule, which sets standards for electronic health data protection; and the Breach Notification Rule, which requires entities to notify individuals of data breaches.
Payment Card Industry Data Security Standard (PCI DSS)
PCI DSS is a set of security standards designed to ensure that all companies that process, store, or transmit credit card information maintain a secure environment. It aims to protect cardholder data and reduce credit card fraud. PCI DSS involves protecting cardholder data through encryption and secure storage, maintaining a secure network with firewalls and other security measures, and managing vulnerabilities through regular updates and monitoring.
Sarbanes-Oxley Act (SOX)
SOX aims to improve the accuracy and reliability of corporate disclosures. It was enacted to protect investors from fraudulent accounting activities by corporations. SOX includes stringent financial reporting requirements, internal controls to ensure the accuracy of financial data, and mandatory audits to verify compliance.
Federal Information Security Management Act (FISMA)
FISMA requires federal agencies to develop, document, and implement an information security program to protect their information and systems from threats. FISMA involves creating an information security framework for federal agencies, conducting risk assessments, and implementing security controls to manage and mitigate risks.
California Consumer Privacy Act (CCPA)
The CCPA enhances privacy rights and consumer protection for California residents. It provides guidelines for businesses on how to handle personal data. The CCPA includes giving consumers rights over their personal data, such as the right to know what data is collected and the right to delete their data. It also imposes penalties for non-compliance to ensure businesses adhere to the regulations.
How to Adhere to Cybersecurity Compliance

Understanding Requirements
First, get a clear understanding of the laws and regulations that apply to your organization. Spend time researching these rules to ensure you’re not missing anything important. Also, don’t forget to look into any industry-specific requirements that might affect your business. This way, you can make sure your compliance efforts are perfectly tailored to your needs.
Gap Analysis
A gap analysis is a great way to assess your compliance status. Compare your existing practices to the requirements. This will help you identify areas for improvement and give you a clear idea of what needs to be done to get up to speed.
Developing Compliance Programs
Developing solid compliance programs means creating policies and procedures that meet all the necessary requirements. Make sure these guidelines are clear and practical. Setting up dedicated compliance teams and assigning specific roles ensures that someone is always keeping an eye on compliance matters.
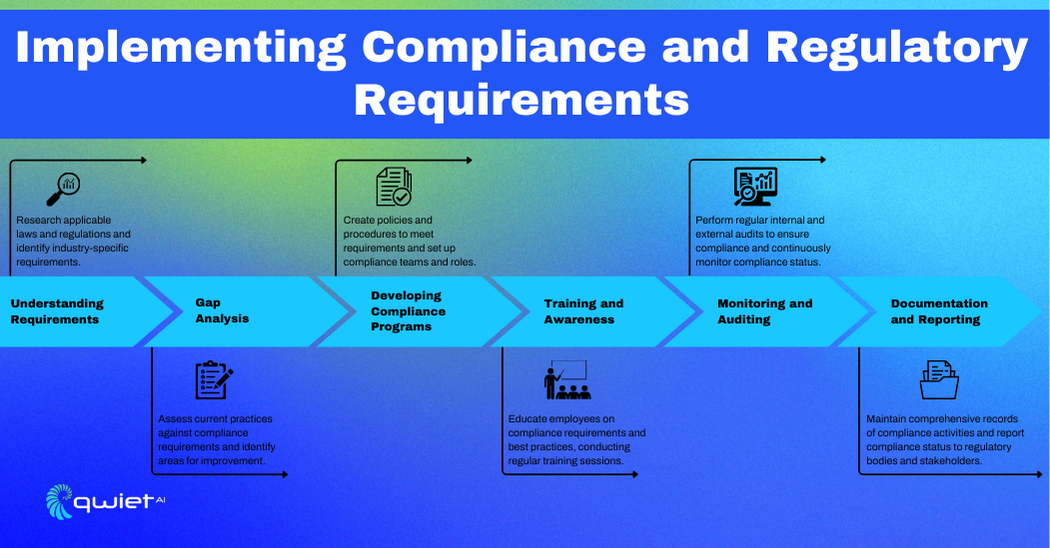
Training and Awareness
It’s important to keep everyone in the loop when it comes to compliance. Educate your employees about the requirements and best practices, so they understand what’s expected of them. Regular training sessions can help keep everyone updated on any changes and reinforce the importance of staying compliant.
Monitoring and Auditing
Regular audits, both internal and external, are essential for maintaining compliance. These audits can help you spot any issues and address them before they become bigger problems. Continuous monitoring of your compliance status ensures that you’re always on top of things.
Documentation and Reporting
Keeping detailed records of all your compliance activities is a must. This documentation helps you stay organized and makes it easier to report your compliance status to regulatory bodies and stakeholders. Regular reporting ensures transparency and accountability within your organization.
Conclusion
Cybersecurity compliance is all about following key rules and best practices to keep your data and systems safe from threats. By sticking to frameworks like GDPR, HIPAA, PCI DSS, SOX, FISMA, and CCPA, you protect your sensitive information and build trust with your customers and partners. Staying compliant helps you avoid legal issues and keeps your security measures sharp. Want to make sure your application is both compliant and secure? Book a demo with Qwiet today to find out how it can improve your application’s security posture to meet compliance.
Read Next
Vulnerability Assessment Overview
What is a Vulnerability Assessment? A vulnerability assessment is a thorough check-up of your information systems to find any security weaknesses. This involves identifying, classifying, and prioritizing potential vulnerabilities in your computer systems, networks, and communication channels. The goal is to uncover any weak spots that might be targeted by cyber threats so you can […]
Interactive Application Security Testing (IAST) Overview
What is Interactive Application Security Testing (IAST)? Interactive Application Security Testing (IAST) analyzes an application’s security while actively running. Unlike other approaches, it integrates directly with the app, allowing it to spot vulnerabilities as the code executes. This gives more accurate insights than methods that only look at static code or run tests outside the […]
Secure Your Java Applications with JSSE: A Comprehensive ...
Introduction Ever wondered how to keep your Java applications safe from prying eyes and cyber threats? This blog post dives into Java Secure Socket Extension (JSSE), a powerful tool for securing communications in your Java applications. We’ll explore the features and configurations of JSSE, showing you how to establish secure socket communications to protect your […]