Introduction
If you’re here, you’re probably trying to figure out how to get compliant with NIST SP 800-218, right? Don’t worry—you’re in the right place. This post will explain exactly what NIST SP 800-218 is and why it matters for your software development. You’ll learn the key steps to achieving compliance and how tools like Qwiet can take the headache out of the process, all while strengthening the security of your software from the ground up.
What is NIST SP 800-218?
NIST SP 800-218, also called the Secure Software Development Framework (SSDF), is a set of best practices that guide organizations in building security into their software development process. It provides steps to help developers and security teams reduce vulnerabilities as they build, test, and deploy software. Whether you’re developing web apps, APIs, or more complex systems, the SSDF helps ensure security is a core part of the Software Development Life Cycle (SDLC) from day one.
The framework integrates security at every phase of the SDLC, from planning and coding to testing and deployment. This allows teams to minimize the chances of vulnerabilities slipping through the cracks and more effectively manage risks. It’s a structured approach to ensuring security isn’t just an afterthought but a part of how the software is designed and delivered.
In February 2024, NIST rolled out an update to SP 800-218 based on feedback from different industries. This update fine-tuned the guidelines to address modern challenges in software security, focusing on ways to reduce vulnerabilities better. It’s aimed at helping organizations align their development practices with the latest security standards, keeping software more secure in today’s evolving threat landscape.
Why is NIST SP 800-218 Compliance Important?
NIST SP 800-218 compliance helps make security a natural part of the software development process. By following these guidelines, teams can catch vulnerabilities early and ensure that security is built into every stage of development. This reduces the risk of breaches and keeps your software more secure.
In industries like government, defense, and critical infrastructure, compliance isn’t just a good idea it’s often required. These sectors deal with highly sensitive data, and NIST SP 800-218 provides clear security practices to meet those high standards. Staying compliant helps protect critical systems and ensures compliance with necessary regulations.
Compliance can also be a real advantage. Many contracts, especially in regulated industries, require you to follow NIST’s framework. Showing you’re compliant not only proves you take security seriously but it also builds trust with clients and partners, giving you a competitive
Key Components of NIST SP 800-218 for Compliance
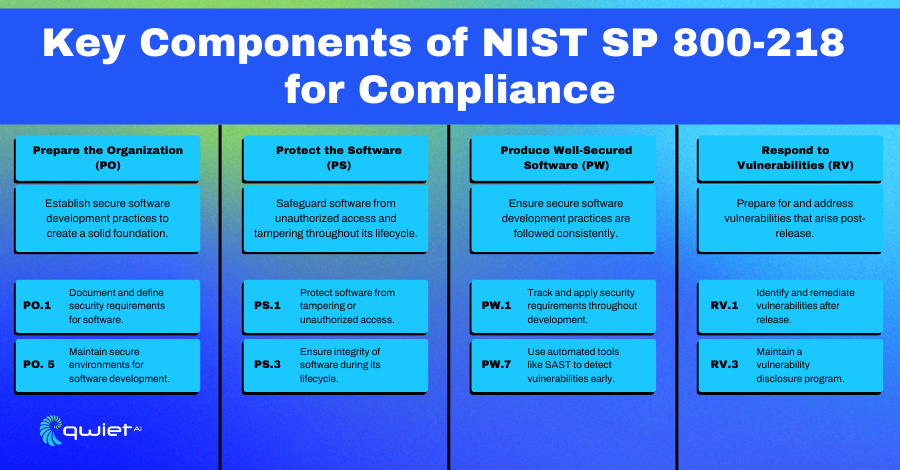
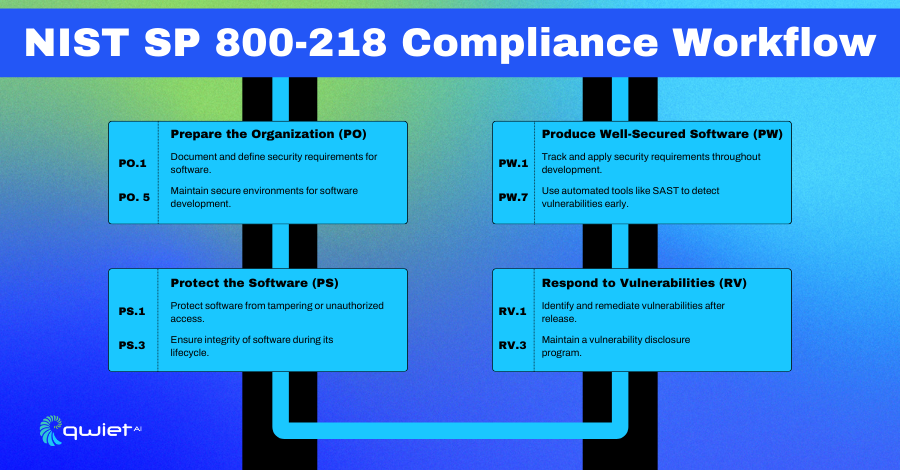
1. Prepare the Organization (PO)
PO.1: Document and define security requirements for software.
To meet NIST SP 800-218 guidelines, starting by clearly documenting all the security requirements for the software you’re developing is important. This means sitting down with your team to identify specific security needs—such as encryption, access controls, and compliance with other regulations—and clearly outlining them from the beginning. This documented set of requirements acts as a roadmap for ensuring that security is baked into every phase of the software development process.
PO.5: Maintain secure environments for software development.
Maintaining secure development environments is crucial to protecting your development process from unauthorized access or interference. This includes implementing access controls, monitoring who has access to your development environment, and using security best practices such as network segmentation and least-privilege access for developers. Regularly review access permissions and audit activities to ensure that only authorized personnel can change the environment, helping prevent tampering or accidental vulnerabilities.
2. Protect the Software (PS)
PS.1: Protect all components of software from tampering or unauthorized access.
It’s important to protect all aspects of your software—the source code, third-party libraries, or dependencies—from unauthorized access or tampering.
You can do this by implementing strict access control policies, using encryption, and digitally signing code to ensure its authenticity. This ensures that only trusted sources can modify or interact with your software, reducing the chance of an attacker tampering with critical components.
PS.3: Implement measures to maintain software integrity during its lifecycle, including secure configurations.
Maintaining your software’s integrity means ensuring that it’s secure not just during development but throughout its entire lifecycle. To do this, secure configurations should be enforced on the production environment, the build pipelines, or the systems that handle deployments.
Regularly auditing these configurations and using tools to monitor the state of your software environments ensures that unauthorized changes are detected quickly and secure settings are always in place.
3. Produce Well-Secured Software (PW)
PW.1: Track and apply security requirements throughout the software development process.
Security requirements shouldn’t be set and forgotten they must be actively tracked and applied throughout the entire software development process. Set up checkpoints at each development phase to verify that your defined security requirements are being met. This can involve regular security reviews, code inspections, and testing to ensure that as the software evolves, it continues to meet the security standards laid out at the start.
PW.7: Use automated security tools such as SAST (Static Application Security Testing) to detect vulnerabilities early.
Implementing automated tools like Static Application Security Testing (SAST) can help you identify vulnerabilities early in development. These tools analyze the source code to detect potential security flaws before executing the software. The earlier you catch vulnerabilities, the cheaper and faster they are to fix, making SAST a critical part of maintaining secure development.
PW.8: Continuously test software to detect security weaknesses, integrating tools like SAST to ensure compliance.
Security testing shouldn’t stop once the software is built—continuous testing is essential to keep up with new vulnerabilities. Tools like SAST and other automated testing methods should be part of your routine. Regularly scanning your code for weaknesses, even after release, ensures that you stay ahead of potential threats and keep your software compliant with NIST’s recommendations.
4. Respond to Vulnerabilities (RV)
RV.1: Implement processes for identifying and remediating vulnerabilities after software release.
Once your software is live, it’s important to have processes for quickly identifying and fixing any emerging vulnerabilities. This means setting up monitoring systems that alert you to potential issues and having a clear patch management process.
When vulnerabilities are discovered through internal monitoring or external reporting, you must respond swiftly to minimize risk and update the software accordingly.
RV.3: Maintain a vulnerability disclosure program to handle reported security issues.
A vulnerability disclosure program is key to getting timely feedback from users and researchers about potential security issues in your software. Having a formal process for receiving and addressing reports of vulnerabilities not only helps you catch issues faster but builds trust with your users.
This program should include clear guidelines on how vulnerabilities can be reported, how they will be handled, and how long it will take to resolve them. This transparency ensures that you’re actively engaged in maintaining the security of your software, even after it’s released.
How to Implement NIST SP 800-218 in Your Organization
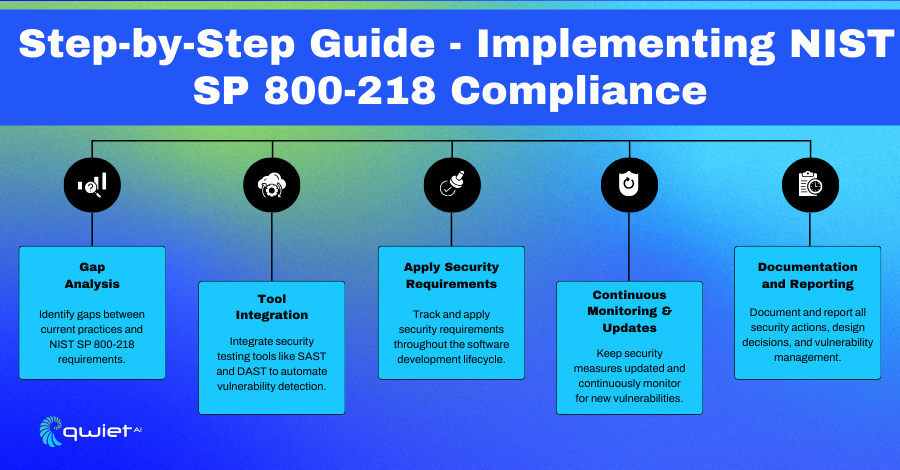
Step 1 – Gap Analysis
Start by doing a gap analysis to see where your current security practices fall short compared to NIST SP 800-218. Look closely at how you handle security across your development process—from setting security requirements to managing vulnerabilities—and see how it aligns with the framework. This will give you a clear picture of what needs to be improved and help you create a plan to fill those gaps.
Step 2 – Tool Integration: Use security testing tools like SAST and DAST
Integrate security testing tools like SAST (Static Application Security Testing) and DAST (Dynamic Application Security Testing) into your workflow. SAST will help catch security issues directly in your source code early on, while DAST tests your application in real-world conditions to find vulnerabilities. Using these tools throughout development helps ensure you’re catching security issues before they become bigger problems.
Step 3 – Continuous Monitoring and Updates
Security threats are constantly changing, so your security measures need to evolve, too. Once you have security tools, use continuous monitoring to monitor your software in real-time. This will help detect any new vulnerabilities that pop up. Regularly update your security configurations, testing protocols, and tools to ensure your defenses stay strong and up to date with the latest threats.
Step 4 – Documentation and Reporting
Don’t forget about documentation it’s a key part of staying compliant with NIST SP 800-218. You need to keep clear records of your security requirements, the tools you’re using, and any decisions made along the way. Documenting your security processes makes it easier to track changes, ensure transparency, and stay prepared for audits. Plus, it gives your team a reference point for maintaining security practices over the long term.
Benefits of NIST SP 800-218 Compliance
Improved Software Security
Following NIST SP 800-218 helps you secure your software by reducing vulnerabilities throughout development. When you build in secure coding practices, regularly test for issues, and manage vulnerabilities early on, your software becomes stronger and better protected. This means fewer risks for your systems and users, and it helps prevent potential security problems.
Enhanced Risk Management
NIST SP 800-218 provides a structured way to identify and reduce security risks. By following the framework, potential vulnerabilities can be caught before they become major threats, helping to protect critical assets. Regular monitoring and solid security practices make you better prepared to manage and respond to any risks that arise, making your organization safer overall.
Competitive Advantage
In industries like government, defense, or critical infrastructure, where security is a major focus, being NIST SP 800-218 compliant can give you an edge. It shows clients and partners that you take security seriously and follow best practices, which can help you stand out. If you aim for contracts or partnerships in high-security sectors, being NIST-compliant can make your organization more attractive and trustworthy.
How Qwiet Helps Map to NIST SP 800-218 Compliance
Qwiet is designed to help organizations stay on top of vulnerability detection and meet NIST SP 800-218 requirements. It automates the process of finding vulnerabilities in your code using static application security testing (SAST) so you can catch and fix issues early in development. By automating these checks, Qwiet helps your team stay focused on building secure software without getting bogged down by manual testing.
How Qwiet Aligns with the SSDF practices of PW.7 and PW.8
Qwiet’s SAST capabilities directly align with NIST SP 800-218’s Secure Software Development Framework (SSDF), specifically practices PW.7 and PW.8. It ensures that secure coding standards are followed throughout the development process and continuously tests for vulnerabilities as the code evolves. This means your team can quickly identify and fix security issues, helping to ensure your software is safe and secure from the start.
Qwiet integrates smoothly into your existing Software Development Life Cycle (SDLC), helping you track and manage vulnerabilities as they arise. It works alongside your development process to maintain secure environments and meet all security requirements. With Qwiet, you can be confident that your software development is aligned with the SSDF framework and NIST SP 800-218 compliance.
Automating Compliance
One of the best parts about Qwiet is that it automates much of the compliance heavy lifting. From detecting vulnerabilities to providing remediation recommendations and generating reports, Qwiet helps ensure everything is handled.
This lightens the load on your development teams, making security a natural part of your workflow while ensuring you meet compliance requirements at every stage of the SDLC.
Conclusion
NIST SP 800-218 offers a clear path for building security into your software development process, reducing risks, and keeping your software safe. We’ve explored why compliance is important, what steps you need to take, and how Qwiet can help automate and streamline your compliance efforts. Ready to simplify your compliance journey and strengthen your security? Reach out to Qwiet and see how we can help you every step of the way.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com
