What is Penetration Testing?
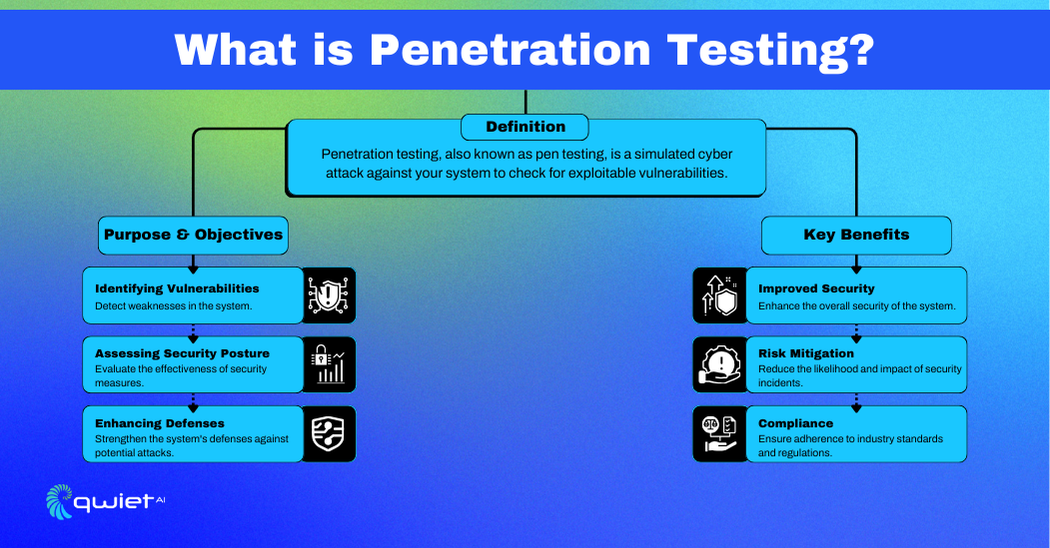
Penetration Testing, or pen testing, is a security practice where experts try to break into your system, network, or application to find weaknesses. This controlled attack helps organizations see where they are vulnerable and fix those issues before real hackers can exploit them.
The main goal of penetration testing is to find and fix security flaws before attackers can exploit them. It helps organizations evaluate the strength of their security measures, identify areas for improvement, and ensure they follow industry regulations. Penetration testing also tests the organization’s ability to handle security breaches and improves its overall security practices.
Penetration testing provides several important benefits, such as helping organizations identify and address security risks, protecting sensitive information, and keeping critical systems safe. It also ensures compliance with industry regulations, avoiding legal and financial problems. By mimicking real attacks, penetration testing improves an organization’s ability to respond to security incidents and strengthens its defenses.
Types of Penetration Testing
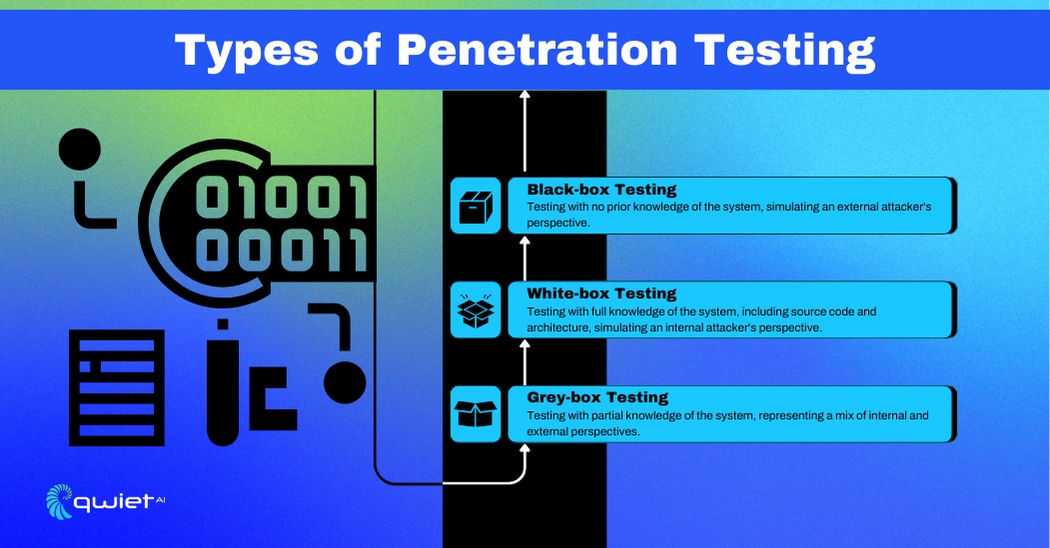
There are several types of penetration testing, each with a unique approach and purpose. These include black-box testing, white-box testing, and grey-box testing.
Black-box Testing
Black-box testing is conducted without prior knowledge of the system’s internal workings. Testers approach the system as an external attacker would, using only publicly available information and their investigative skills. This type of testing is useful for identifying vulnerabilities that could be exploited by attackers who have no insider knowledge of the system.
White-box Testing
White-box testing thoroughly examines the system with full knowledge of its internal structure, source code, and architecture. Testers can access detailed information, allowing for an in-depth assessment of security controls and potential vulnerabilities. This method is typically used to uncover hidden flaws that may not be evident through black-box testing, providing a comprehensive evaluation of the system’s security.
Grey-box Testing
Grey-box testing is a combination of black-box and white-box testing techniques. Testers have partial knowledge of the system, such as access to certain documents or limited insider information. This approach aims to balance the depth of white-box testing and the external perspective of black-box testing. It makes it effective for identifying vulnerabilities that might be overlooked by either method alone.
Penetration Testing Methodologies
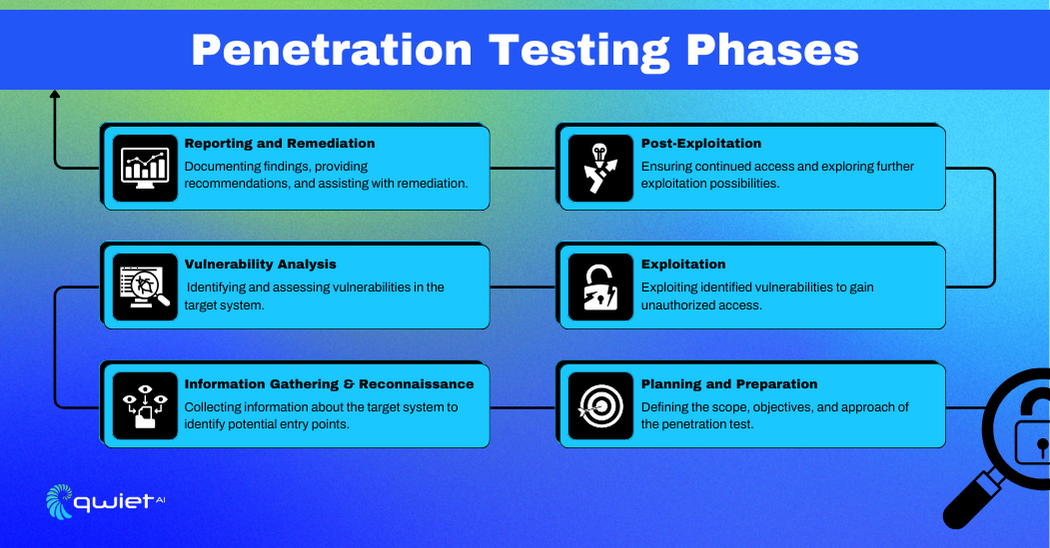
Penetration testing follows a series of steps to evaluate and improve security thoroughly.
Here’s a breakdown of each phase and its importance:
- Planning and Preparation: This first step involves setting the goals, scope, and rules for the test. Everyone agrees on what systems will be tested and how. Good planning ensures the test is organized and effective.
- Information Gathering and Reconnaissance: In this phase, testers gather information about the target system, such as IP addresses and network details. This helps them understand potential vulnerabilities and how to proceed.
- Vulnerability Analysis: Testers analyze the collected information to identify weaknesses in the system. They look for open ports, outdated software, and other security gaps, which helps them prioritize which vulnerabilities to focus on.
- Exploitation: Here, testers try to exploit the identified vulnerabilities to gain access to the system. This shows how an attacker could breach the system and what kind of damage they could do. Successful exploitation highlights critical security flaws.
- Post-exploitation: After gaining access, testers assess what can be done with that access. They check for sensitive data, network access, and other valuable resources. This phase helps understand the potential impact of a real attack.
- Reporting and Remediation: The final step is to document all findings, including details on vulnerabilities and how they were exploited. Testers provide recommendations to fix these issues. Clear reporting helps stakeholders understand the security risks and take action to improve their defenses.
Common Tools Used in Penetration Testing
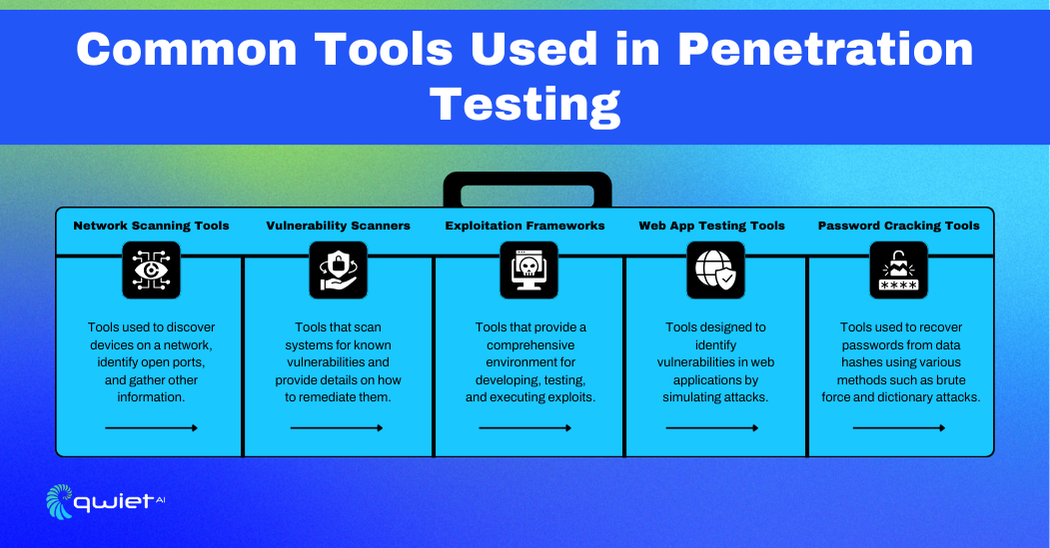
Penetration testing relies on various specialized tools to identify and exploit system vulnerabilities. Here are some of the key tools used by security professionals:
Network Scanning Tools
Network scanning tools like Nmap are important for discovering devices and services on a network. They provide detailed information about network topology, open ports, and running services. Nmap helps testers map the attack surface and identify potential entry points for further investigation.
Vulnerability Scanners
Vulnerability scanners such as Qwiet automate the process of identifying security weaknesses in systems and applications. These tools scan for known vulnerabilities in software, configurations, and network devices, providing a comprehensive list of potential security issues that must be addressed.
Exploitation Framework
Exploitation frameworks like Metasploit provide a platform for developing and executing exploit code against identified vulnerabilities. These tools allow testers to simulate attacks in a controlled environment, demonstrating the potential impact of security flaws and helping to prioritize remediation efforts.
Web Application Testing Tools
Web application testing tools such as OWASP ZAP and Qwiet identify and exploit vulnerabilities in web applications. These tools offer features like automated scanning, manual testing, and web traffic interception, enabling testers to find and exploit security issues in web-based applications.
Password Cracking Tools
Password cracking tools like John the Ripper and Hashcat are used to test the strength of passwords and password policies. These tools employ various techniques, such as brute force and dictionary attacks, to crack passwords and demonstrate how easily weak passwords can be compromised.
Penetration Testing Techniques
Penetration testing employs techniques to assess the security of different systems and environments. These techniques cover a range of attack vectors, providing a holistic view of potential vulnerabilities.
Social Engineering
Social engineering targets the human element of security by attempting to deceive individuals into revealing confidential information or performing actions that compromise security. Techniques include phishing emails, pretexting, and baiting. This approach highlights the importance of employee training and awareness in safeguarding sensitive information.
Network Penetration Testing
Network penetration testing identifies and exploits vulnerabilities within an organization’s network infrastructure. Testers assess devices, protocols, and network services to find weaknesses that could allow unauthorized access or data exfiltration. This technique helps in securing internal and external network boundaries.
Web Application Penetration Testing
Web application penetration testing examines web-based applications for security flaws. Testers use various tools and methods to identify issues such as SQL injection, cross-site scripting (XSS), and insecure authentication mechanisms. This testing ensures that web applications are resilient against attacks that could compromise sensitive data or user accounts.
Wireless Network Penetration Testing
Wireless network penetration testing evaluates the security of an organization’s wireless networks. Testers look for vulnerabilities in Wi-Fi protocols, encryption standards, and access controls. This technique protects against unauthorized access and eavesdropping on wireless communications.
Physical Penetration Testing
Physical penetration testing involves simulating real-world attacks on an organization’s physical security measures. Testers attempt to bypass locks, alarms, and other physical barriers to gain unauthorized access to facilities. This testing helps identify physical security weaknesses that could lead to theft or sabotage of critical assets.
Conclusion
Penetration testing helps find and fix security weaknesses in your systems, networks, and applications. Organizations can use techniques like social engineering and tools like Nmap and Metasploit to protect their data and improve security. Regular testing ensures compliance and stronger defenses. Book a demo to see how Qwiet can help you identify and resolve vulnerabilities.
Read Next
Microservices Security Overview
What is Microservices Security? Microservices security is the comprehensive approach to safeguarding each service within a microservices architecture. In this model, each service functions independently, which creates unique security requirements for each one. To secure these distributed services, microservices security involves methods to protect inter-service communications, secure APIs, and manage access and identity across multiple […]
Security by Design
What is Security by Design? Security by Design is a proactive approach that gives developers a sense of control by integrating security measures into every stage of the software development process. Instead of treating security as an afterthought, this methodology ensures that security considerations are embedded from the initial design phase to deployment and maintenance. […]
Vulnerability Assessment Overview
What is a Vulnerability Assessment? A vulnerability assessment is a thorough check-up of your information systems to find any security weaknesses. This involves identifying, classifying, and prioritizing potential vulnerabilities in your computer systems, networks, and communication channels. The goal is to uncover any weak spots that might be targeted by cyber threats so you can […]