What is Runtime Application Self-Protection (RASP)?
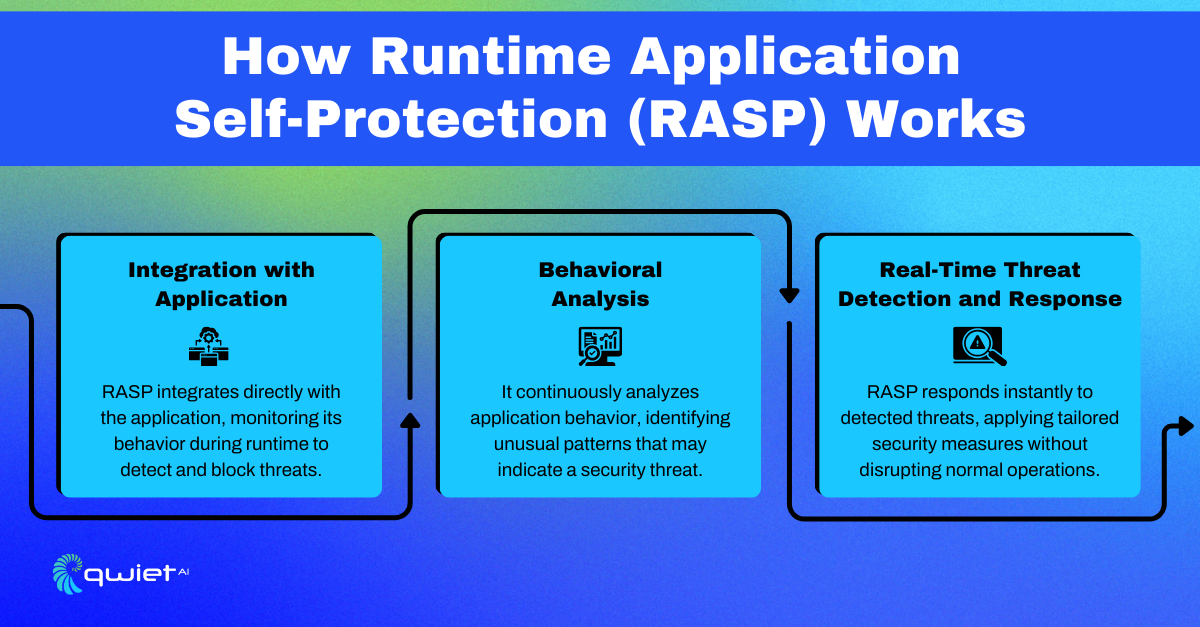
Runtime Application Self-Protection (RASP) is a security solution built directly into an application. It works by monitoring the app’s behavior during its execution, detecting and stopping potential threats in real time. Because it runs inside the application, RASP can provide immediate protection by blocking malicious actions before they cause harm.
RASP integrates with the application, tracking its behavior as it runs. It analyzes the flow of operations to detect any suspicious activity, such as an attempt to exploit a vulnerability.
When RASP identifies a threat, it responds automatically, neutralizing attacks like SQL injection or cross-site scripting (XSS) without disrupting normal application performance.
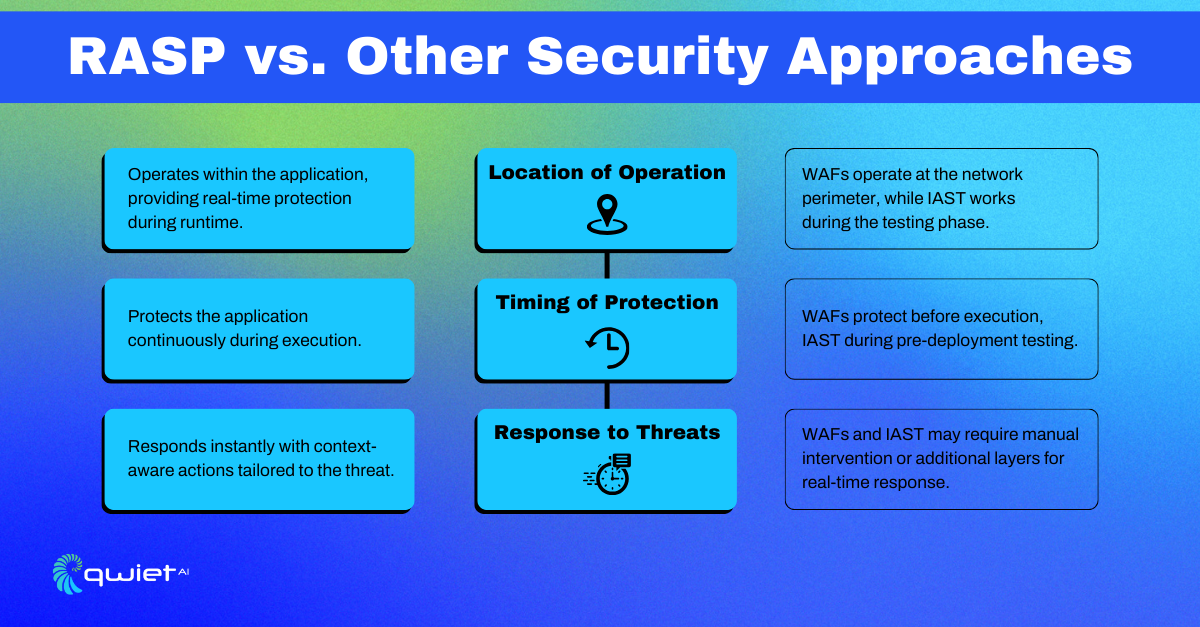
RASP works inside the application, offering protection while the app is running. Web Application Firewalls (WAFs), on the other hand, sit outside the app and filter traffic before it reaches the application.
Interactive Application Security Testing (IAST) is used during the development phase to find vulnerabilities, not to defend against live attacks. RASP differs by continuously monitoring and responding to threats during the app’s actual operation, making it more responsive to runtime attacks.
Why RASP Matters
RASP offers real-time security for applications by actively monitoring and responding to threats during runtime. This makes it particularly effective against attacks that bypass external defenses, such as Web Application Firewalls (WAFs), allowing the application to defend itself while it’s running.
RASP minimizes false positives by analyzing the specific context of detected threats within the application. This allows it to provide tailored, accurate responses to attacks, reduce unnecessary alerts, and focus on real security risks without interrupting normal operations.
RASP continues to protect applications after deployment, constantly monitoring for new threats as they emerge. This ongoing protection ensures the application remains secure even as new vulnerabilities are discovered or attack techniques evolve, offering continuous defense throughout the app’s lifecycle.
Components of RASP
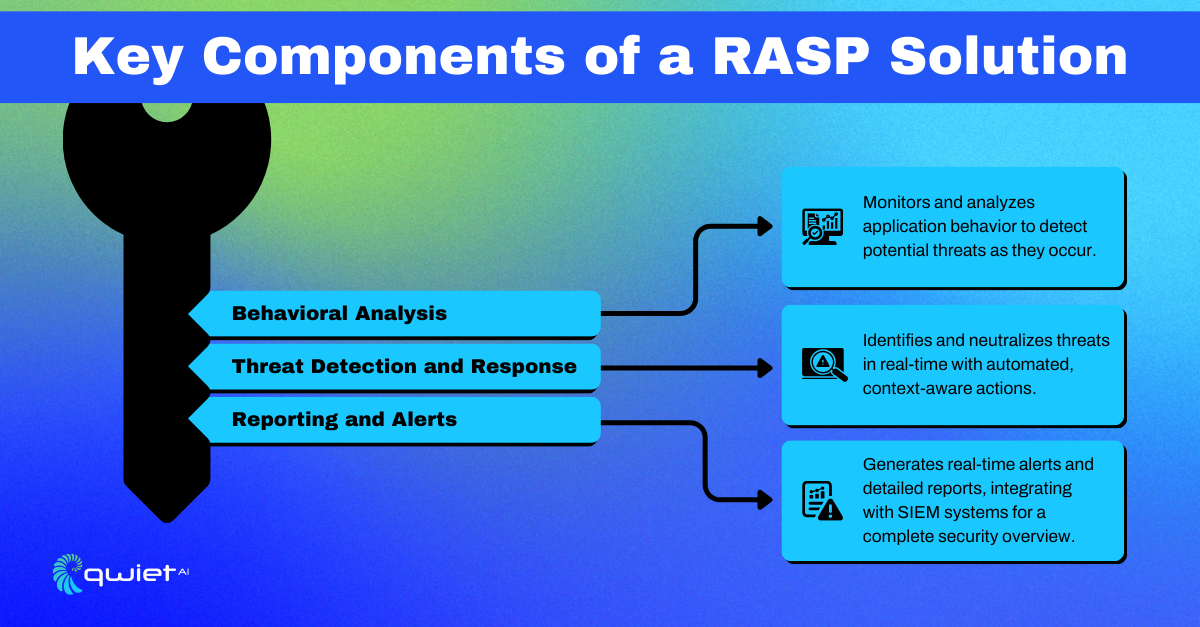
Behavioral Analysis
RASP tools constantly monitor how an application behaves while it’s running. They track data flows, user actions, and system interactions in real-time, looking for anything unusual or out of place. When a potential threat is detected, RASP can immediately block it.
Understanding an application’s normal behavior is critical for spotting sophisticated attacks that other tools might miss. RASP’s ability to analyze behavior in real-time helps detect subtle threats that may not trigger traditional security systems, catching attacks that rely on bypassing usual detection methods.
Threat Detection and Response
RASP identifies attacks like SQL injection or cross-site scripting (XSS) the moment they happen. It can instantly block these threats from affecting the application, stopping the attack before any damage is done—all without needing outside tools or systems to take action.
RASP’s responses are automated and context-aware, meaning they adjust based on the type of threat and what’s happening within the application. This ensures precise and effective action without interrupting normal user activity or slowing down the system.
Reporting and Alerts
RASP tools provide instant alerts and detailed reports when a threat is detected. This helps security teams stay informed and respond quickly to incidents, offering clear insights into what happened and where vulnerabilities may exist.
RASP integrates with SIEM systems and other security tools to give a full view of application security. This connection allows security teams to track and analyze threats across all layers of their systems, improving overall defense and response capabilities.
Conclusion
RASP provides real-time, continuous protection by monitoring an application’s behavior and blocking threats like SQL injection and XSS attacks as they happen. Unlike WAFs and IAST, RASP operates inside the application, allowing it to detect and respond to attacks more effectively while minimizing false positives. It also ensures ongoing security even after deployment, adapting to new threats as they emerge. Book a demo with Qwiet today to enhance your application security.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com
