Key Takeaways
- Secure secret management prevents data leaks and unauthorized access by protecting API keys, database credentials, and encryption keys from exposure.
- Automated secret management tools improve security and efficiency by enforcing access controls, secret rotation, and real-time monitoring.
- AI-driven detection and Code Property Graph (CPG) analysis enhance secret security by identifying hardcoded secrets and reducing false positives.
Introduction
Modern applications depend on APIs, cloud environments, and microservices, making secret management a security priority. API keys, database credentials, and encryption keys are frequently exposed in logs, repositories, or source code, creating high-risk entry points for attackers. This article discusses the risks of poor secret management, best practices for securing sensitive credentials, and modern approaches, such as AI-driven detection and Code Property Graph (CPG) analysis, to enhance security at scale.
What is Secret Management?

Secret management securely stores distributes, and manages sensitive credentials across applications and infrastructure. This includes API keys, database passwords, cloud access tokens, and encryption keys for sensitive data that grant access to systems or services. Proper secret management reduces the risk of unauthorized access, data breaches, and credential leaks by enforcing strict security controls over how secrets are stored and accessed.
Common Types of Secrets in Applications
Applications use various secrets to manage authentication, access control, and secure communication. If these credentials are exposed, they can lead to unauthorized access, data breaches, and compromised systems.
- API Keys & OAuth Tokens: Used for authenticating requests to external services and APIs.
- Authentication Credentials: Includes usernames and passwords for user authentication.
- Database Passwords: Secure database connections by restricting unauthorized access.
- Cloud Access Keys: Provide authentication for cloud services and infrastructure.
- SSH Keys – Enable secure remote access to servers and infrastructure.
- TLS/SSL Certificates: Encrypt data in transit and verify server identities.
- Service Account Credentials: Grant automated processes access to applications and services.
Challenges in Secret Management
One of the biggest challenges in secret management is hardcoding credentials in source code and configuration files. Developers may store secrets in plaintext for convenience, creating a long-term security risk. If these credentials end up in a version control system or a shared repository, attackers scanning for exposed secrets can easily discover them.
Another challenge is the lack of centralized secret management. Without a dedicated system for handling secrets, organizations often rely on ad-hoc storage solutions, leading to fragmented security policies. Some secrets may be stored in plaintext files, while others might be manually shared among teams. This inconsistency makes it difficult to track, audit, and enforce security best practices, increasing the likelihood of accidental exposure or unauthorized access.
Security Risks Associated with Poor Secret Management

Secrets in Public Repositories
Hardcoded secrets in public repositories are among the most common ways credentials get exposed. Developers may accidentally commit API keys, database credentials, or cloud access tokens to repositories like GitHub or GitLab, making them accessible to anyone scanning for sensitive data. Attackers actively search public repositories for exposed secrets, and once discovered, these credentials can be used to gain unauthorized access to services, steal data, or disrupt systems.
Secrets in Logs & CI/CD Pipelines
Sensitive credentials often end up in log files, which can remain unnoticed for long periods. If proper redaction policies are not in place, debug logs, application logs, and audit trails may capture authentication tokens or API keys. If log files are exposed or stored insecurely, this creates a risk of unauthorized access.
CI/CD pipelines are another common exposure point. Automated deployment workflows frequently require access to cloud services, databases, and internal APIs, leading to stored credentials being used. Without secure handling, secrets may be passed as plaintext variables, embedded in pipeline configurations, or stored in build artifacts. If pipeline logs or configurations are exposed, attackers can retrieve these secrets and use them to compromise application environments.
Secrets Sprawl & Insider Threats
When secrets are not managed centrally, they often get distributed across different teams, tools, and environments without proper oversight. This uncontrolled distribution—known as secrets sprawl, makes security enforcement difficult, as it becomes challenging to track where secrets are stored, who has access, and whether they have been properly secured.
Insider threats add another layer of risk. Employees, contractors, or third-party vendors with access to sensitive credentials may misuse them intentionally or accidentally. Malicious insiders may exploit credentials for unauthorized access, while well-intentioned employees may share secrets insecurely or fail to rotate them when required. Organizations face a higher risk of credential leaks and security breaches without proper access controls and monitoring.
Best Practices for Secure Secret Management

Use a Dedicated Secret Management System
Secrets should never be embedded in source code or stored in configuration files. They need to be kept in encrypted vaults that enforce strict access controls and logging. Tools like HashiCorp Vault, AWS Secrets Manager, and Azure Key Vault provide secure storage, automated access policies, and secret expiration mechanisms.
These solutions support API-based retrieval, allowing applications to access credentials dynamically without exposing them in plaintext. They also integrate with hardware security modules (HSMs) and cloud-native encryption services to strengthen key management.
Implement Least Privilege Access Controls
Secrets should only be accessible to the applications and users that require them. Role-Based Access Control (RBAC) and Attribute-Based Access Control (ABAC) should be used to define precise permissions. Policies should be scoped using least privilege principles, restricting credentials to specific environments, services, or identity groups.
Multi-factor authentication (MFA) should be enforced for human access. All retrievals should be logged with contextual metadata, including user identity, access location, and timestamp. Access logs should be integrated with Security Information and Event Management (SIEM) systems to detect anomalies.
Rotate Secrets Regularly
Static secrets increase the risk of unauthorized access if leaked. Secrets should be rotated frequently, and any compromised credentials should be revoked immediately. Automated secret rotation systems can generate new credentials, update dependent services, and invalidate old secrets without manual intervention.
Applications should retrieve secrets dynamically at runtime rather than relying on static environment variables or configuration files. Cloud providers offer built-in secret rotation capabilities, such as AWS Secrets Manager automatic rotation and Kubernetes External Secrets for dynamically fetching and refreshing credentials.
Monitor & Audit Secret Usage
Secret access should be continuously monitored to detect suspicious activity. Every access request should be logged, including details on the requester, the action performed, and the authentication method used. Logs should be forwarded to centralized logging solutions, such as ELK Stack, Splunk, or AWS CloudTrail, for correlation with other security events.
Monitoring systems should trigger alerts when unusual access patterns are detected, such as secrets from unauthorized IP ranges, excessive retrieval attempts, or access outside of defined operational hours. Periodic audits should validate that secrets are properly managed, rotated, and restricted based on least privilege policies.
Secure Secrets in CI/CD Pipelines
Secrets used in CI/CD workflows must be stored and retrieved securely in logs or configuration files without exposure. Instead of hardcoding credentials in pipeline scripts, secret management tools should be integrated to inject secrets dynamically during runtime. CI/CD platforms like GitHub Actions, GitLab CI, and Jenkins offer built-in secret management features that encrypt credentials and restrict access based on job permissions.
Kubernetes environments should use solutions like the HashiCorp Vault injector or the Kubernetes Secrets Store CSI Driver to mount secrets securely as environment variables or ephemeral files. To prevent secrets from being accidentally recorded or leaked, all CI/CD pipeline logs should be sanitized.
Modern Approaches to Secret Management in AppSec
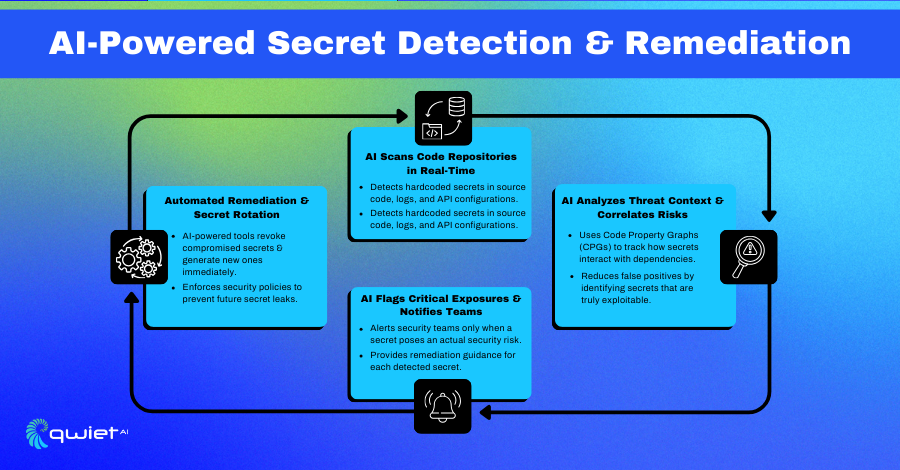
Code Property Graph (CPG) Analysis for Secret Detection
Advanced security tools use Code Property Graph (CPG) analysis to identify hardcoded secrets by mapping code structure and tracking data flow. This method detects credentials embedded in source code, configuration files, and environment variables by analyzing how sensitive data moves through an application. The CPG-based analysis extends beyond static detection by assessing how secrets interact with dependencies, helping security teams pinpoint potential exposure risks before they become exploitable.
AI-Driven Secret Scanning
Machine learning models enhance secret detection by analyzing code, logs, and infrastructure configuration patterns. AI-driven scanning tools monitor repositories, CI/CD pipelines, and cloud environments for exposed credentials.
These models reduce false positives by distinguishing between real secrets and similar-looking strings, allowing security teams to focus on high-confidence findings. AI-powered scanners learn from past incidents, improving accuracy and adapting to evolving threats.
Real-Time Secret Validation & Threat Correlation
Modern secret management platforms integrate with threat intelligence sources to validate exposed credentials in real-time. When a leaked secret is detected, it is automatically cross-referenced with known attack indicators, breach databases, and adversary tactics.
This correlation helps security teams prioritize remediation by determining whether a secret has already been compromised or if it is actively being used in an attack. Real-time validation enhances visibility by mapping secret exposure to real-world security threats.
Automated Remediation & Response
Security automation platforms help contain exposure by revoking compromised secrets and issuing alerts when a credential is leaked. Automated workflows trigger secret rotation, disable affected access tokens, and enforce policy-based access controls.
Integration with DevSecOps pipelines allows organizations to securely manage secrets throughout the software development lifecycle (SDLC). Automated response mechanisms minimize human error and reduce the time between detection and mitigation, lowering the risk of unauthorized access.
Conclusion
Strong secret management prevents credential leaks, unauthorized access, and compliance violations. Traditional methods leave security gaps, while automated solutions provide real-time detection, monitoring, and enforcement. AI-driven scanning and Code Property Graph (CPG) analysis enhances protection by identifying risks before they become threats. Ready to improve your security strategy? Book a demo with Qwiet today.
FAQs
What is secret management in application security?
Secret management involves securely storing, distributing, and managing sensitive credentials such as API keys, database passwords, and encryption keys to prevent unauthorized access and data leaks.
Why is secret management important for AppSec?
Exposed secrets can lead to data breaches, supply chain attacks, and system compromises. Strong secret management practices reduce these risks and help maintain compliance with security regulations.
What are the best practices for secure secret management?
Key practices for reducing exposure risks include using encrypted secret management systems, enforcing least privilege access, automating secret rotation, monitoring secret usage, and securing CI/CD pipelines.
How do AI and Code Property Graphs (CPGs) improve secret security?
AI-driven scanning detects hardcoded secrets in real-time, while CPG analysis maps code structure and data flow to identify hidden risks and prevent credential leaks.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com
