Introduction
Ever wondered how to keep your Java applications safe from prying eyes and cyber threats? This blog post dives into Java Secure Socket Extension (JSSE), a powerful tool for securing communications in your Java applications. We’ll explore the features and configurations of JSSE, showing you how to establish secure socket communications to protect your data. By reading this, you’ll learn to set up JSSE, create secure sockets, handle SSL exceptions, and use SAST tools to strengthen your application’s security.
Setting Up JSSE
Environment Setup
Before diving into JSSE, you need to set up your environment properly. Ensure that you have JDK 8 or later installed, as JSSE is a part of the Java platform starting from Java 1.4. Verify your JDK installation by running java -version in your terminal or command prompt. This confirms that you have the correct version of Java.
| java –version |
JDK Requirements
Using JSSE requires JDK 8 or higher. The Java Secure Socket Extension is included with the Java Development Kit, so you don’t need to download any additional libraries. Having JDK 8 or later ensures you have all the necessary tools and libraries to work with JSSE.
| javac –version |
Configuring Your Development Environment
To configure your development environment for JSSE, ensure your IDE is set up to work with the JDK version installed on your system.
Set the project SDK to match your installed JDK if you’re using an IDE like IntelliJ IDEA, Eclipse, or NetBeans. Additionally, ensure your environment variables (like JAVA_HOME) point to the correct JDK installation path.
| export JAVA_HOME=/path/to/your/jdk export PATH=$JAVA_HOME/bin:$PATH |
Importing Necessary Packages
JSSE utilizes several packages to enable secure socket communications. Here are the primary packages you’ll need:
- javax.net.ssl: Provides classes for SSL sockets.
- java.security: Contains classes for key management and encryption.
- java.security.cert: Used for handling certificates.
Import these packages at the beginning of your Java program to access JSSE functionalities.
| import javax.net.ssl.SSLServerSocketFactory; import javax.net.ssl.SSLServerSocket; import javax.net.ssl.SSLSocketFactory; import javax.net.ssl.SSLSocket; import javax.net.ssl.SSLContext; import java.security.KeyStore; import java.security.cert.CertificateException; |
Setting up your environment and importing these packages, you can start implementing secure communications in your Java applications.
Key Concepts in JSSE
SSL/TLS Protocols
SSL (Secure Sockets Layer) and TLS (Transport Layer Security) are protocols designed to secure communications over a computer network. They encrypt the data transmitted between the client and the server, ensuring that unauthorized parties cannot read or tamper with any intercepted data. TLS is the successor to SSL and offers improved security and performance.
Importance of SSL/TLS in Securing Communication
Using SSL/TLS protocols is fundamental for protecting sensitive information during transmission. They ensure data integrity, confidentiality, and authenticity, crucial for preventing eavesdropping, data breaches, and man-in-the-middle attacks.
By implementing these protocols, applications can provide a secure channel for data exchange, which is particularly important for applications handling financial transactions, personal information, and other sensitive data.
Certificates and KeyStores
Digital certificates are electronic documents used to prove the ownership of a public key. They are issued by a Certificate Authority (CA) and contain the public key and information about the key owner and the CA. Certificates are crucial in establishing a trusted relationship between parties in a secure communication.
Types of KeyStores
- JKS (Java KeyStore): The default KeyStore type in Java, designed to store private keys and certificates. It is proprietary to Java.
- PKCS12: A standard format for storing private keys and certificates, designed for compatibility across different platforms and applications. It uses a password-based encryption scheme to protect the keys and certificates.
Code Snippet: Loading a KeyStore
Here’s a simple example of how to load a KeyStore in Java:
| import java.io.FileInputStream; import java.security.KeyStore; public class KeyStoreExample { public static void main(String[] args) { try { // Load the KeyStore KeyStore keyStore = KeyStore.getInstance(“JKS”); FileInputStream fis = new FileInputStream(“keystore.jks”); keyStore.load(fis, “password”.toCharArray()); fis.close(); // Access the KeyStore entries KeyStore.ProtectionParameter param = new KeyStore.PasswordProtection(“password”.toCharArray()); KeyStore.PrivateKeyEntry entry = (KeyStore.PrivateKeyEntry) keyStore.getEntry(“alias”, param); // Print certificate details System.out.println(entry.getCertificate()); } catch (Exception e) { e.printStackTrace(); } } } |
This snippet demonstrates how to load a Java KeyStore, access an entry, and print the certificate details. Make sure to replace “keystore.jks”, “password”, and “alias” with your actual KeyStore file, password, and alias.
Creating Secure Sockets
To create a secure server socket, you need to configure an SSLServerSocket that will listen for incoming SSL/TLS connections. This involves setting up an SSLContext, which acts as a factory for secure socket factories.
You’ll configure the SSLContext with the necessary key and trust material and then use it to create an SSLServerSocketFactory for your server socket.
Setting up the SSLContext requires specifying the protocol (such as TLS) and initializing it with key managers and trust managers. These managers handle the authentication and encryption details. Once the SSLContext is initialized, you can create and configure your SSLServerSocket to accept secure connections.
Code Snippet: Initializing SSLContext and Setting Up SSLServerSocket
| import javax.net.ssl.*; import java.io.FileInputStream; import java.security.KeyStore; public class SecureServerSocketExample { public static void main(String[] args) { try { // Load KeyStore KeyStore keyStore = KeyStore.getInstance(“JKS”); FileInputStream keyStoreStream = new FileInputStream(“keystore.jks”); keyStore.load(keyStoreStream, “password”.toCharArray()); keyStoreStream.close(); // Set up key manager factory KeyManagerFactory keyManagerFactory = KeyManagerFactory.getInstance(“SunX509”); keyManagerFactory.init(keyStore, “password”.toCharArray()); // Initialize SSLContext SSLContext sslContext = SSLContext.getInstance(“TLS”); sslContext.init(keyManagerFactory.getKeyManagers(), null, null); // Create SSLServerSocket SSLServerSocketFactory sslServerSocketFactory = sslContext.getServerSocketFactory(); SSLServerSocket sslServerSocket = (SSLServerSocket) sslServerSocketFactory.createServerSocket(8443); // Configure SSLServerSocket sslServerSocket.setEnabledProtocols(new String[] {“TLSv1.2”}); sslServerSocket.setNeedClientAuth(true); System.out.println(“Secure server socket created, waiting for connections…”); SSLSocket sslSocket = (SSLSocket) sslServerSocket.accept(); // Handle client connection } catch (Exception e) { e.printStackTrace(); } } } |
In this example, a KeyStore is loaded from a file, and a KeyManagerFactory is set up with it. The SSLContext is then initialized with the key managers. The SSLServerSocketFactory created from this context creates an SSLServerSocket on port 8443. The server socket is configured to use TLS 1.2 and to require client authentication.
Creating a Secure Client Socket
Creating a secure client socket involves configuring an SSLSocket to connect to a secure server. Like the server setup, you initialize an SSLContext and use it to create an SSLSocketFactory. The socket factory then creates an SSLSocket, which can connect to the server securely.
Code Snippet: Initializing SSLContext and Setting Up SSLSocket
| import javax.net.ssl.*; import java.io.FileInputStream; import java.security.KeyStore; public class SecureClientSocketExample { public static void main(String[] args) { try { // Load TrustStore KeyStore trustStore = KeyStore.getInstance(“JKS”); FileInputStream trustStoreStream = new FileInputStream(“truststore.jks”); trustStore.load(trustStoreStream, “password”.toCharArray()); trustStoreStream.close(); // Set up trust manager factory TrustManagerFactory trustManagerFactory = TrustManagerFactory.getInstance(“SunX509”); trustManagerFactory.init(trustStore); // Initialize SSLContext SSLContext sslContext = SSLContext.getInstance(“TLS”); sslContext.init(null, trustManagerFactory.getTrustManagers(), null); // Create SSLSocket SSLSocketFactory sslSocketFactory = sslContext.getSocketFactory(); SSLSocket sslSocket = (SSLSocket) sslSocketFactory.createSocket(“localhost”, 8443); // Start SSL handshake sslSocket.startHandshake(); System.out.println(“Secure client socket connected to server.”); // Handle server communication } catch (Exception e) { e.printStackTrace(); } } } |
In this client-side example, a TrustStore is loaded, and a TrustManagerFactory is set up. The SSLContext is initialized with trust managers. An SSLSocketFactory created from this context is used to create an SSLSocket that connects to a server running on localhost at port 8443. The client socket starts the SSL handshake to establish a secure connection with the server.
Mutual Authentication and Exception Handling
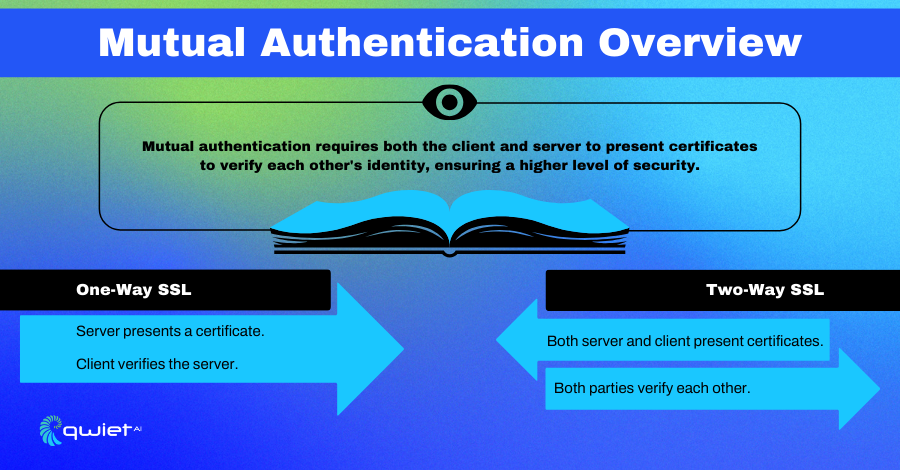
Mutual authentication enhances security by requiring the client and the server to authenticate each other. This means that not only does the client need to trust the server, but the server must also trust the client. Mutual authentication is often used in environments where trust needs to be bidirectional, such as in banking or secure enterprise applications.
Explanation and Configuration
To configure mutual authentication, you need to ensure that both the server and the client have their key pairs and corresponding certificates. On the server side, you configure the SSLServerSocket to request client authentication by calling setNeedClientAuth(true). On the client side, you need to load the client’s key store into the SSLContext to provide the necessary credentials during the SSL handshake.
Code Snippet: Configuring Mutual Authentication for SSLServerSocket and SSLSocket
| import javax.net.ssl.*; import java.io.FileInputStream; import java.security.KeyStore; public class MutualAuthExample { public static void main(String[] args) { try { // Load Server KeyStore KeyStore serverKeyStore = KeyStore.getInstance(“JKS”); FileInputStream serverKeyStoreStream = new FileInputStream(“server_keystore.jks”); serverKeyStore.load(serverKeyStoreStream, “serverpassword”.toCharArray()); serverKeyStoreStream.close(); // Set up server key manager factory KeyManagerFactory serverKeyManagerFactory = KeyManagerFactory.getInstance(“SunX509“); serverKeyManagerFactory.init(serverKeyStore, “serverpassword”.toCharArray()); // Load TrustStore for Server KeyStore serverTrustStore = KeyStore.getInstance(“JKS“); FileInputStream serverTrustStoreStream = new FileInputStream(“server_truststore.jks”); serverTrustStore.load(serverTrustStoreStream, “trustpassword”.toCharArray()); serverTrustStoreStream.close(); // Set up server trust manager factory TrustManagerFactory serverTrustManagerFactory = TrustManagerFactory.getInstance(“SunX509“); serverTrustManagerFactory.init(serverTrustStore); // Initialize SSLContext for Server SSLContext serverSSLContext = SSLContext.getInstance(“TLS“); serverSSLContext.init(serverKeyManagerFactory.getKeyManagers(), serverTrustManagerFactory.getTrustManagers(), null); // Create SSLServerSocket SSLServerSocketFactory sslServerSocketFactory = serverSSLContext.getServerSocketFactory(); SSLServerSocket sslServerSocket = (SSLServerSocket) sslServerSocketFactory.createServerSocket(8443); sslServerSocket.setNeedClientAuth(true); // Enable client authentication System.out.println(“Server ready for mutual authentication…”); // Load Client KeyStore KeyStore clientKeyStore = KeyStore.getInstance(“JKS“); FileInputStream clientKeyStoreStream = new FileInputStream(“client_keystore.jks”); clientKeyStore.load(clientKeyStoreStream, “clientpassword”.toCharArray()); clientKeyStoreStream.close(); // Set up client key manager factory KeyManagerFactory clientKeyManagerFactory = KeyManagerFactory.getInstance(“SunX509“); clientKeyManagerFactory.init(clientKeyStore, “clientpassword”.toCharArray()); // Load TrustStore for Client KeyStore clientTrustStore = KeyStore.getInstance(“JKS“); FileInputStream clientTrustStoreStream = new FileInputStream(“client_truststore.jks”); clientTrustStore.load(clientTrustStoreStream, “trustpassword”.toCharArray()); clientTrustStoreStream.close(); // Set up client trust manager factory TrustManagerFactory clientTrustManagerFactory = TrustManagerFactory.getInstance(“SunX509“); clientTrustManagerFactory.init(clientTrustStore); // Initialize SSLContext for Client SSLContext clientSSLContext = SSLContext.getInstance(“TLS“); clientSSLContext.init(clientKeyManagerFactory.getKeyManagers(), clientTrustManagerFactory.getTrustManagers(), null); // Create SSLSocket SSLSocketFactory sslSocketFactory = clientSSLContext.getSocketFactory(); SSLSocket sslSocket = (SSLSocket) sslSocketFactory.createSocket(“localhost”, 8443); sslSocket.startHandshake(); // Start SSL handshake System.out.println(“Client and server mutually authenticated.”); } catch (Exception e) { e.printStackTrace(); } } } |
This example shows how to configure mutual authentication. The server loads its key and trust stores, sets up the key and trust managers, and initializes the SSLContext. It then creates an SSLServerSocket and enables client authentication. Similarly, the client loads its key store and trust store, sets up the key and trust managers, and initializes the SSLContext to create an SSLSocket. The client starts the handshake process to establish a mutually authenticated connection.
Handling SSL Exceptions
Effectively handling SSL exceptions is important for maintaining secure communication. Common SSL exceptions include SSLHandshakeException, SSLPeerUnverifiedException, and SSLProtocolException. These exceptions typically indicate issues with certificate validation, mismatched protocols, or problems during the SSL handshake process.
Debugging SSL Issues
Debugging SSL issues can be challenging, but enabling detailed logging can help. You can enable SSL debugging in Java by setting the javax.net.debug system property to all.
This provides comprehensive logs of the SSL handshake and other operations, which can help identify the root cause of issues. Additionally, verifying your key store and trust store configurations, checking for expired or misconfigured certificates, and ensuring protocol compatibility can resolve many common problems.
| // Enable SSL debugging System.setProperty(“javax.net.debug”, “all”); |
Including this line in your application, you can generate detailed SSL debug output, which will help you troubleshoot and resolve SSL-related issues.
How a SAST Tool Can Help Secure Your Java Application
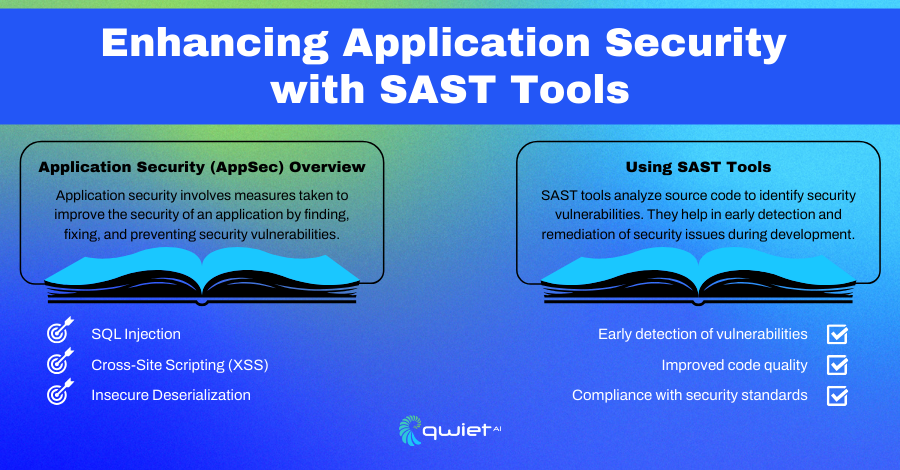
Adding a Static Application Security Testing (SAST) tool to your development process can help secure your Java applications. SAST tools scan your source code, bytecode, or binaries to find security vulnerabilities without running the program.
They catch common issues like SQL injection, cross-site scripting (XSS), and insecure cryptographic practices. By catching these problems early in the development cycle, SAST tools help you fix security flaws before your application goes live, which means fewer headaches and lower costs.
Using a SAST tool also helps your development team adopt better security practices. These tools provide detailed reports and suggestions for fixing issues, making it easier for developers to understand and address security concerns.
Conclusion
In this post, we covered how to secure your Java applications using JSSE, from setting up your environment and understanding SSL/TLS protocols to creating secure sockets and handling SSL exceptions. Implementing JSSE is a key step in making your Java applications more secure. If you’re ready to take your application’s security to the next level, Qwiet.ai is here to help. Book a call with us today to ensure your applications are protected from cyber threats.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com
