What is Threat Modeling?
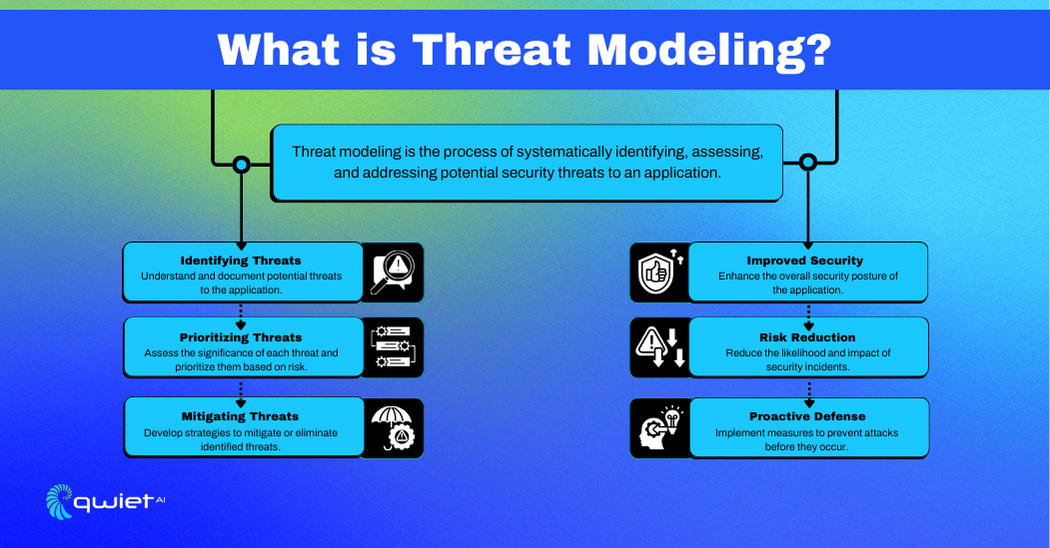
Threat modeling is a way to find and fix potential security problems in a system. We can understand how attackers might take advantage of these issues by looking at how the system is built and spotting weak points. This helps us get a clear view of the system’s security and identify areas that need improvement.
The main goal of threat modeling is to secure systems and applications by predicting and dealing with possible threats before they can cause damage. This involves finding important assets, understanding how they might be attacked, and assessing the impact of these attacks. By including threat modeling in the software development process, we can build security into the system from the start, reducing the risk of breaches and helping meet regulatory standards.
Threat modeling offers several important benefits. It helps find and fix security issues early, which saves time and money compared to dealing with them after the system is deployed. It also raises security awareness among development and operations teams, promoting a security-first mindset. Additionally, it helps prioritize security tasks based on their impact and likelihood, ensuring that the most critical threats are addressed first and resources are used effectively.
Concepts in Threat Modeling
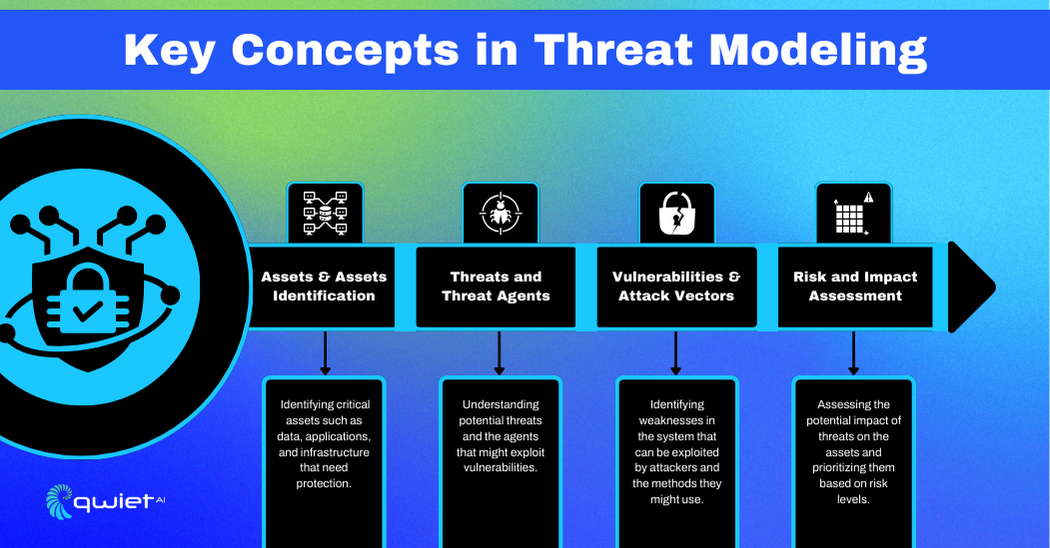
Threat modeling encompasses several key concepts important for understanding and mitigating security threats. These concepts include identifying assets, understanding threats and threat agents, pinpointing vulnerabilities and attack vectors, and assessing risks and their impacts. Each of these elements plays a significant role in creating a secure system.
Assets and Assets Identification
Assets are valuable system components that need protection, such as data, applications, and infrastructure. Identifying these assets involves determining what needs safeguarding and prioritizing them based on their importance to the organization. This step is fundamental in understanding what potential attackers might target and why these assets are attractive.
Threats and Threat Agents
Threats are potential events or actions that could harm the system, while threat agents are entities that could exploit vulnerabilities to carry out these threats. Identifying threats and threat agents involves analyzing possible attack scenarios and understanding who might be motivated to exploit weaknesses in the system. This helps anticipate potential security breaches and prepare appropriate defenses.
Vulnerabilities and Attack Vectors
Vulnerabilities are weaknesses in a system that could be exploited by threat agents, while attack vectors are the paths or methods used to carry out these exploits. Identifying vulnerabilities and attack vectors involves a thorough examination of the system’s architecture, code, and configurations to uncover weaknesses that could be targeted. This step is crucial for developing strategies to mitigate these vulnerabilities and protect the system.
Risk and Impact Assessment
Risk and impact assessment involves evaluating the potential consequences of identified threats exploiting vulnerabilities. This process includes determining the likelihood of different attack scenarios and the potential damage they could cause the organization. By assessing risks and impacts, organizations can prioritize their security efforts and allocate resources effectively to address the most significant threats.
Threat Modeling Methodologies
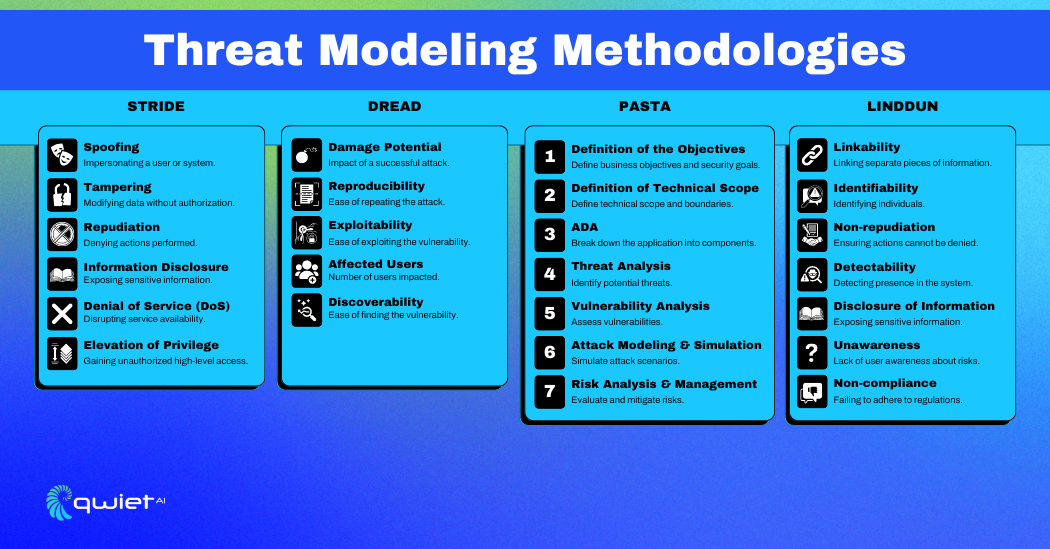
Threat modeling methodologies provide structured ways to identify and address potential security threats. Each method offers a different approach, helping security professionals choose the best one for their needs. Here, we explore five popular methodologies: STRIDE, DREAD, PASTA, LINDDUN, and Attack Trees.
STRIDE (Spoofing, Tampering, Repudiation, Information Disclosure, Denial of Service, Elevation of Privilege)
STRIDE is a method created by Microsoft to identify and categorize security threats. It breaks threats into six types: Spoofing (pretending to be someone else), Tampering (altering data), Repudiation (denying actions), Information Disclosure (exposing information), Denial of Service (disrupting services), and Elevation of Privilege (gaining unauthorized access). By looking at these categories, STRIDE helps spot vulnerabilities and implement security measures to address them.
DREAD (Damage, Reproducibility, Exploitability, Affected Users, Discoverability)
DREAD is a model used to evaluate and prioritize threats based on five criteria: Damage (potential impact), Reproducibility (ease of replication), Exploitability (ease of exploitation), Affected Users (number of users impacted), and Discoverability (ease of discovery). Each threat is scored on these criteria, providing a way to compare and prioritize them, helping to focus on the most serious threats first.
PASTA (Process for Attack Simulation and Threat Analysis)
PASTA is a methodology that focuses on simulating attacks to understand their impact. It has seven stages: defining business objectives, defining technical scope, breaking down the application, analyzing threats, examining vulnerabilities, modeling attacks, and managing risks. PASTA aligns security needs with business goals, ensuring threat modeling is part of the overall risk management strategy.
LINDDUN (Linkability, Identifiability, Non-repudiation, Detectability, Disclosure of Information, Unawareness, Non-compliance)
LINDDUN is a method focused on identifying privacy threats in software systems. It classifies threats into seven categories: Linkability (connecting different data sets), Identifiability (identifying individuals), Non-repudiation (denying actions), Detectability (detecting actions or data), Disclosure of Information (revealing sensitive data), Unawareness (lack of user awareness), and Non-compliance (violating privacy regulations). LINDDUN ensures privacy is considered throughout the threat modeling process.
Attack Trees
Attack Trees are a visual way to map out how an attacker might exploit system vulnerabilities. The tree starts with a main goal, like gaining unauthorized access, and branches into various sub-goals and attack paths. Each branch shows a different attack method, making seeing and analyzing potential threats easier. Attack Trees help understand threats’ complexity and develop effective mitigation strategies.
Steps in the Threat Modeling Process
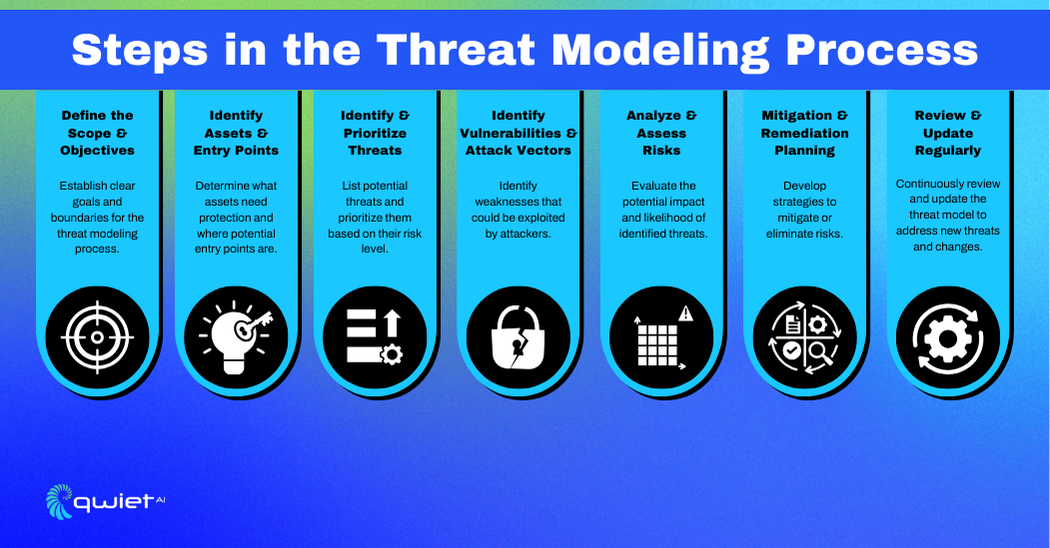
The threat modeling process helps identify and address potential security threats systematically. Each step builds on the previous one to create a strong security strategy. Here are the key steps:
- Define the Scope and Objectives
Start by outlining what parts of the system you will focus on and set clear security goals. This helps ensure that you’re considering all relevant components and know exactly what you aim to protect. Defining scope and objectives gives direction to the entire threat modeling process.
- Identify Assets and Entry Points
Identify critical assets like data, applications, and infrastructure, and pinpoint where attackers might gain access. Knowing what needs protection and how attackers might get in helps prioritize security measures on the most valuable and vulnerable parts of the system.
- Identify and Prioritize Threats
List potential threats and rank them by importance. This way, you can focus on the most serious risks first. Prioritizing threats ensures that your security efforts target the most pressing issues, making your system safer.
- Identify Vulnerabilities and Attack Vectors
Examine the system to find weaknesses that could be exploited and the methods attackers might use. Understanding these vulnerabilities and attack paths is crucial for developing effective defenses and preventing potential breaches.
- Analyze and Assess Risks
Evaluate the potential consequences if threats exploit vulnerabilities. Consider both how likely an attack is and what the impact would be. This helps prioritize which risks to address first, ensuring you focus on the most significant threats.
- Mitigation and Remediation Planning
Develop and implement strategies to reduce risks and fix vulnerabilities. This could include technical fixes, policy changes, or process improvements. Effective planning and action lower the system’s overall risk and enhance security.
- Review and Update Regularly
Threat modeling should be an ongoing effort. Review and update your findings regularly to stay ahead of new threats and ensure current measures are still effective. Continuous improvement keeps your system secure over time.
Conclusion
We’ve covered threat modeling, explaining its purpose, benefits, key concepts like asset identification and risk assessment, and methods such as STRIDE, DREAD, PASTA, LINDDUN, and Attack Trees. We also talked about how to integrate threat modeling into the SDLC through early-stage and continuous assessments and team collaboration. Effective threat modeling is important for building secure systems and promoting a security-first mindset.
To improve your security posture, schedule a demo call for Qwiet to help you find and fix vulnerabilities.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com
