What is a Vulnerability Assessment?
A vulnerability assessment is a thorough check-up of your information systems to find any security weaknesses. This involves identifying, classifying, and prioritizing potential vulnerabilities in your computer systems, networks, and communication channels. The goal is to uncover any weak spots that might be targeted by cyber threats so you can take steps to fix them and boost your overall security.
Performing vulnerability assessments regularly is important for keeping your organization’s digital assets secure. The main objective is to spot and fix security flaws before anyone with bad intentions can exploit them.
Vulnerability assessments play a crucial role in protecting your organization’s sensitive data and ensuring compliance with industry regulations. By conducting these assessments regularly, you can stay ahead of potential threats and continually strengthen your security measures.
Key Components of Vulnerability Assessment
Asset Inventory
The first step in a vulnerability assessment is to identify all assets, such as systems, applications, and networks. This involves cataloging everything connected to your IT environment to ensure every potential entry point is noticed.
Maintaining an up-to-date inventory is important because it ensures that all assets are accounted for and monitored. An accurate inventory also helps quickly identify and address any vulnerabilities that might arise.
Vulnerability Identification
Methods to identify vulnerabilities include automated tools and manual testing. Automated tools can quickly scan large environments, while manual testing allows security experts to perform a more detailed and nuanced analysis.
Common vulnerabilities often include misconfigurations, outdated software, and weak passwords. If not properly managed and secured, these issues can provide easy access points for attackers.
Vulnerability Analysis
Assessing the impact and exploitability of identified vulnerabilities helps to understand each weakness’s potential consequences. This analysis is crucial for deciding how to address each vulnerability effectively.
Categorizing vulnerabilities based on severity helps prioritize remediation efforts. High-severity vulnerabilities that pose significant risks are dealt with first, ensuring the most dangerous threats are neutralized quickly.
Risk Evaluation
Determining the potential impact of vulnerabilities on business operations is an important aspect of risk evaluation. This step assesses how a security breach could affect your organization’s functionality and data integrity.
Prioritizing vulnerabilities based on risk ensures that resources are allocated efficiently. By focusing on the most pressing threats, you can mitigate risks that could have the most severe consequences for your organization.
Reporting
Documenting findings in a detailed report provides a clear overview of identified vulnerabilities and their implications. This report serves as a reference for understanding the current security posture.
The final step is to provide actionable recommendations for remediation. These suggestions guide the organization in fixing identified issues and improving overall security, ensuring vulnerabilities are effectively addressed.
Types of Vulnerability Assessments
Network-based Assessments
Network-based assessments focus on scanning and analyzing the network infrastructure for weaknesses. This assessment helps identify vulnerabilities in network devices such as routers, switches, firewalls, and other components that make up the network. By evaluating these devices, you can pinpoint security gaps that could be exploited by attackers to gain unauthorized access or disrupt services.
Host-based Assessments
Host-based assessments involve evaluating individual systems and servers for vulnerabilities. This type of assessment examines the security posture of each host to identify weaknesses such as outdated software, misconfigurations, and weak passwords. It also checks for unauthorized access points and suspicious activity that could indicate a compromise.
Application-based Assessments
Application-based assessments focus on identifying vulnerabilities in web and mobile applications. They are designed to uncover security flaws such as SQL injection, cross-site scripting (XSS), and other common vulnerabilities that attackers can exploit to gain access to sensitive data or take control of the application.
Database Assessments
Database assessments aim to assess databases for security flaws and misconfigurations. They examine the database management systems (DBMS) to identify vulnerabilities such as improper access controls, insecure configurations, and outdated software that could be exploited by attackers.
Tools and Technologies for Vulnerability Assessment
Automated Scanners
Automated scanners are powerful tools that help quickly identify vulnerabilities across your systems. These scanners, like Qwiet are designed to run comprehensive checks on networks, applications, and devices. They can identify security issues, from outdated software to misconfigurations, and provide detailed reports on their findings. Automated scanners allow for efficient and thorough vulnerability assessments, especially in large and complex IT environments.
One of the main advantages of automated scanners is their ability to perform regular scans without much manual intervention. This means you can schedule regular scans, ensuring you consistently monitor your systems for new vulnerabilities. The detailed reports generated by these scanners help understand the vulnerabilities and the steps needed to remediate them.
Manual Testing
Manual testing, particularly through penetration testing techniques, involves security experts actively trying to exploit vulnerabilities in your systems. Unlike automated scanners, penetration testing is more in-depth and can uncover vulnerabilities that automated tools might miss. Penetration testers use techniques to simulate real-world attacks, providing a clearer picture of how an attacker might exploit your systems’ weaknesses.
While automated tools are efficient, they sometimes generate false positives or miss complex vulnerabilities.
Security experts bring their knowledge and experience to the table, interpreting the results from automated scans, conducting detailed manual tests, and providing insights that tools alone cannot offer. Their expertise helps in accurately assessing the risk and impact of identified vulnerabilities, ensuring you effectively address the most critical issues.
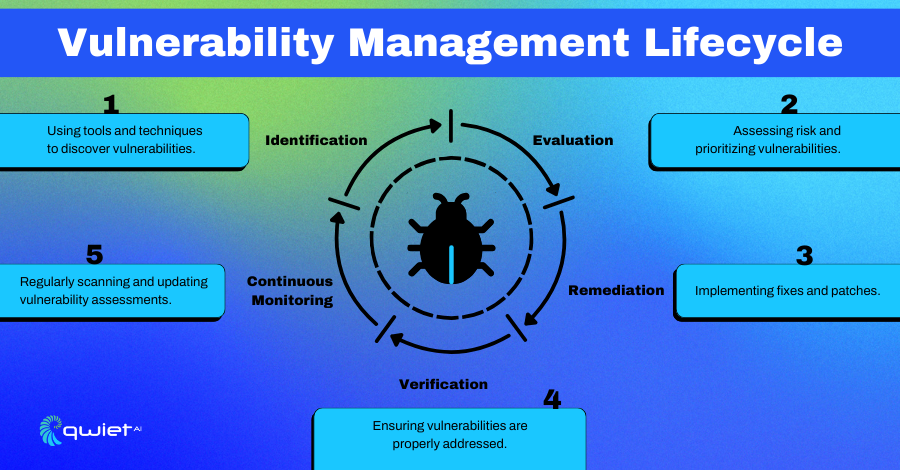
Conclusion
Regular vulnerability assessments are essential for identifying and fixing potential security weaknesses before they can be exploited. By combining automated scanners with manual testing, you can uncover and address vulnerabilities across your network, applications, and databases. Staying proactive with these assessments protects your sensitive data and ensures compliance with industry standards. Ready to strengthen your security posture? Book a demo with Qwiet today and see how it can safeguard your codebase.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com
