What is a Web Application Firewall (WAF)?

A Web Application Firewall (WAF) is a security tool designed to monitor, filter, and block HTTP and HTTPS traffic to and from web applications. It protects these applications by inspecting incoming requests for malicious patterns and blocking any suspicious or harmful traffic. This defense mechanism handles web-based threats, ensuring only legitimate traffic can interact with the web application.
WAFs operate at the application layer, offering protection against attacks that target vulnerabilities in web applications. These include threats like cross-site scripting (XSS), SQL injection, and many others that are part of the OWASP Top 10. By addressing application-layer vulnerabilities, WAFs provide a focused level of security to protect sensitive web services..
Why Web Application Firewalls Matter

Application Security
Sophisticated attacks often target Web applications to exploit vulnerabilities in the application layer. WAFs play a critical role in defending against these attacks by analyzing incoming traffic and preventing malicious requests from reaching the application. Whether the threat is an injection attack, a script-based exploit, or an application-layer threat, a WAF helps keep these attacks from compromising the system.
Regulatory Compliance
In many industries, protecting web applications isn’t just good practice—it’s a requirement. Regulations such as PCI-DSS, HIPAA, and GDPR mandate that organizations use protective measures like WAFs to secure sensitive data. A WAF can help organizations meet these compliance standards by providing a layer of defense against unauthorized access and data breaches, reducing the risk of legal penalties, and ensuring that data privacy standards are upheld.
Real-Time Protection
One of the key benefits of a WAF is its ability to provide real-time protection. By continuously monitoring traffic, WAFs can detect and block malicious requests as they happen. This immediate response helps to stop attacks before they can exploit vulnerabilities, keeping web applications secure without downtime or delays.
Zero-Day Attack Mitigation
WAFs are also highly effective in mitigating zero-day attacks. These attacks target previously unknown vulnerabilities, often before a patch or fix is available. With a WAF, flexible rule sets can be applied to detect and block suspicious behavior, providing protection even before a vulnerability is formally identified or patched. This proactive defense helps secure applications against emerging threats while waiting for official updates.
Components of Web Application Firewalls
Traffic Monitoring & Filtering
WAFs actively monitor and filter HTTP/S traffic, examining incoming and outgoing data for malicious patterns or behaviors. By analyzing each request, WAFs can identify potentially harmful traffic and block or flag suspicious requests before interacting with the application. This continuous monitoring helps detect and stop attacks like SQL injections or cross-site scripting, keeping the application safe from exploitation.
Rule Sets & Policies
WAFs use customizable rule sets that filter traffic based on specific application needs. These rules can be adapted to address the unique vulnerabilities of a particular web application or rely on pre-configured settings to block commonly known attack vectors. This flexibility allows WAFs to defend against generalized threats and more targeted attacks, providing a tailored layer of security for different environments.
Anomaly Detection & Signature Matching
WAFs enhance their security capabilities through anomaly detection and signature matching. By recognizing known attack signatures and identifying traffic that deviates from normal patterns, they can block or flag emerging threats before they become damaging. Detecting known threats and spotting unusual behavior protects established and new attack methods.
Modes of Deployment
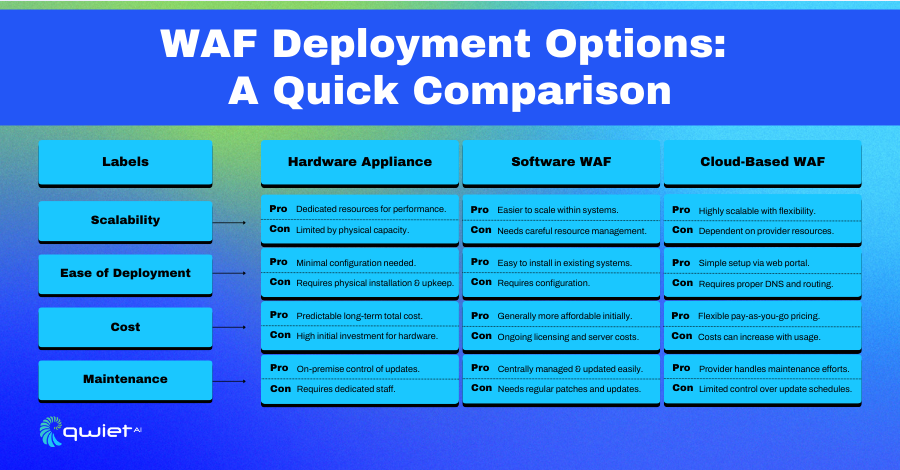
WAFs can be deployed in various ways to fit different infrastructure needs. They are available as hardware appliances, software installed on-premises or cloud-based solutions. This range of deployment options allows organizations to choose the approach that best suits their environment, whether a highly controlled on-premises setup or a scalable cloud-based architecture. Each deployment method offers the same level of security, but the choice depends on the organization’s specific infrastructure and security requirements.
Conclusion
Web Application Firewalls (WAFs) help protect web applications by monitoring and filtering traffic to block threats like XSS and SQL injection. They provide real-time protection with customizable rules and can detect unusual patterns, making them flexible for different environments. WAFs are important for security and compliance for businesses dealing with sensitive data. Qwiet can find vulnerabilities early to improve your security even more. Get in touch with the Qwiet team to learn more.
Read Next
Spring Boot Security Mechanisms
Introduction As businesses increasingly rely on web applications and microservices, securing them becomes important. Spring Boot is popular among developers for creating efficient microservices. This article will guide you through Spring Boot’s security options, from basic setups to advanced configurations. You’ll learn how to integrate these tools to enhance your application’s security.. Basics of Security […]
Microservices Security Overview
What is Microservices Security? Microservices security is the comprehensive approach to safeguarding each service within a microservices architecture. In this model, each service functions independently, which creates unique security requirements for each one. To secure these distributed services, microservices security involves methods to protect inter-service communications, secure APIs, and manage access and identity across multiple […]
The Top 10 AppSec Trends Shaping Cybersecurity in 2025
Key Takeaways Focus on API and Supply Chain Security: Strengthen API security with token-based authentication, API gateways, and AI-powered monitoring. Use AI-enhanced Software Bill of Materials (SBOMs) to identify and prioritize risks in third-party dependencies. Implement Zero-Trust at the Application Layer: Secure APIs, microservices, and data by enforcing strict access controls, continuous verification, and micro-segmentation […]