Introduction
SBOMs (Software Bills of Materials) are becoming a must-have in software development. They help teams understand their software’s dependencies, manage security risks, and meet growing compliance requirements. As regulations tighten and software systems get more complex, SBOMs provide much-needed visibility and control. Free and open-source SBOM tools have gained popularity for being cost-effective and easy to access. But are they enough to handle today’s demanding compliance and security needs? This article looks at what these tools can offer, where they fall short, and when it might make sense to look at enterprise solutions.
What Do Open-Source SBOM Tools Offer?
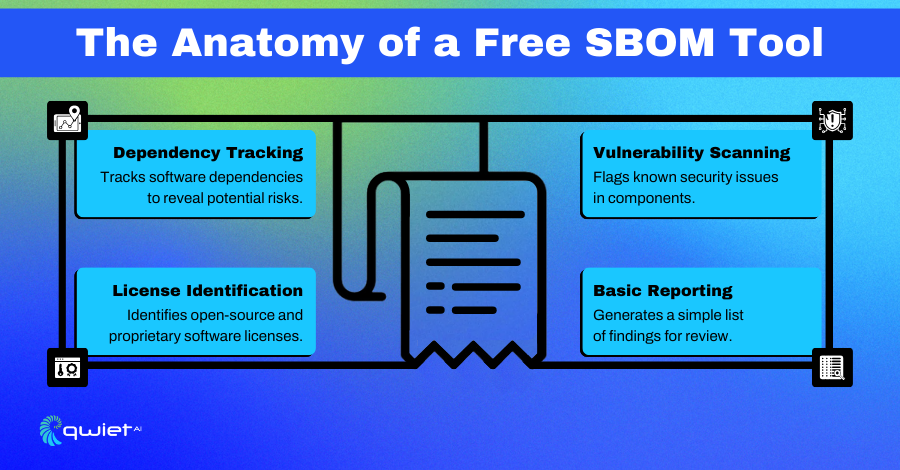
Open-source SBOM tools have gained significant traction for supporting software development teams in achieving transparency and managing dependencies effectively. Several popular frameworks and tools have emerged to help developers create and maintain software bills of materials, addressing the growing demand for clear visibility into software components.
- SPDX tools: SPDX (Software Package Data Exchange) is a widely used standard for representing SBOMs. Open-source tools based on SPDX provide formats and frameworks for generating, sharing, and validating software component data, fostering collaboration and transparency across projects.
- CycloneDX implementations: CycloneDX offers a lightweight standard for SBOM generation, optimized for security-focused use cases. Tools implementing CycloneDX provide flexible options for creating SBOMs, particularly in environments where security vulnerabilities are a primary concern.
- Dependency-checkers and scanners: These tools analyze dependencies within software projects to identify outdated, vulnerable, or unlicensed components. Open-source scanners integrate seamlessly into many development pipelines, helping developers detect risks and improve the integrity of their applications.
Beyond the technical capabilities, open-source SBOM tools bring several tangible benefits to software teams, especially those managing costs or working with limited resources.
- Cost savings: As free tools, open-source SBOM solutions eliminate the need for licensing fees, reducing overhead expenses while offering essential functionality for generating and maintaining SBOMs.
- Accessibility and ease of adoption: Open-source tools are readily available and often supported by clear documentation and active user communities. This makes them accessible to teams of all sizes, regardless of budget or technical expertise.
- Community-driven improvements and updates: Open-source projects thrive on active collaboration, with contributors regularly enhancing features, fixing bugs, and ensuring compatibility with new standards or frameworks. This dynamic development cycle allows users to benefit from shared innovation and collective expertise.
While open-source SBOM tools address many foundational needs, understanding their strengths and limitations is critical for organizations aiming to align their software practices with regulatory and security demands.
The Growing Need for SBOM Solutions
The demand for SBOM solutions has grown fast, especially as compliance requirements become stricter. Governments and industries are putting a spotlight on software transparency and security. For example, the U.S. Executive Order on Cybersecurity has made SBOMs a requirement for certain contracts to reduce supply chain risks. Different sectors, like healthcare, financial services, and government, are also introducing rules to ensure software meets their unique security standards.
On top of that, modern software ecosystems are becoming more complicated. Commercial and open-source components are deeply interconnected, creating layers of dependencies that can be tough to untangle. To keep up, teams need SBOMs that are reliable, detailed, and up-to-date in real time. These provide the necessary clarity to understand dependencies and address any risks they might bring.
Limitations of Open-Source SBOM Tools
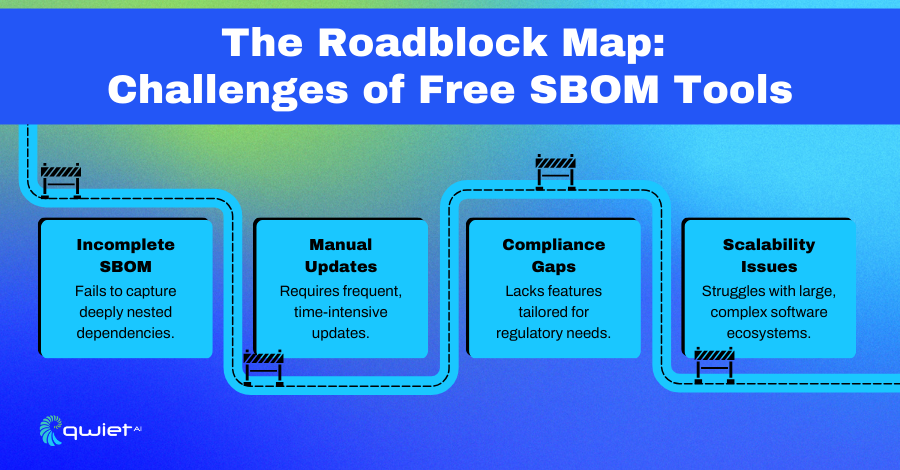
Accuracy and Completeness Issues
Open-source SBOM tools often struggle with identifying deeply nested dependencies, leaving significant gaps in understanding a software’s full composition. Mixed license environments add another layer of complexity, where these tools may fail to detect vulnerabilities accurately or provide comprehensive insights into licensing risks. These challenges can lead to incomplete SBOMs lacking the detail required for effective risk management.
Limited Compliance Readiness
Open-source tools frequently lack the specialized features needed to meet specific regulatory requirements, making them difficult to adapt for compliance in regulated industries. Generating SBOMs that align with multiple standards is another common limitation, as most free tools are not designed to handle the intricacies of cross-standard compatibility. This challenges organizations operating in sectors with diverse or evolving compliance needs.
Scalability and Maintenance
Handling large-scale or complex software environments is another area where open-source SBOM tools fall short. These tools often struggle to maintain performance and reliability as the project scale increases. Automating updates and integrating SBOM generation into CI/CD pipelines can also be challenging, leading to inefficiencies and gaps in the software development workflow.
Support and Reliability
With open-source SBOM tools, support often depends on community contributors rather than dedicated teams. While communities can be highly active, they may not provide the responsiveness required for critical updates or urgent security fixes. This reliance can result in delays when new features are needed or vulnerabilities are discovered, leaving organizations with unresolved issues for longer than is safe or practical.
Risks of Relying Solely on Open-Source SBOM Tools
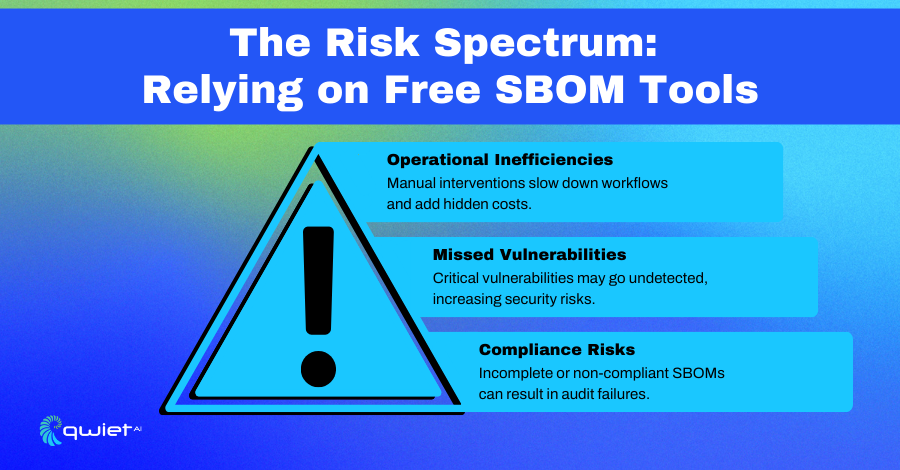
Compliance Risks
Open-source SBOM tools often need to address the nuanced requirements of regulatory frameworks, which can lead to significant compliance risks. For example, many of these tools need help to produce SBOMs that align with standards like ISO/IEC 19770-1, NIST 800-161, or industry-specific frameworks such as HIPAA or PCI DSS.
The inability to map software components accurately to these standards increases the likelihood of non-compliance during audits. This can result in financial penalties or legal actions, reputational damage, and loss of eligibility for government or enterprise contracts.
Security Vulnerabilities
One of the key limitations of open-source SBOM tools is their inability to detect deeply nested dependencies or track vulnerabilities in components with complex licensing. Vulnerabilities often reside in secondary or tertiary layers of a software supply chain, which these tools may need to pay more attention to due to insufficient depth in their analysis.
Furthermore, open-source tools typically lack integration with real-time vulnerability databases, which means outdated or insecure components may remain undetected for extended periods. These blind spots increase the overall attack surface and expose organizations to risks that could escalate into serious security incidents.
Operational Inefficiencies
In large or complex environments, open-source SBOM tools often require significant manual intervention to maintain accuracy and coverage. For instance, teams frequently need to address missing data fields, reformat reports, or reconcile mismatched dependency versions.
This labor-intensive process is compounded by the need for more automation capabilities in most tools, such as integration with CI/CD pipelines or support for real-time updates during build processes. As software environments scale, these inefficiencies become more pronounced, leading to delays in deployment cycles and increased workload for development, DevOps, and security teams. Over time, this fragmented approach to SBOM management can hinder the adoption of agile and secure development practices.
The Case for Paid or Enterprise SBOM Solutions
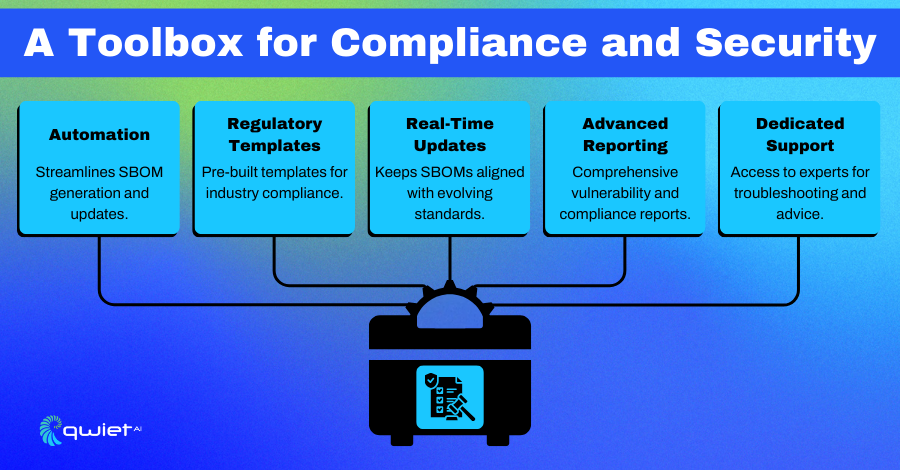
Enhanced Features and Capabilities
Enterprise SBOM tools offer advanced features that simplify managing complex software environments. They provide deep vulnerability scanning, detecting issues in even the most nested dependencies, and seamlessly integrate with DevSecOps pipelines to automate SBOM generation and updates. With detailed reports on vulnerabilities, licensing, and dependency health, these tools empower teams to stay ahead of potential risks while streamlining workflows.
Regulatory and Standards Support
Paid solutions make compliance much easier by offering pre-configured templates for frameworks like NIST, ISO, HIPAA, and PCI DSS. They also adapt to changing regulations with real-time updates, reducing the effort needed to stay compliant. This built-in compliance support helps organizations avoid audit headaches and maintain readiness for industry requirements.
Dedicated Support and Reliability
You can access dedicated support teams with enterprise solutions for quick help with technical issues or questions. Regular updates and security patches keep the tools reliable and aligned with the latest technologies and threats, giving you peace of mind when managing critical software dependencies.
Finding the Right Balance

When Free/Open-Source SBOM Tools Might Suffice
Free or open-source SBOM tools can fit smaller projects or organizations operating in non-regulated industries. These tools work well when compliance isn’t a significant concern and the scale of dependencies is manageable.
Teams with strong technical expertise in SBOM management can also effectively use open-source solutions, as they can address any gaps or limitations with custom scripting or manual adjustments. Open-source options meet the need for environments where flexibility and cost savings are more important than advanced features.
Indicators That It’s Time to Upgrade
As compliance demands increase, open-source tools often need help to keep up. When regulatory requirements become more complex or audits regularly occur, paid solutions offer the tailored support needed to stay aligned.
Similarly, enterprise solutions provide the scalability and automation required to handle the workload as the software ecosystem grows in complexity, whether through large-scale applications or heavily layered dependencies. For organizations where security risks or legal exposure carry significant consequences, the added reliability, compliance features, and support of paid SBOM tools make them a more effective choice.
Conclusion
Free and open-source SBOM tools are a great starting point, especially for smaller projects or teams in non-regulated industries. However, their limitations can challenge larger or more complex environments. Organizations facing strict compliance demands or high-security stakes often need tools that offer advanced features, scalability, and dedicated support. Choosing the right SBOM solution means balancing cost, capabilities, and compliance needs. Taking the time to assess your requirements can help you invest in the right tools for long-term success. Want to learn how Qwiet SBOM can help your team stay secure and compliant? Book a demo today to see it in action!
Read Next
Interactive Application Security Testing (IAST) Overview
What is Interactive Application Security Testing (IAST)? Interactive Application Security Testing (IAST) analyzes an application’s security while actively running. Unlike other approaches, it integrates directly with the app, allowing it to spot vulnerabilities as the code executes. This gives more accurate insights than methods that only look at static code or run tests outside the […]
Microservices Security Overview
What is Microservices Security? Microservices security is the comprehensive approach to safeguarding each service within a microservices architecture. In this model, each service functions independently, which creates unique security requirements for each one. To secure these distributed services, microservices security involves methods to protect inter-service communications, secure APIs, and manage access and identity across multiple […]
Vulnerability Assessment Overview
What is a Vulnerability Assessment? A vulnerability assessment is a thorough check-up of your information systems to find any security weaknesses. This involves identifying, classifying, and prioritizing potential vulnerabilities in your computer systems, networks, and communication channels. The goal is to uncover any weak spots that might be targeted by cyber threats so you can […]