What is Zero Trust Architecture?
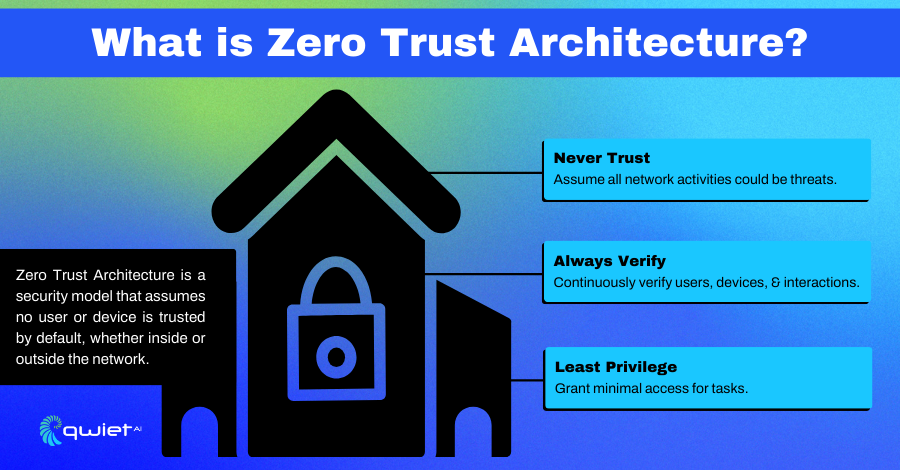
Zero Trust Architecture (ZTA) is a security framework that assumes no user or device is inherently trustworthy. It eliminates the concept of a secure perimeter by applying strict verification to every resource interaction, treating all access requests as potentially malicious.
ZTA continuously validates user and device identities, regardless of location, while enforcing least privilege to limit access to only what is necessary. This ongoing validation blocks unauthorized access and provides clear visibility into access patterns, simplifying threat detection and response.
The principle “Never trust, always verify” defines ZTA. Every access request is rigorously evaluated based on credentials, device compliance, and contextual risk, creating an environment where trust must always be earned.
Why Does Zero Trust Architecture Matter?
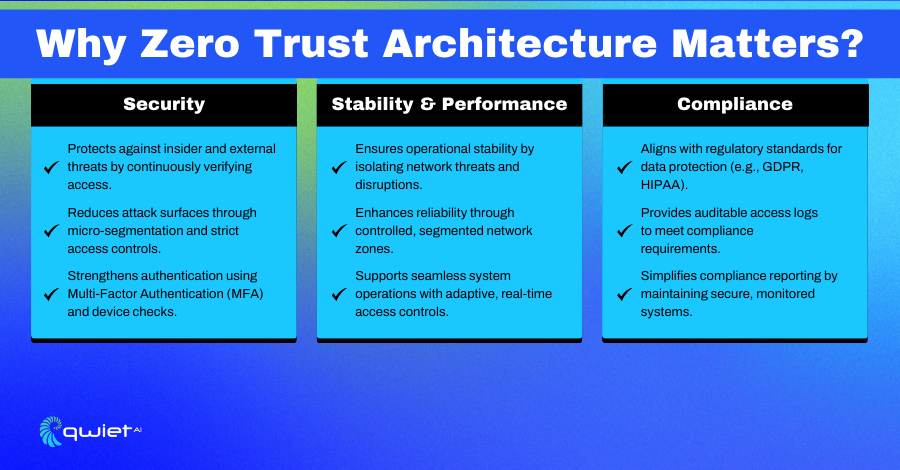
Security
Zero Trust strengthens security by treating every interaction as untrusted until thoroughly validated. Insider threats, accidental or deliberate, are just as dangerous as external attackers, and this model ensures that all access requests are rigorously authenticated and authorized. Zero Trust creates a protective layer against vulnerabilities like compromised accounts or exploited devices by reducing reliance on implicit trust.
It also limits exposure by restricting access based on specific parameters such as user roles, device compliance, and location. This containment approach significantly reduces the pathways attackers can exploit, even if they infiltrate a system. Continuous monitoring adds another layer of protection, analyzing each access attempt in real time to prevent unauthorized access to sensitive data and maintain its integrity and confidentiality.
Stability & Performance
Zero Trust enhances system stability by tightly controlling who and what can interact with resources. Unauthorized access, whether through malicious intent or human error, is a significant source of disruptions. Zero Trust minimizes the risk of unexpected downtime or operational interference by explicitly granting permissions and monitoring actions.
Micro-segmentation is another cornerstone of this model, dividing the network into smaller, isolated zones. This prevents attackers from moving freely within the network, effectively containing potential breaches to a single segment. Dynamic access controls improve performance by adapting to real-time changes, such as shifts in user behavior or risk levels. This means systems remain both secure and responsive, even as conditions evolve.
Compliance
Meeting regulatory requirements is a demanding but necessary aspect of modern operations, and Zero Trust simplifies this process. Its strict access controls, real-time monitoring, and detailed activity logs naturally align with the expectations of frameworks like GDPR, HIPAA, and PCI-DSS. Continuous verification of users, devices, and actions creates a clear audit trail, which not only aids in compliance reporting but also demonstrates a proactive commitment to protecting sensitive data.
Zero Trust also addresses compliance gaps by providing consistent, real-time visibility into access patterns, making identifying and correcting vulnerabilities easier. This model offers a structured, reliable approach to regulatory alignment for organizations under pressure to meet stringent standards.
Components of Zero Trust Architecture
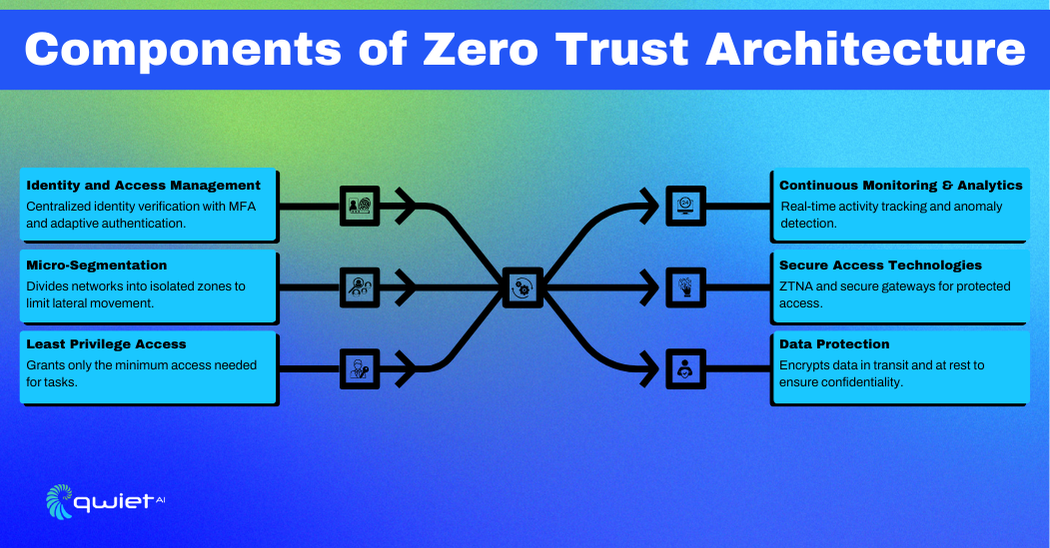
Identity and Access Management (IAM)
Identity and Access Management (IAM) ensures that only the right people can access your systems and data. It centralizes authentication, meaning there’s a single, streamlined way to verify users and devices.
But it doesn’t stop at just logging in once. IAM keeps checking to ensure the person or device interacting with resources is still authorized. Multi-factor authentication (MFA) adds an extra layer of security by requiring something beyond a password, like a code sent to your phone or a fingerprint scan. This extra step makes it much harder for someone to gain unauthorized access, even if they manage to steal one piece of information.
Micro-Segmentation
Think of micro-segmentation as breaking a big network into smaller, well-guarded zones. Each zone is tightly controlled and has rules about who or what can access it. This means that even if an attacker manages to breach one part of the system, they can’t roam freely to other areas.
Communication between these zones is also restricted to what’s necessary, so there’s less risk of a breach spreading. It’s a way to isolate and protect sensitive network parts, even when something goes wrong elsewhere.
Least Privilege Access
Least privilege access means giving users and devices only the permissions they need to do their jobs and nothing more. It’s like giving someone only the keys to their needed rooms, not the entire building. This limits the damage that could be done if an account or device is compromised.
But it’s not a one-and-done deal. Access levels are continuously reviewed and adjusted based on things like a user’s role, behavior, or system changes. This ensures that permissions stay relevant and secure as situations evolve.
Continuous Monitoring and Analytics
Continuous monitoring monitors everything happening in real-time, spotting potential threats as they emerge. It’s not just about watching; it’s about responding quickly.
Using tools like artificial intelligence and machine learning, Zero Trust can analyze behavior to flag unusual activities, like someone trying to access data they don’t normally use. This proactive approach makes catching and stopping threats easier before they cause significant damage.
Secure Access Technologies
Secure access technologies, like Zero Trust Network Access (ZTNA), provide secure and context-aware entry to applications and resources. ZTNA evaluates factors such as user location, device health, and the sensitivity of the accessed resource before granting permission.
Endpoint security tools and secure gateways also play a big role here. They check that devices are up-to-date and safe to connect to the network, helping maintain a strong overall security posture.
Data Protection
Data protection is all about keeping information safe, whether stored or shared. Encryption ensures that data remains private and intact, even if someone manages to intercept it. Policies are also put in place to control how data is shared, making sure it’s handled securely and doesn’t end up in the wrong hands. These measures protect the confidentiality, integrity, and availability of sensitive information, reducing risks and building trust in managing data.
Conclusion
Zero Trust Architecture is a smart way to tackle today’s security challenges. Continuously verifying users and devices protect against insider threats, limits lateral attacks, and helps meet compliance requirements. It’s a straightforward yet effective approach to keeping your organization safe and adaptable. Adopting Zero Trust principles lays the foundation for a secure and resilient infrastructure. Pairing these principles with tools like Qwiet ensures your code is free of vulnerabilities that could compromise your security. Book a demo with Qwiet today to see how it can secure your application.
Read Next
No related posts.
About Qwiet AI
Qwiet AI empowers developers and AppSec teams to dramatically reduce risk by quickly finding and fixing the vulnerabilities most likely to reach their applications and ignoring reported vulnerabilities that pose little risk. Industry-leading accuracy allows developers to focus on security fixes that matter and improve code velocity while enabling AppSec engineers to shift security left.
A unified code security platform, Qwiet AI scans for attack context across custom code, APIs, OSS, containers, internal microservices, and first-party business logic by combining results of the company’s and Intelligent Software Composition Analysis (SCA). Using its unique graph database that combines code attributes and analyzes actual attack paths based on real application architecture, Qwiet AI then provides detailed guidance on risk remediation within existing development workflows and tooling. Teams that use Qwiet AI ship more secure code, faster. Backed by SYN Ventures, Bain Capital Ventures, Blackstone, Mayfield, Thomvest Ventures, and SineWave Ventures, Qwiet AI is based in Santa Clara, California. For information, visit: https://qwietdev.wpengine.com
