Our journey in application security has always been about empowering developers, making them the key players in shipping secure code without drowning in noise. Back in 2021, at ShiftLeft, we introduced the concept of “Attacker Reachability,” a way to focus only on those open-source vulnerabilities that could be exploited in a given application. The results were stunning: filtering out issues that didn’t matter, we saw open-source vulnerability ticket volumes drop by over 90%. Fast forward to today, and ShiftLeft has evolved into Qwiet AI, a new name reflecting our mission to “quiet” the noise in AppSec.
In this post, I’ll reintroduce Attacker Reachability in the context of Qwiet AI’s modern platform, powered by Code Property Graph (CPG), enriched with Agentic AI assistants, and augmented by AutoFix remediation. The goal remains: deliver security and productivity by cutting out false positives and focusing developers on what truly matters.
What is “Attacker Reachability”?
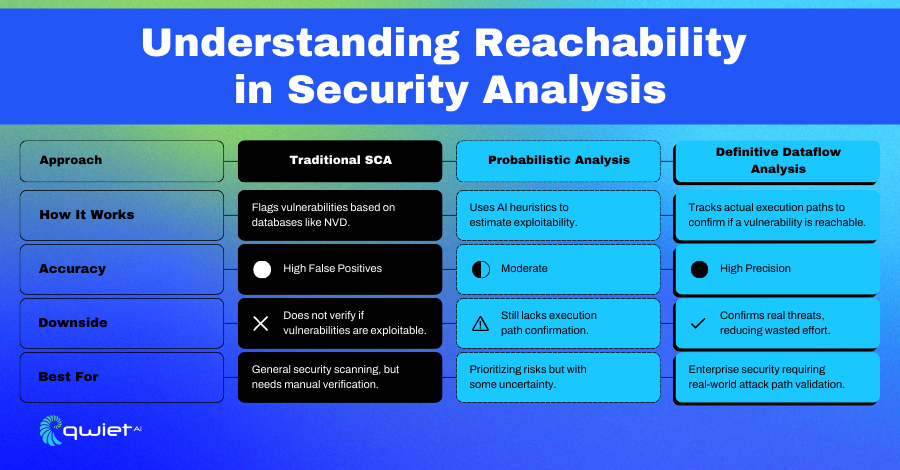
Attacker Reachability is all about determining whether a given vulnerability in an open-source dependency is reachable through a path that starts with an attacker’s input. In other words, if a sequence of calls from a public-facing entry point in your application (a source) to the vulnerable code (sink) in a third-party library, without any sanitization or validation, breaks the chain, that vulnerability is considered attacker-reachable. If no such path exists, the issue is largely theoretical for your app; it might be a critical CVE on paper, but it shouldn’t be a top priority if an attacker can’t get to it.
In practice, we define an attacker-controlled path by tracing an application’s public inputs to its sensitive sinks (database, log, HTTP response, etc.), checking that no adequate validation or sanitization occurs along the way. A CVE in a package is attacker-reachable if such an end-to-end path connects the app input to the vulnerable code in that package. Traditional Software Composition Analysis (SCA) tools often ignore this context, and they flag any known vulnerabilities in your dependencies. Qwiet AI takes a more innovative approach: if a vulnerability isn’t reachable in your app’s actual data flow, we can confidently deprioritize or even ignore it. This innovative approach sets us apart and ensures we’re not just another SCA tool.
Using Attacker Reachability as a filter, security teams can focus on the subset of open-source vulnerabilities that pose a real risk. This was the breakthrough insight at ShiftLeft, and it holds just as true now at Qwiet AI, except now we’ve supercharged it with our latest technology stack.
CPG-Powered Prioritization: How Code Property Graph Finds What Matters
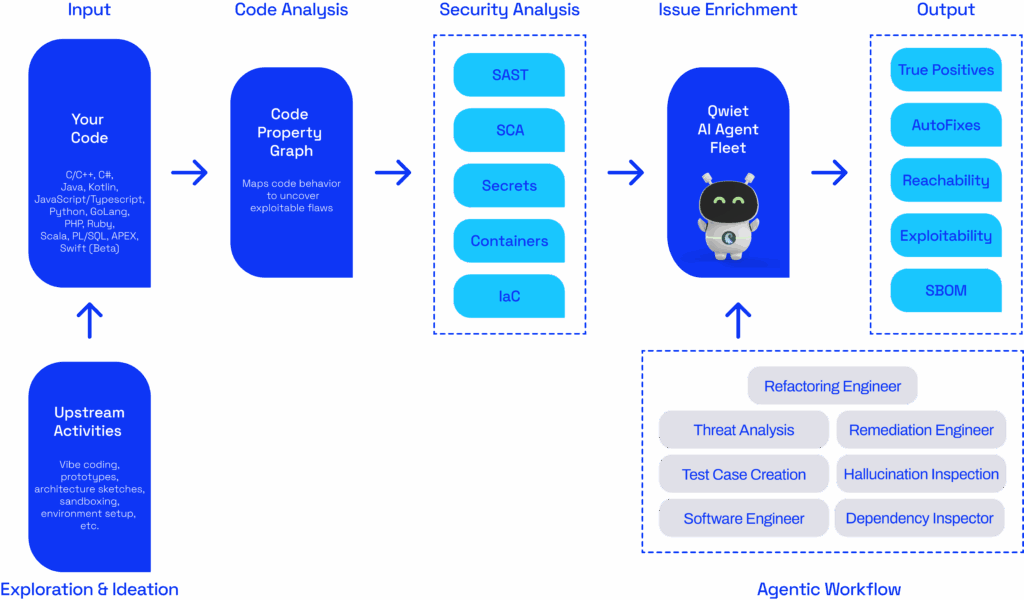
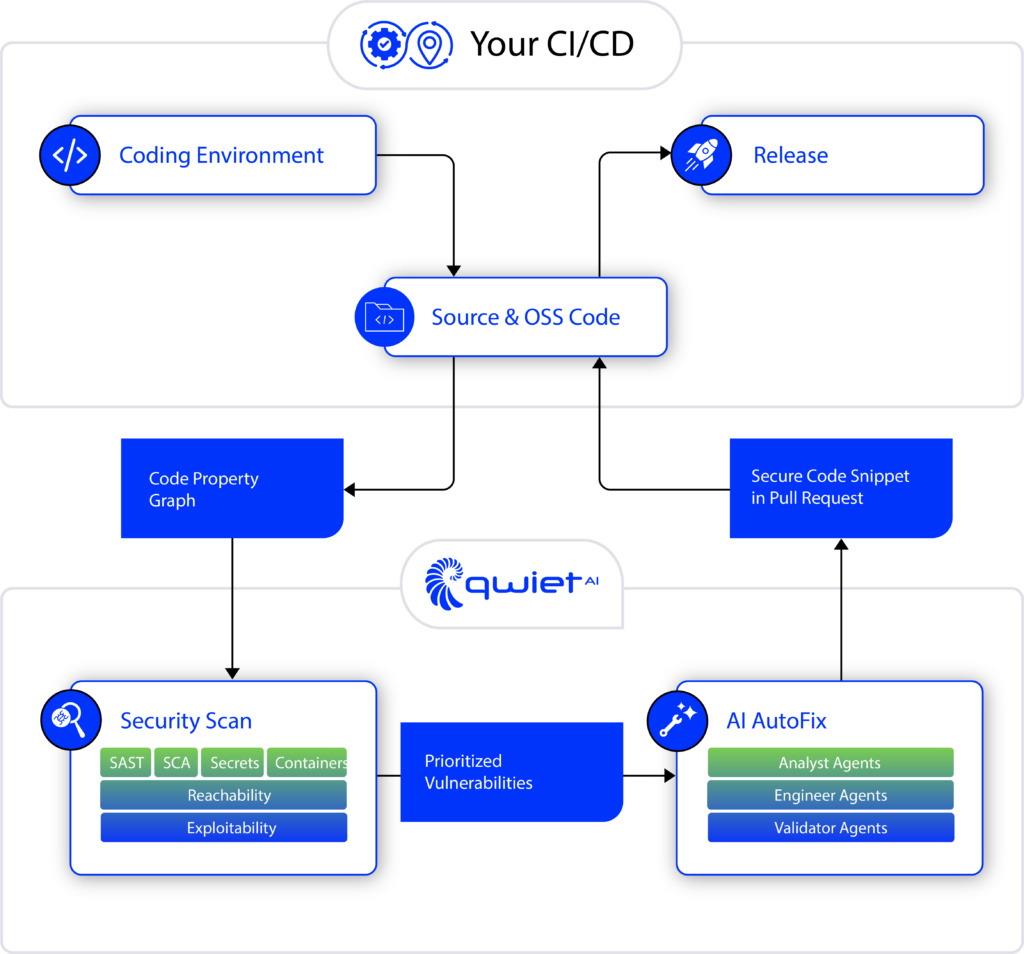
So, how does Qwiet AI figure out which vulnerabilities are attacker-reachable? The magic lies in our foundational technology: the Code Property Graph (CPG). The CPG is a comprehensive graph representation of your code. It combines abstract syntax trees, control-flow graphs, data-flow graphs, and more into one unified “graph of graphs”. This holistic view lets us understand how data moves through your application.
When Qwiet AI scans your code (including your custom code and all open-source libraries it uses), it first builds a Code Property Graph of the entire codebase. This graph knows all the call relationships that connect sources to sinks, and it also encodes how different components (including third-party packages) relate to each other within the app. Unlike a simplistic call graph, the CPG incorporates control flow and data flow analysis, so it won’t miss paths or falsely assume a path exists when it can’t happen. In short, it avoids the common blind spots that lead other tools to overestimate or underestimate reachability.
For example, a basic call graph might drop a path because it doesn’t realize data was transformed and passed along, or it might include a path that a real attacker couldn’t follow because it misses a condition that prevents exploitation. Qwiet’s CPG-powered analysis has no such problem. It can trace a path through a series of function calls, across module boundaries, following data transformations, while respecting conditional logic and sanitization checks. The result is a high-fidelity identification of which vulnerabilities are truly reachable by an attacker.
If the CPG shows a path from user-controlled input A to a vulnerable function in package E (with no safety net in between), we mark that CVE as reachable (and thus worthy of attention). Conversely, we can safely downgrade its priority if a vulnerability is never reached along any path from untrusted input (or only reached in scenarios where proper validation occurs).
This approach massively reduces false positives for open-source vulnerabilities. You’re no longer dealing with the entire list of CVEs in your software bill of materials; you’re dealing with the much smaller list of CVEs that impact your security. This noise reduction gives you the confidence that you’re focusing on the right issues. And we don’t stop there, we also factor in exploitability. Qwiet’s platform includes a feature called Blacklight, which checks each reachable vulnerability against real-world threat intelligence to see if there are known exploits in the wild. With a click of an “Exploitable” filter, you can narrow the list further to both reachable and exploitable vulnerabilities. Qwiet AI pinpoints the critical open-source issues that must be fixed before release by combining reachability and exploitability.
Agentic AI: Multiple AI Personas Supercharging AppSec
Identifying and prioritizing vulnerabilities is half the battle; the other half is doing something about them. This is where Qwiet AI’s Agentic AI comes into play. Agentic AI refers to our unique multi-AI approach. Instead of relying on a single monolithic AI to handle everything, Qwiet orchestrates a team of specialized AI agents collaborating throughout the security workflow. Think of it like an assembly line of intelligent assistants working together to secure your code, each with a specific role.
Why multiple agents? Because a lone AI model, no matter how advanced, can falter in complex tasks, it might hallucinate information or miss context. In contrast, a multi-agent system can have checks and balances. One agent’s output can be verified or refined by another, significantly reducing errors. In Qwiet’s case, we’ve designed a set of AI personas that mimic the workflow of a security and development team:
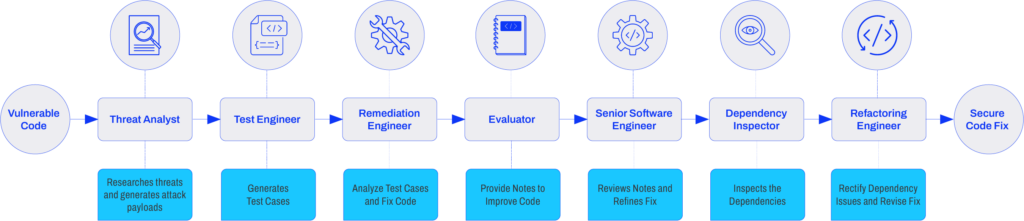
Qwiet AI’s guided Agentic AI workflow. Instead of a single AI, the platform employs a sequence of specialized “AI Security Code Assistants” (agents) that take on roles akin to human experts. For a given piece of vulnerable code, these agents perform tasks in succession a Threat Analyst agent researches the weakness and possible exploits, a Test Engineer agent generates test cases to confirm the vulnerability, a Remediation Engineer suggests code fixes, an Evaluator agent reviews and provides feedback on the fix, a Senior Engineer refines the solution, a Dependency Inspector checks for any library-level issues, and a Refactoring Engineer ensures the final patch integrates cleanly. This guided, collaborative process results in a Secure Code Fix with minimal human intervention. Such an Agentic AI approach means the AI isn’t just pointing out problems, it’s actively helping to solve them, step by step.
These AI personas operate within Qwiet AI’s platform seamlessly. The Agentic workflow kicks in when a security scan identifies prioritized vulnerabilities (thanks to reachability and exploitability analysis). One agent might start crafting a fix for a vulnerable code snippet, while another generates unit tests to validate the fix. Yet another agent cross-checks the fix against coding standards or known patterns to avoid regressions. Because they all share the context provided by the Code Property Graph, these agents deeply understand the application’s structure and data flows when proposing changes. The result is an AI-driven remediation process that is reliable and context-aware, much more than a naive “find-and-replace” or code suggestion.
Critically, the multi-agent system also helps eliminate AI hallucinations and mistakes. For example, if one agent proposes an incorrect code change, another agent (acting like a reviewer) can catch that by testing it or comparing it against the intended security requirements. This setup mirrors a human code review process, but everything happens autonomously at machine speed. It’s Agentic AI in action: a coordinated, autonomous workflow of AIs ensuring that the vulnerability is found and fixed correctly.
AutoFix: Automatic Remediation at Lightning Speed
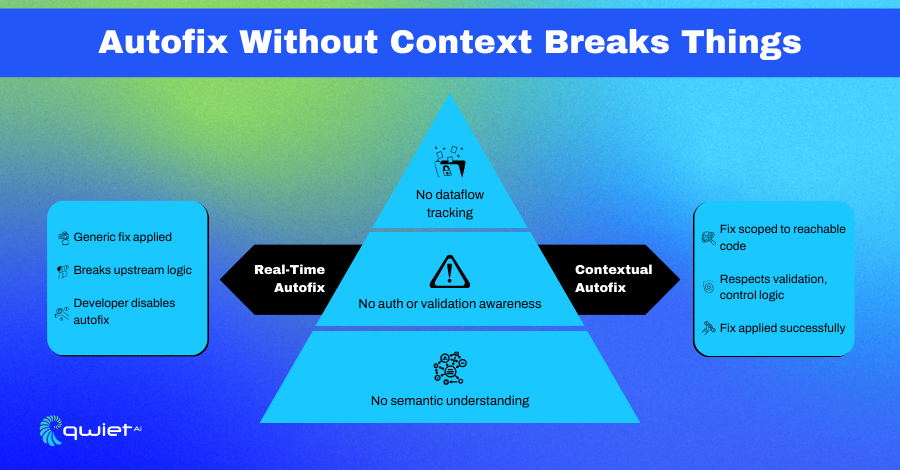
One of the most exciting outcomes of Qwiet’s Agentic AI system is AI AutoFix, which can automatically fix vulnerabilities in code. Instead of just throwing findings over the wall for developers, Qwiet AI can take the next step and provide a ready-to-apply fix (or even auto-apply it via pull request). Our AI agents essentially become an on-demand remediation team working alongside your developers.
The impact of AutoFix on development speed and security posture is tremendous. Imagine scanning your application and immediately getting a list of critical issues and code patches to resolve them. Qwiet’s AutoFix uses the collaborative intelligence of multiple agents plus the precision of CPG to generate contextual fixes that align with your code’s logic and style. It doesn’t just suggest a generic update; it looks at how similar issues were fixed in your code base or open source, understands the data flow, and produces a targeted code change that addresses the vulnerability while minimizing side effects.
This means developers save a vast amount of time. Instead of spending hours diagnosing a vulnerability and crafting a patch, they can review the AI-suggested fix (often produced in under 90 seconds by the platform) and then accept or tweak it. Early data shows that AI AutoFix can reduce remediation time by ~95% on average. In other words, what used to take days of back-and-forth can now be done in minutes. One tech journalist noted that with AutoFix, developers might only spend time on the truly challenging issues, letting the AI handle the routine fixes, potentially saving “an incredible 95% of time”.
AutoFix integrates into your existing development workflow. For example, it can automatically generate a secure code patch and open a pull request on your repository with the fix. A developer can then review the PR, run tests, and merge, significantly cutting down the mean-time-to-remediate (MTTR) for vulnerabilities. Because Qwiet AI also generates test cases as part of the Agentic workflow, you often get proof that the fix works (and doesn’t break anything) alongside it. This level of automation is unprecedented in AppSec: we’re not just finding issues faster, we’re also fixing them faster, all thanks to AI-driven automation.
Real-World Impact: Less Noise, Faster Remediation
The combination of Attacker Reachability, CPG-based analysis, and Agentic AI-powered AutoFix significantly boosts developers’ signal-to-noise ratio. We analyzed 49 applications using a traditional SCA tool in a recent proof-of-concept with a customer. We found 2,761 open-source vulnerabilities across 718 libraries, 2,761 potential “tickets” demanding developers’ attention. Then we ran the same apps through Qwiet AI’s platform. The list shrank dramatically by focusing only on reachable vulnerabilities; over 92% of those findings were eliminated as irrelevant. The development team could concentrate on roughly 200 significant issues instead of wading through thousands. This ~92% noise reduction isn’t a one-off; we consistently see that 90% or more of dependency CVEs can be safely deprioritized thanks to reachability analysis.
Now add exploitability filtering on top of that. Out of those ~200 reachable issues, a subset of known exploits in the wild becomes the highest priority. Everything else can be scheduled in a backlog or watched over time. The result is a laser focus on what will bite you if not fixed, instead of an endless list of theoretical “CVEs of the day.”
Crucially, Qwiet AI delivers this precision without sacrificing coverage. Our approach has been vetted against industry benchmarks. For instance, in tests against the OWASP Benchmark suite, Qwiet’s analysis achieved a 100% true-positive rate with only a 25% false-positive rate, making it one of the best-in-class static analysis solutions. High accuracy means you’re not trading one kind of noise for another; you truly get high recall and precision.
And when it comes to remediation, the story only gets better. AI AutoFix can often remediate those remaining priority issues in a fraction of the time it would take manually. By our estimates, teams using Qwiet AI have seen mean-time-to-remediate improve 10x or more on certain classes of vulnerabilities. Fixes that might have languished in the backlog for weeks are applied almost immediately. Developers can focus on feature work rather than churn through security debt, and AppSec teams can enforce policy (like “no critical reachable vulns before release”) without causing delays.
Let’s put it in perspective with a few key takeaways:
- 90% + Noise Reduction: By leveraging Attacker Reachability, Qwiet AI customers routinely eliminate most open-source vulnerability alerts as non-issues. Developers only get actionable, relevant findings instead of hundreds or thousands of false alarms.
- Prioritize Exploitable Risks: Integrating reachability with live threat intelligence means the issues you see have both a path and a known exploit vector. Essentially, your actual top risks.
- 95% Faster Remediation: The Agentic AI and AutoFix capabilities rapidly generate and apply fixes. Internal data and external reviews report up to a 95% reduction in remediation time for typical vulnerabilities. Faster fixes = significantly lower MTTR and reduced window of exposure.
- Improved Dev Productivity: Shorter vulnerability lists and automated fixes reduce developers’ distractions. Teams can focus on building product features, with security handled in the background. One Qwiet AI user noted that their developers “only have to spend time on real challenges” instead of wrestling with endless security tickets.
- Unified Platform: Qwiet AI brings SAST, SCA, SBOM, secret scanning, and more into one scan, powered by the Code Property Graph. No more jumping between separate tools and reconciling results, it’s one integrated view of your code security posture. This unified approach and our AI engine ensure nothing slips through the cracks, even as it reduces noise.
Now what?
Attacker Reachability was a game-changer when we first rolled it out, and in the era of Qwiet AI, it’s more potent than ever. By intelligently separating the signal from the noise and then using automation to act on that signal rapidly, we enable development teams to achieve what once seemed impossible: significantly better security with substantially less effort. As someone on this journey from the ShiftLeft days to now, I’m proud (and frankly excited) to see how far the platform has come. We’ve gone from simply identifying critical vulnerabilities to fixing them on the fly, all while preserving developer velocity.
In a world where new vulnerabilities and zero-days make headlines every week, Qwiet AI’s approach ensures that you can focus on the vulnerabilities that truly matter and trust the platform to handle much of the remediation work. Our customers have found that this leads to more secure code in production, less firefighting, and happier developers. After all, delivering secure software on time is the ultimate win-win for security and engineering.
Don’t just take our word for it, you can try out Qwiet AI’s platform for free using your code. See how it identifies reachable, exploitable vulnerabilities and watch AutoFix generate a patch before you’ve even had a chance to create a JIRA ticket. We’re confident you’ll be amazed by the noise reduction and productivity gains. If you’d like a deeper dive or a tailored walk-through of how this could work in your organization, reach out to us to schedule a demo, and our team will be happy to show you Qwiet AI in action.
Security may never be “easy,” but it can be quieter with smart prioritization and intelligent automation. Qwiet AI is here to make that a reality. Here’s to reducing the noise and letting you code in peace, knowing the critical vulnerabilities are under control!
