Introduction
OAuth 2.0, the authorization framework, is as ubiquitous as cat videos on the internet. But just like those seemingly innocent videos, OAuth 2.0 can hide some nasty surprises if not implemented correctly. As the digital landscape evolves, so do the challenges and threats developers face. Ensuring that our web applications are secure is not just a matter of best practice but a necessity. So, let’s roll up our sleeves, delve deeper into the intricacies of OAuth 2.0, and fortify our web apps to be as secure as Fort Knox.
The Basics: Understanding OAuth 2.0
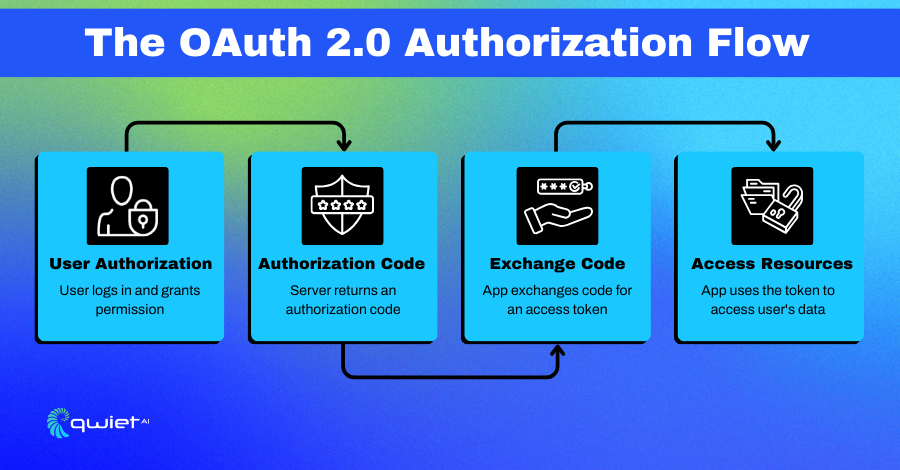
OAuth 2.0 is the go-to framework for allowing third-party applications to access web resources without sharing passwords. Imagine a world where you had to give your house key to a friend every time they wanted to borrow something. Risky, right? OAuth 2.0 offers a solution akin to giving them a special key that only works for specific rooms and for a limited time.
It’s like a digital handshake that says, “Hey, this user trusts me. Can I access their data?” By facilitating this trust, OAuth 2.0 ensures that users don’t have to compromise their security while enjoying the convenience of interconnected applications.
Code Snippet: Basic OAuth 2.0 Authorization Flow in JavaScript
| const express = require(‘express’); const axios = require(‘axios’); const app = express(); app.get(‘/auth/redirect’, async (req, res) => { const authCode = req.query.code; const tokenResponse = await axios.post(‘<https://oauth2.example.com/token>’, { code: authCode, client_id: ‘YOUR_CLIENT_ID’, client_secret: ‘YOUR_CLIENT_SECRET’, redirect_uri: ‘<http://localhost:3000/auth/redirect>’, grant_type: ‘authorization_code’ }); const accessToken = tokenResponse.data.access_token; // Use the access token to access protected resources }); |
In this JavaScript example, we use the Express.js framework to handle the OAuth 2.0 authorization code flow. When the user authorizes your application on the OAuth provider’s site, they are redirected back to your application with an authorization code.
This code is then exchanged for an access token by making a POST request to the OAuth provider’s token endpoint. The access token can then be used to make authorized API requests on behalf of the user.
Common Pitfalls and How to Avoid Them
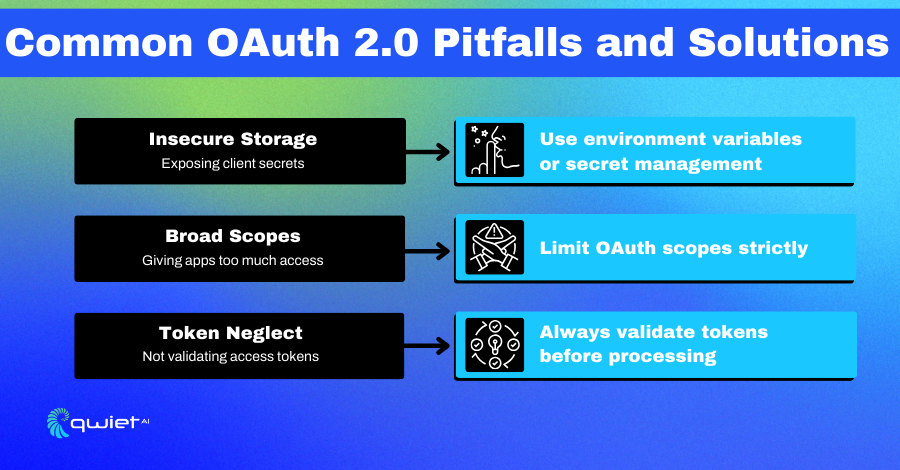
Insecure Storage of Client Secrets
The client secret is a critical component in the OAuth 2.0 dance. It’s shared between your application and the OAuth 2.0 provider, acting as a credential proving your identity. If mishandled or exposed, malicious actors can impersonate your application, leading to unauthorized access to user data.
Storing this secret directly in source code or unprotected databases is a glaring vulnerability. Properly securing the client’s secret is paramount to ensuring the integrity of the authorization process.
Countermeasures:
- Use specialized, secret management services.
- Encrypt client secrets before storing them.
- Regularly rotate and update client secrets.
- Limit access to client secrets only to necessary personnel.
Code Snippet: Securely Storing Client Secrets
| require(‘dotenv’).config(); const clientSecret = process.env.OAUTH_CLIENT_SECRET; |
We’re using the dotenv package to load the client secret from an environment variable. This ensures that the secret is not hard-coded into the application, reducing the risk of accidental exposure.
Inadequate Scope Limitation
Scopes in OAuth 2.0 define the boundaries of what a third-party application can and cannot do. Think of them as permissions. Granting excessive scopes is risky.
If a third-party application is ever compromised or has hidden malicious intentions, it could misuse those broad permissions, leading to data breaches or unwanted data manipulation.
It’s essential to be judicious and precise when defining and granting scopes, ensuring applications only get the necessary access.
Countermeasures:
- Limit scopes to only what the third-party app needs.
- Regularly review and update scope permissions.
- Educate users on the implications of granting scopes.
- Implement a scope approval process for third-party apps.
Code Snippet: Limiting OAuth Scopes
| const tokenResponse = await axios.post(‘<https://oauth2.example.com/token>’, { // …other parameters scope: ‘read_profile’ }); |
In this code snippet, we’re specifying the scope as read_profile, which means the third-party app can only read the user’s profile information and nothing more. This is crucial in limiting what the third-party app can do with the access token.
Lack of Token Validation
Access tokens are the golden tickets in the OAuth 2.0 world. They prove that a user has granted specific permissions to an application. However, applications might act on invalid, expired, or tampered tokens without proper validation.
This oversight can lead to unauthorized actions or data exposures. Ensuring rigorous token validation is a fundamental step in maintaining the security and integrity of the authorization process.
Countermeasures:
- Validate tokens before processing requests.
- Implement token blacklisting mechanisms.
- Set short expiration times for tokens.
- Use token revocation endpoints.
Code Snippet: Validating Access Tokens
| const jwt = require(‘jsonwebtoken’); function validateToken(accessToken) { try { const decoded = jwt.verify(accessToken, ‘YOUR_PUBLIC_KEY’); return true; } catch (error) { return false; } } |
In this code snippet, we use the jsonwebtoken library to validate the access token. The jwt.verify() method checks and decodes the token’s signature. If the token is invalid or tampered with, an exception is thrown, and the function returns false.
Advanced Techniques
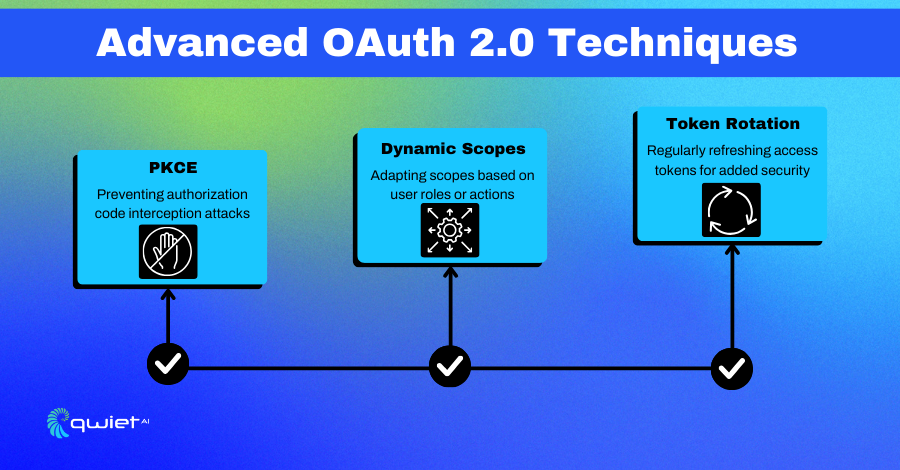
Implementing PKCE for Public Clients
PKCE, or Proof Key for Code Exchange, is a vital enhancement for OAuth 2.0, especially for public clients like mobile apps where storing a client secret securely is challenging. PKCE introduces an additional layer of security, ensuring that even if an authorization code is intercepted, it can’t be misused.
By generating a unique code verifier for each authorization request and its derived code challenge, PKCE ensures that only the genuine client can exchange the authorization code for an access token, adding an extra layer of protection against potential attacks.
Code Snippet: Implementing PKCE
| const crypto = require(‘crypto’); const codeVerifier = crypto.randomBytes(64).toString(‘hex’); const codeChallenge = crypto .createHash(‘sha256’) .update(codeVerifier) .digest(‘base64’); |
In this code snippet, we generate a code verifier and a code challenge using Node.js’s built-in crypto module. The code verifier is a cryptographically random string. The code challenge is the SHA256 hash of the verifier, encoded in base64. These values are used to secure the OAuth 2.0 authorization code flow.
Conclusion
OAuth 2.0 is a robust and flexible framework that can provide strong security for your applications. However, like any powerful tool, it must be handled carefully. A small misstep can lead to significant security vulnerabilities. With the right knowledge and practices, you can make your OAuth 2.0 implementation as secure as a Swiss vault. So implement these best practices, and sleep easy knowing that your application’s authorization is in good hands! To further bolster your application’s security, consider Qwie.ai, book a demo now, and discover how Qwiet.ai can elevate your security posture.