Key Takeaways
- Static tools miss logic-driven vulnerabilities. Traditional SAST tools flag obvious syntax-level risks but fail to understand business rules, multi-tenant boundaries, or the actual intent behind code behavior.
- Qwiet’s comprehensive analysis traces full execution paths across helpers, middleware, and services. Modeling code as a connected graph uncovers hidden risks buried in trusted-looking utilities, such as unvalidated shell calls, authorization gaps, and insecure file operations.
- Remediation is only valuable if it respects context. Qwiet’s auto-fix suggestions are designed to preserve business logic while resolving vulnerabilities. This approach contrasts with shallow, rule-based fixes that can break functionality or miss deeper patterns.
Introduction
Most SAST tools accurately catch obvious issues like hardcoded secrets, dangerous functions, and untrusted input in the same file. But they fall short when vulnerabilities depend on how your app works, how data flows across helpers, which services enforce access, or whether business rules are being followed. They don’t see the whole picture and miss the real risks. Qwiet is built to close that gap. It analyzes your entire codebase as a connected graph, following execution across files, layers, and services. It doesn’t just look at what the code says; it understands what it is doing. This article breaks down where traditional scanners stop and how Qwiet goes further to catch what others miss.
SAST Pattern Matching vs. Real Application Logic

Traditional SAST tools are built to detect known patterns, such as dangerous function calls combined with untrusted input. That works well for catching obvious issues, but they don’t evaluate what the code tries to do. They don’t model business semantics or reason about the intent behind access rules. For example, they can’t tell whether a route is supposed to be tenant-scoped or publicly accessible.
That distinction matters in multi-tenant apps. Without validating ownership or access context, a request might return data that belongs to a different user or organization. SAST tools miss that because the vulnerability isn’t in the syntax; it’s in the missing logic. That gap creates risk, and it’s one of the reasons these tools often miss issues that show up in production but not during static analysis.
Multi-Tenant Access Control Missing
This is a good example of a security issue that’s easy to miss during static analysis because nothing looks wrong. The code works, tests pass, and traditional SAST tools trigger no warnings.
But in a multi-tenant system, missing a tenant ownership check can lead to data leakage across accounts or organizations, something that’s not visible from syntax alone.
// routes/projects.js
app.get(‘/projects/:id’, authenticate, async (req, res) => {
const project = await Project.findById(req.params.id);
if (!project) return res.status(404).json({ error: ‘Not found’ });
// No tenant ownership check
res.json(project);
});
This route appears fine on the surface. Authentication is enforced, the project is queried, and a response is returned. But it’s missing a critical validation step: confirming that the fetched project belongs to the requesting user’s tenant. Users can access records outside their scope without that check simply by guessing or iterating through project IDs.
SAST won’t flag this because there’s no dangerous function, tainted input, or insecure API call. The issue lives entirely in the missing business rule, which requires understanding how tenants are structured and how ownership should be enforced. Quiet catches this by analyzing the full behavior path and identifying when expected guardrails, like tenant filtering, are missing.
Graph-Based Analysis of Internal Helper Behavior
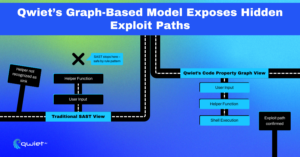
Unsafe Internal Shell Execution
It’s common for engineering teams to use internal helpers or utilities to abstract repetitive logic, such as restarting services, managing files, or wrapping database access.
These functions often feel safe because they’re internal and used consistently, but they can still contain unsafe behavior. Traditional SAST tools often miss issues because the risk is hidden a few layers behind trusted wrappers. If the tool doesn’t treat the helper as a sink, it doesn’t get flagged, even if user input ends up in a shell command.
# utils/deployment.py
def restart_service(name):
import os
os.system(f”systemctl restart {name}”) # Unsafe command usage
# routes/admin.py
@app.route(‘/admin/restart’)
@require_admin
def restart():
service = request.args.get(‘service’)
restart_service(service) # No validation of input
, return ‘Restarted’
Here, the /admin/restart route accepts a query parameter and passes it straight into a utility function that runs a shell command. The restart_service helper wraps the dangerous behavior behind a familiar interface, but the risk remains that user input is being executed without validation or sanitization.
This kind of pattern is common in internal tooling, where trusted-looking wrappers abstract away complexity. However, shell execution remains vulnerable if untrusted input is reached.
Traditional SAST tools often miss cases like this because they don’t treat the helper as a sink and can’t follow the data path across files or layers. Qwiet traces input flow across function calls, sees where it lands, and flags the behavior even when it’s several levels deep in internal code.
Auto-Fix with Context-Aware Repair Suggestions

Security tools can suggest fixes, but if those fixes don’t respect how the code is being used, they create more problems than they solve. A good remediation path needs to reflect the intent of the code, not just what pattern it matches. That’s especially true when user input influences sensitive operations, like writing to the filesystem.
Take this example from a file upload route:
const fs = require(‘fs’);
app.post(‘/upload’, authenticate, (req, res) => {
const filePath = `/uploads/${req.body.filename}`;
fs.writeFileSync(filePath, req.body.content); // Path traversal risk
res.json({ message: ‘File saved’ });
});
The writeFileSync() call means the filename comes directly from the request body. An attacker could craft a payload that writes files outside the intended directory without sanitization. Most static tools either miss this or surface it without a meaningful fix.
Qwiet looks at the full data path and understands how user input flows into the file system operation. It knows this is a path traversal issue, and it can generate a fix that neutralizes the risk without altering the app’s behavior. Here’s what that looks like:
const path = require(‘path’);
const safePath = path.join(‘/uploads’, path.basename(req.body.filename));
fs.writeFileSync(safePath, req.body.content); // Sanitized path
This fix uses path.basename() to neutralize directory traversal attempts by stripping any parent path references from the filename. It ensures the file is written inside the intended directory, regardless of user input. The rest of the logic remains untouched, preserving the route’s behavior.
This kind of targeted patch only works if the tool generating it understands where the input comes from, how it’s used, and what the code is trying to do. Qwiet’s context-aware analysis provides visibility, unlike rule-based scanners that either miss the issue entirely or suggest a generic fix that breaks functionality.
Enforcement of Business Logic Through Policy-Aware Scanning
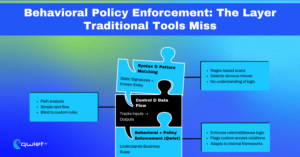
Many high-impact security issues result from missing business logic, not from obviously dangerous code. Teams often have internal expectations, like “only finance managers can approve invoices” or “admin routes must include role checks,” but those expectations don’t always appear in the code.
Most static analysis tools won’t detect when those patterns are missing because there’s no known sink or tainted input. The code runs fine, but the access control logic isn’t enforced.
Take this route for invoice approval:
app.post(‘/invoices/:id/approve’, async (req, res) => {
await approveInvoice(req.params.id); // Missing role check
res.json({ status: ‘approved’ });
});
The issue here isn’t in what the code does; it’s in what it doesn’t do. There’s no middleware confirming that the user has the proper role. Anyone who can hit this route can approve an invoice. It’s a business policy violation, but static tools won’t catch it because there’s no unmistakable security signature against which to match.
Qwiet scans with context and policy awareness. If a route like this is expected to be protected by requireRole(‘finance_manager’), Qwiet flags the gap and offers a fix that fits how the rest of the application handles access control:
app.post(‘/invoices/:id/approve’, requireRole(‘finance_manager’), async (req, res) => {
await approveInvoice(req.params.id);
res.json({ status: ‘approved’ });
});
This issue doesn’t appear in security dashboards unless the tool knows what rules matter to your environment. Qwiet connects expected behavior with actual implementation and highlights when they don’t match. That’s the level of control you need if you’re trying to catch business logic gaps before they turn into incidents.
Conclusion
Qwiet isn’t just scanning for patterns, and it’s analyzing behavior. It detects business logic flaws, missing authorization checks, dangerous helper usage, and data exposure risks that static tools often overlook. With full-code graph modeling, it understands what the code is doing and what it’s meant to do.
That insight powers targeted auto-fix suggestions and policy-aware enforcement that reflect how the application works. It reduces manual triage and supports dev teams without slowing them down. The result is accurate coverage where it matters and a faster, cleaner path to secure code. Want to see how Qwiet fits into your environment? Book a demo to see how it detects what legacy scanners miss and accelerates remediation with context-aware insight.
FAQs
Why do traditional SAST tools miss business logic vulnerabilities?
Most SAST tools scan code by matching known patterns. They don’t evaluate execution paths, cross-file dependencies, or how data interacts with business rules. That closes their eyes to logic flaws, missing authorization checks, and multi-tenant access issues.
What makes Qwiet AI different from other static analysis tools?
Qwiet uses graph-based code analysis to trace how data flows across files, services, and helper functions. It models behavior instead of relying on pattern matching, allowing it to detect vulnerabilities tied to logic, authorization, and app-specific rules.
Can Qwiet AI provide secure auto-fix suggestions?
Yes. Qwiet offers context-aware repair suggestions considering data flow, business logic, and application structure. This reduces the risk of regressions and avoids breaking functionality, unlike basic tools that suggest shallow, one-size-fits-all fixes.
How does Qwiet detect hidden risks in helper functions or internal tools?
Qwiet builds a code property graph that maps function calls, data movement, and execution paths. It can trace unvalidated input into internal utilities, even when the risk is buried in functions that static tools usually skip.
