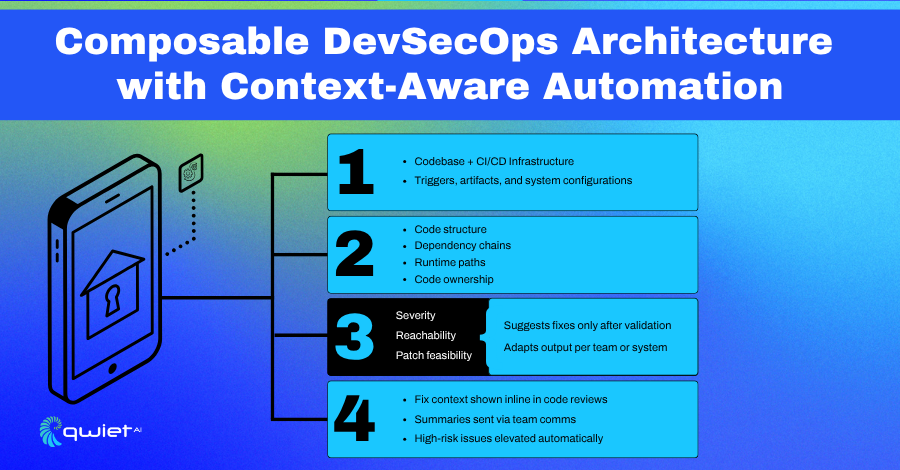
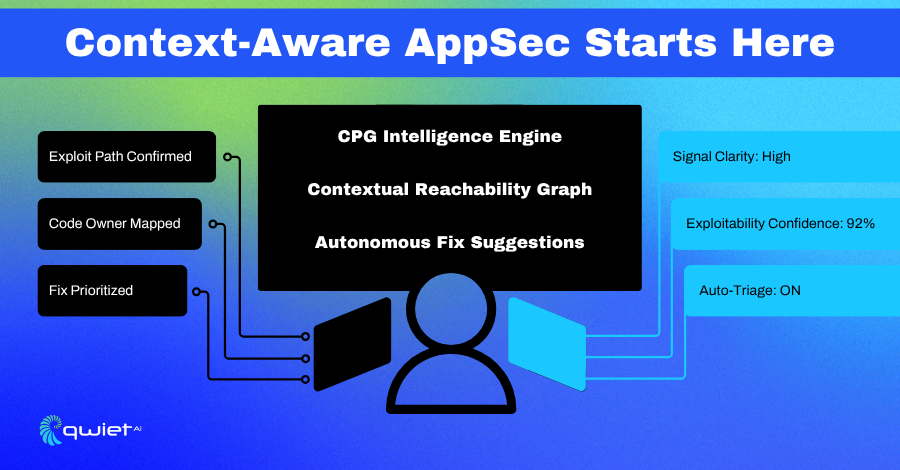
Scaling DevSecOps in the AI Era: What...
Introduction DevSecOps isn’t broken, but under stress as AI-generated code accelerates delivery. It’s also injecting complexity and risk into development pipelines, often without clear visibility. Developers are now expected to integrate security scanning into CI/CD, interpret ambiguous findings, and deliver clean code at machine speed. In this article, you will learn where traditional DevSecOps workflows […]