Key Takeaways
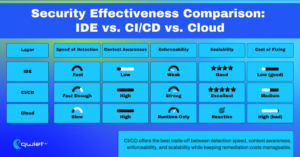
- While IDE tools are beneficial for providing immediate feedback, their scope is limited. They excel at catching fundamental issues early in development, such as missing input validation, insecure function usage, or weak defaults. However, they cannot see system-wide interactions, merged branches, or production configurations. This limitation underscores the need for a more comprehensive security solution.
- Cloud-based security tools, while offering runtime visibility, are inherently reactive. They detect threats in production, by which time vulnerabilities have already been exposed and are more complex and costly to fix. This reactive nature underscores the need for a more proactive security solution.
- CI/CD pipelines offer a proactive approach to security, striking a balance between visibility, enforcement, and scale. Positioned at the heart of the workflow, they analyze the entire application state, enforce policy automatically, and enable teams to identify and address issues before deployment, all without impeding the development process. This proactive stance should reassure software teams about the security of their code.
Introduction
Software teams are shipping faster than ever, pushing features, merging pull requests, and deploying updates daily. That speed helps delivery, but increases the risk of missed security issues. So, where should security fit in? Should it start in the IDE, kick in after deployment, or happen somewhere between? Each layer plays a role. IDEs offer quick feedback, and cloud tools catch runtime issues, but neither provides the context, control, or scale needed to secure fast-moving code. CI/CD pipelines close that gap. Sitting in the middle of the workflow, they see the whole application state and catch issues before release. This article looks at each stage and shows why CI/CD is the most effective place to apply security.
The IDE: A Developer’s First Line, But Not Enough

Security checks in the IDE offer developers instant feedback as they write code. These tools can help flag mistakes early, like missing input validation, insecure function usage, or weak defaults. Getting that real-time feedback can help teams maintain coding standards and avoid simple issues before they get pushed upstream.
That said, IDE-based tools operate with a narrow view. They typically scan one file or a developer’s local project at a time. They don’t see merged branches, complete dependency graphs, or how different services interact across environments. And they’re not looking at the actual configurations that go live in production. So while they help point out localized issues, they miss anything that depends on full-system context.
Another limitation is that they’re developer-controlled. If a tool starts slowing things down or throws too many low-value warnings, it’s easy to silence or deactivate. That makes it hard to rely on for consistent security enforcement across a team or codebase.
IDE scanning has value for early-stage feedback. But it’s isolated. It doesn’t connect to the rest of the security pipeline or scale across environments or teams. If the goal is to prevent real-world vulnerabilities from reaching production, you will need more than what these tools can see.
The CI/CD Pipeline: Where Context Meets Automation
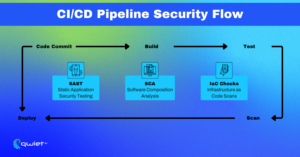
CI/CD pipeline security checks happen automatically as part of code commits, pull requests, and builds. They run on the whole application state, scanning for code-level issues, configuration flaws, dependency risks, and even infrastructure drift. These scans are usually more thorough than possible inside a local development environment and are tightly integrated into how teams ship code.
One of the strengths is visibility; the pipeline can access merged code, environment variables, dependency manifests, container specifications, and deployment scripts. That broader view allows it to catch vulnerabilities that only emerge when code is integrated or configured for production. It also helps detect issues in third-party libraries, secrets in version control, or misconfigurations in infrastructure-as-code templates.
Security in the pipeline can be enforced as policy. That means high-severity vulnerabilities, failed checks, or misaligned permissions can block a build from continuing. Instead of relying on manual review or hoping developers catch everything, the pipeline creates automatic gates that apply across projects. Those controls can be standardized so teams aren’t left guessing what’s safe to deploy.
Another advantage is the ability to scale; once scanners are in place, they can evaluate hundreds of pull requests daily without adding friction. Because the scans don’t run on a developer’s machine, they can process larger workloads and use more advanced rulesets. This allows for behavioral detection, API misuse analysis, and custom organizational policies without impacting developer speed.
Consistent outputs also benefit security teams. Pipeline scan results can be logged, reported on, and used to track progress over time. Telemetry helps with auditing, compliance, and identifying where teams might need more training or tighter review. Compared to early or late-stage scanning, CI/CD offers a high-leverage spot to catch issues with the right balance of context, automation, and repeatability.
The Cloud: Watching Too Late, Fixing Too Expensively
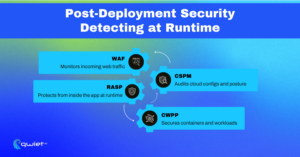
Cloud-based security tools operate post-deployment, monitoring running systems for threats and misconfigurations. These tools, like WAFs, RASP, CSPM, and CWPP, are designed to observe real-time traffic, detect unusual behavior, and flag indicators of compromise. They focus on what the application is doing in production, not just what it looks like in code.
One benefit is that cloud security tools can detect problems that code scanners can’t see. Runtime secrets exposure, zero-days, and configuration drift are issues that often only show up once the system is live. These tools help detect real-world risks, such as unauthorized access, data breaches, or service disruptions, especially in large, distributed environments where infrastructure and application logic change frequently.
However, detection after deployment means the vulnerability has already been exposed to users or attackers. These tools don’t prevent issues from making it to production. They notify you when something is wrong, and that alert often arrives late in the game. The longer a flaw stays exposed, the more likely it is to be exploited, and the harder it is to contain the impact.
Fixing post-deployment problems isn’t simple. You might have to pause services, push emergency patches, roll back changes, or deal with partial outages. That creates downtime risk, leading to revenue loss and customer dissatisfaction, disrupting engineering teams, and putting pressure on incident response. Even minor configuration errors can take hours to reverse in a live environment, and any misstep can introduce new problems, potentially causing partial outages.
Cloud security tools are helpful for visibility and response. But they’re inherently reactive. They’re valuable in identifying active threats but unreliable for preventing them. Without earlier checks in the development and deployment process, you’re left responding to problems after they have become public. More damage tends to happen in that gap, and earlier-stage controls should have caught the issue first.
Why CI/CD Wins: Combining Context, Control, and Speed
Security in the CI/CD pipeline brings together the visibility, control, and enforcement needed across the entire development lifecycle. Unlike IDE tools, which operate in isolation, or cloud tools, which react after deployment, CI/CD security provides a comprehensive and proactive approach. It scans merged code, configuration files, infrastructure templates, and container definitions in one pass, making it possible to detect issues that only emerge when everything is connected.
Automated security checks embedded directly into the CI/CD workflow enforce policies with consistency and clarity. When high-severity vulnerabilities, misconfigurations, or exposed secrets are detected, the build process halts, providing developers with immediate feedback. By integrating security rules into the pipeline, teams eliminate uncertainty around scan execution and response. Everything is built into the process.
CI/CD scanning is designed to scale effortlessly across large codebases and multiple teams without interfering with local development workflows. Because scans run independently of a developer’s environment, they can leverage more advanced and resource-intensive analysis. This includes evaluating open-source dependencies, analyzing infrastructure-as-code templates, and running deep static and dynamic tests that would be impractical on a local machine.
A decisive advantage of CI/CD security is its ability to connect pre-production scanning with real-world production insights. Teams can feed runtime telemetry into the pipeline to fine-tune detection logic, reduce noise, and highlight the most relevant patterns. This supports shift-left and shift-right strategies, embedding security early in development while continually using production data to improve future checks.
IDE tools are ideal for enabling rapid development and catching surface-level issues early. Cloud security tools help monitor and protect what happens once code is live. However, regarding holistic policy enforcement, full-process visibility, and scalable, in-depth analysis, CI/CD is the most impactful control point. Treating the CI/CD pipeline as the primary enforcement layer ensures security is not an afterthought, but a core part of how software gets built.
Conclusion
Security doesn’t need to slow you down, but it needs to be built into the parts of your workflow that matter. The CI/CD pipeline gives you complete visibility into what’s being built, lets you enforce standards consistently, and integrates cleanly into how teams work. It’s the one place in the lifecycle where you get the right mix of context, control, and automation. Incorporating security into crucial parts of your workflow, like the CI/CD pipeline, doesn’t have to hinder speed.
This approach offers comprehensive visibility into the development process, allows consistent standard enforcement, and seamlessly fits into team workflows. The CI/CD pipeline provides an optimal balance of context, control, and automation within the development lifecycle.
IDE tools are helpful for developer hygiene, and cloud monitoring helps with visibility after deployment. But if you want to stop vulnerabilities before they reach production, your defenses will significantly impact CI/CD. Not all layers carry the same weight. Put your strongest security controls where you have the most leverage, right in the pipeline.
Book a demo with Qwiet to see how we make this possible.
FAQs
What is the best stage to integrate security in the software development lifecycle?
The CI/CD pipeline is the most effective stage for integrating security. It provides full context of the application, enforces policies automatically, and scales across teams. It catches issues earlier than cloud tools and with more depth than IDE plugins.
Why is IDE-based code security not enough?
IDE security tools offer helpful feedback during coding, but only provide a limited project view. They often miss broader issues like merged branch conflicts, runtime misconfigurations, and dependency vulnerabilities, visible only at later stages, like CI/CD.
How does CI/CD security scanning work?
CI/CD security scanning runs automatically on commits, pull requests, and builds. It can analyze the codebase, configurations, dependencies, and container specs. This enables checks for secrets, insecure APIs, and misconfigured permissions before code reaches production.
What are the limitations of cloud-based security tools?
Cloud-based tools detect issues after deployment, meaning vulnerabilities are already live. Fixes can require downtime, emergency patches, or rollbacks. They’re helpful for monitoring, but too late in the pipeline to prevent many risks.
How can teams reduce risk while maintaining development speed?
Teams can reduce risk by embedding automated security checks in the CI/CD pipeline. This approach catches critical issues before release without slowing down developers. IDE tools can support learning, and cloud monitoring can help with runtime visibility, but CI/CD is where scalable enforcement happens.
