Introduction
When keeping information private and secure over the internet, SSL/TLS is essential. This sturdy structure protects data sent between clients and servers on the internet. In this essay, we will navigate the twisting roads of SSL/TLS, exposing its complexities and hazards and providing strategies for overcoming some of its most challenging obstacles.
Overview of SSL/TLS
SSL/TLS relies on the user’s trust to function. If you’ve ever seen the little locked padlock in your browser’s address bar, you can thank the SSL/TLS protocol for that. Credit card details and other sensitive information are safe from prying eyes with this system in place.
Basics of SSL/TLS
Evolution of SSL to TLS
Originally introduced by Netscape in the early 1990s as Secure Sockets Layer (SSL), this protocol has undergone various iterations since then. Transport Layer Security (TLS) is the current standard for secure communication since it was built upon SSL and improved upon its weaknesses.
Core Principles and Components
The SSL/TLS protocol is characterized by three main features:
- Handshake: This delicate dance of back-and-forth communication establishes the parameters for a secure connection.
- Cipher Suites: Algorithms that encrypt data, ensuring the information remains gibberish to unauthorized entities even if intercepted.
- Certificates: Digital passports that ascertain the authenticity of a server, reassuring the client of its legitimacy.
A Glimpse at a Typical TLS Handshake

Understanding the sequence of events in a TLS handshake is pivotal to grasping how secure connections are established. Below is a simplified representation of this process:
| // Here’s a simplified view of what happens during a TLS handshake using Javascript functions: clientHello(); // Client reaches out for a secure connection serverHello(); // Server acknowledges and presents its certificate exchangeKey(); // Both agree on encryption keys for this session verifyCertificates(); // Certificates are cross-checked establishConnection(); // A secure tunnel is formed for data transfer |
The above showcases how a javascript client and server efficiently negotiate the terms of a secure session, ensuring encrypted and authenticated communication.
Common SSL/TLS Issues Developers Encounter
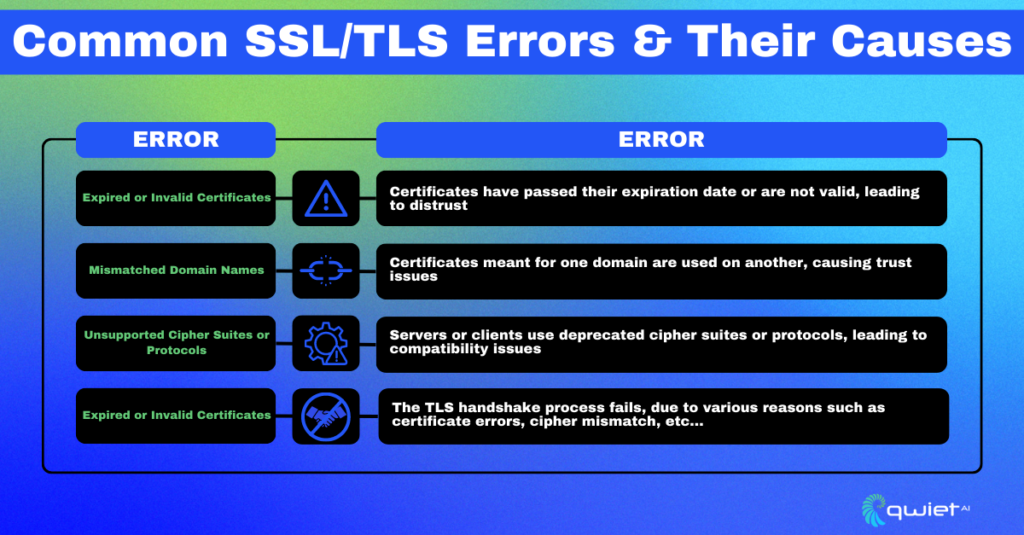
Expired or Invalid Certificates
Certificates with photos serve as time-limited digital passports. After a certain age, browsers stop trusting them, which causes problems. They verify that the server you are talking to is who it says it is. However, once a certificate has expired, all sense of security is gone.
Mismatched Domain Names
Imagine being shown an ID where the photo matches, but the name doesn’t. A similar scenario arises when a certificate designed for one domain is employed on another. It raises red flags, leading to a breach of trust.
Unsupported Cipher Suites or Protocols
Every so often, cipher suites or protocols get deprecated due to vulnerabilities. However, some servers or clients cling to them, leading to compatibility issues. It’s akin to reading a letter written in an old, forgotten dialect.
Delving into a Failed TLS Handshake
While the above outlines a successful handshake, not all negotiations go smoothly. Here’s a hypothetical situation where a TLS handshake might fail due to certificate expiration:
| // Here’s an illustrative snippet representing a failed handshake: try { startHandshake(); } catch (error) { if (error === ‘CERTIFICATE_EXPIRED’) { console.error(‘TLS handshake halted due to an expired certificate.’); } } |
The above demonstrates how developers can handle and diagnose specific errors during the handshake process, enabling corrective action.
Tools and Techniques for Debugging SSL/TLS Issues
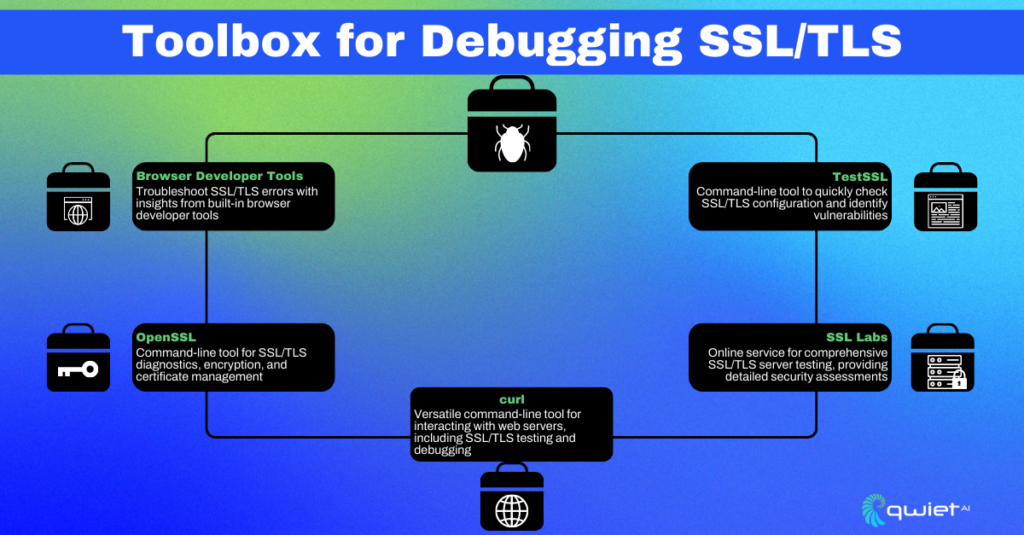
Browser Developer Tools
Modern browsers have come a long way from mere tools for viewing web pages. They’re now packed with powerful developer tools that offer granular insights into various aspects of a website, including SSL/TLS-related errors.
How They Help: When you land on a webpage and encounter an SSL error, your browser’s developer console will typically flag it with a clear message. For instance, you might see warnings related to mixed content (secure and non-secure elements on one page), or a direct notification that the website’s certificate is expired or not trusted.
Usage: To access these tools, right-click on a webpage and select “Inspect” or “Inspect Element”, then navigate to the ‘Console’ or ‘Security’ tab. Here, you’ll see a log of errors, warnings, and informational messages, with SSL/TLS issues typically highlighted in red or with a warning icon.
Advantage: The immediacy of these tools — they’re right there in the browser, no additional software required — makes them an indispensable first line of defense when troubleshooting SSL/TLS issues. They can quickly pinpoint the nature and source of the problem, guiding developers on the next steps for resolution.
Command-Line Crusaders: OpenSSL and curl
For those who prefer to roll up their sleeves and dive deep, the command line provides robust tools like OpenSSL and curl.
OpenSSL: An open-source toolkit for SSL and TLS, OpenSSL offers a suite of command-line tools for creating and managing certificates, keys, and other cryptographic tasks. For instance, with OpenSSL, one can connect to a remote server and retrieve its certificate or even test the server’s SSL configuration like below:
| openssl s_client -connect example.com:443 |
curl: A versatile command-line tool for transferring data with URLs, curl supports many protocols, including HTTPS. When faced with SSL issues, curl can provide verbose outputs, helping pinpoint problems as demonstrated below:
| curl -v https://example.com |
Advantage: These command-line tools offer a detailed look into SSL/TLS diagnostics, allowing developers to inspect, test, and debug issues with precision directly from their terminal.
Step-by-Step Debugging Process
Pinpointing the Problem
The first step in any debugging journey is identifying the crux of the issue. Is the problem rooted in an expired certificate or a protocol mismatch?
Verifying Capabilities
The dance between client and server necessitates a shared set of protocols and cipher suites. Ensure this compatibility to avoid missteps.
Certificate Scrutiny
Every certificate tells a story. Ensuring its authenticity and validity is crucial to establishing trust.
| # Checking a certificate’s validity: openssl x509 -in server.crt -text -noout |
Server Configuration Examination
Reviewing server configurations provide insights into potential inconsistencies or vulnerabilities lurking in the shadows.
| # Extracting server SSL/TLS details: openssl s_client –connect example.com:443 -msg |
Mitigating Common SSL/TLS Pitfalls
Keep an Eye on the Calendar
Certificate expiry is one of the most common causes for SSL/TLS errors. Ensure that certificate renewals are prominently marked on your calendar. An expired certificate not only disrupts your web services but also erodes trust with your users. Better yet, consider using automated renewal processes available with some services, such as Let’s Encrypt. By automating renewals, you eliminate the risk of human error, ensuring uninterrupted and secure service for your users.
Trust Only the Best
Certificates are the backbone of the SSL/TLS protocol. Regarding Certificate Authorities (CAs), not all are created equal. Just as you’d only trust sensitive information with a reputable entity, ensure you obtain certificates from established, trustworthy CAs. These CAs have rigorous validation processes and are recognized and trusted by most modern browsers and operating systems. Using a certificate from a reputable CA ensures that your users won’t encounter trust issues when accessing your site.
Stay Updated
The landscape of web security is ever-evolving. As threats change and grow, so do the tools and methods to counter them. Ensure server configurations stay updated, avoiding deprecated or vulnerable cipher suites. Outdated configurations can expose your site to vulnerabilities, impacting security and performance.
Proactive Monitoring
Complacency is a silent adversary in the world of SSL/TLS. Proactive monitoring is your best defense against unforeseen SSL/TLS issues. While setting up your SSL/TLS configurations correctly is essential, ongoing monitoring ensures they remain effective over time. Employ monitoring tools and services that scan your servers and provide real-time alerts for potential issues. This proactive approach ensures that you’re always one step ahead, resolving issues before they escalate and impact your users.
Conclusion
Navigating the intricate web of SSL/TLS is pivotal for upholding digital trust and safeguarding data. As cybersecurity continually evolves, the tools highlighted in this guide are invaluable. However, it’s the all-encompassing strategy of Qwiet AI that truly enables developers to tackle both present and looming security issues in their code quickly and accurately. Schedule a demo with us today, and transform your application security paradigm.