Introduction
Today, we delve deep into a commonly perplexing topic in web security: Mixed Content Warnings. Through this article, we aim to shed light on these warnings, their implications, and how their resolution can significantly enhance the safety of your web applications.
Understanding Mixed Content
In the online world, “Mixed Content” is a term that has a particular meaning. It describes a situation where an initial HTML document is loaded over a secure HTTPS connection, but other resources (such as images, videos, stylesheets, and scripts) associated with the page are loaded over an insecure HTTP connection.
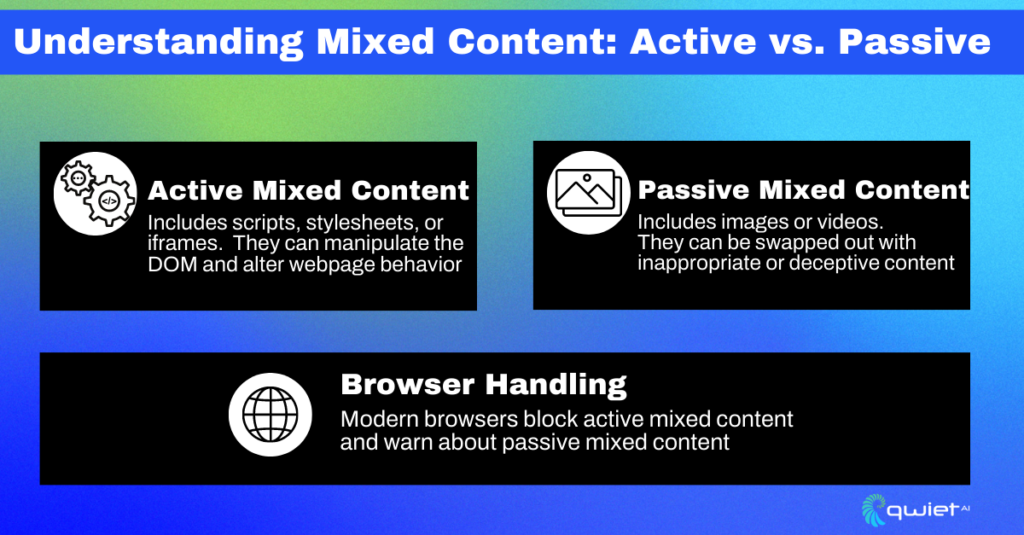
This content can be broadly categorized into two types: active and passive. Active mixed content, including scripts, stylesheets, or iframes, is potentially dangerous because it can manipulate the Document Object Model (DOM) and alter the web page’s behavior. Passive mixed content, like images or videos, while not as potent as active content, poses risks because an attacker could swap out these resources with inappropriate or deceptive content.
Having mixed content on your webpage opens a pandora’s box of security vulnerabilities. It makes your website susceptible to eavesdropping and man-in-the-middle attacks. Attackers can view and modify the mixed content requests, potentially compromising sensitive user data.
How Browsers Handle Mixed Content
Different web browsers have varying approaches to handling mixed content. While most modern browsers block specific types of mixed content (typically active mixed content), they also warn when other types of mixed content (usually passive mixed content) are detected.
The mixed content warnings are usually accessible in the browser’s JavaScript console. These warnings provide a detailed description of the exact nature of the mixed content, including the specific resources loaded insecurely and their sources. This information is invaluable when troubleshooting mixed content issues.
The Impact of Mixed Content on Website Security
Mixed content can seriously undermine the security that an SSL/TLS secured site provides. The SSL/TLS protocols establish a secure, encrypted link between a web server and a client, usually a web browser. The HTTPS protocol, which stands for HTTP Secure, uses SSL/TLS to protect the data transmitted between clients and servers from being intercepted, tampered with, or forged.
However, when mixed content is present, HTTPS’s integrity and confidentiality can be seriously compromised. This is because attackers can exploit the HTTP content to intercept or alter the data being exchanged between the client and server. This weakens the overall security of your website and exposes your users to potential attacks.
Strategies to Identify Mixed Content in Your Web Application
There are multiple ways to detect mixed content in your web application. The most straightforward method involves using your browser’s developer tools. Most modern browsers will log a warning in the JavaScript console if they encounter mixed content. These warnings provide the exact URLs of the mixed content, allowing you to locate and address the issue quickly.
Automated tools and online scanners also help detect mixed content. These tools scan your web application’s pages and report any mixed content. Some advanced tools can also scan your CSS and JavaScript files for references to insecure HTTP URLs.
To illustrate here is a simple JavaScript snippet that can help detect passive mixed content on your webpage:
| // Find all img elements that have an http source let images = document.querySelectorAll(‘img[src^=”http://”]’); console.log(`Found ${images.length} mixed content images.`); |
Once you’ve identified the mixed content, the next step is to interpret the results and take corrective action. This typically involves checking the URLs flagged as mixed content and determining where they are referenced in your application.
Solutions and Best Practices to Handle Mixed Content
There are several effective strategies to tackle mixed content issues:
- Content Security Policy (CSP): A CSP can prevent various mixed content issues. A CSP is a response header that allows you to control the resources loaded on your webpage. Here’s an example of a CSP that could help with mixed content:
| Header set Content–Security–Policy “default-src https: data: ‘unsafe-inline’ ‘unsafe-eval'” |
- HTTPS for all resources: One of the simplest ways to prevent mixed content is to load all your page’s resources over HTTPS.
- Automatic upgrade of insecure requests: Modern browsers can upgrade all mixed content requests to secure connections automatically. Here’s an example:
| Header always set Content–Security–Policy: “upgrade-insecure-requests;” |
- Fixing mixed content warnings: This involves changing all your HTTP links to HTTPS. This must be done in your HTML, CSS, and JavaScript files. For example:
| <!– Change this –> <img src=“http://example.com/image.jpg”> <!– Into this –> <img src=“https://example.com/image.jpg”> |
Prevention: Avoiding Mixed Content Issues in the Future
The best way to handle mixed content is to avoid it altogether. Adopt secure coding practices to prevent mixed content issues. This includes loading all external resources over HTTPS:
| <!– Securely loading an external script –> <script src=“https://example.com/script.js”></script> |
Also, consider implementing continuous monitoring of your web applications for mixed content. Regularly scanning your application helps detect mixed content as it arises and allows for prompt remediation. Keeping abreast of the latest trends and guidelines in web security is also vital in maintaining a secure web application.
Conclusion
Mixed content warnings are more than just an annoyance for developers; they’re a significant indicator of potential security vulnerabilities in a web application. Addressing these warnings ensures your website maintains the highest level of security and builds trust with your users. We’ve journeyed from understanding what mixed content is, through its threats, to the steps for mitigating these risks.
