Introduction
Let’s dive into the fascinating world of web security, specifically discussing a notorious threat – clickjacking. Imagine a user clicking on a button thinking they like a photo but instead transferring money from their bank account. Scary, right? That’s clickjacking for you. This threat not only compromises user trust but can also deal a financial blow to businesses.
Basics of Clickjacking
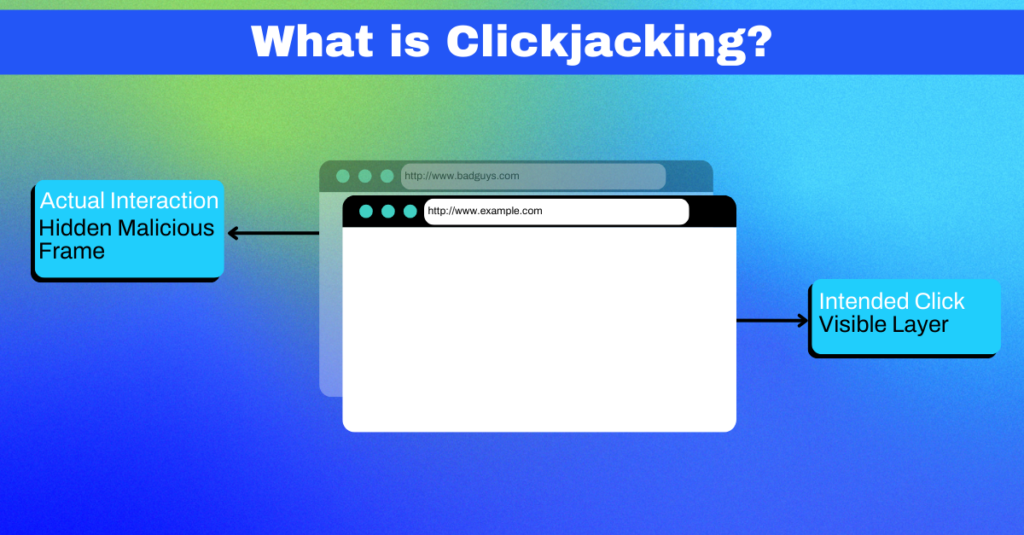
What is Clickjacking?
Ah, clickjacking—sounds like something straight out of a spy movie, doesn’t it? But in the digital realm, it’s far from fiction.
Clickjacking is a sleight-of-hand trick in the cybersecurity world. It’s a method where attackers hoodwink users into interacting with something entirely different from what they think they’re interacting with.
Picture this: you believe you’re clicking on a benign link, say to upvote a forum post, but instead, you’ve just followed another link that downloads malware onto your device. Spooky, right? Clickjacking is especially pernicious and can hijack innocent user actions, turning them into unintentional attacks against themselves or others.
Now, how does it work? The attacker camouflages malicious links, buttons, or frames under seemingly innocent ones. They create a facade, a mirage that users trust. And behind that facade? Well, that’s where the harm lurks. You could be subscribing to a service, liking a controversial page, or even transferring funds without knowing you did it.
Common Methods in Clickjacking
So, how do these digital magicians pull off their tricks? There are various ways to set the stage for a clickjacking attack, but let’s delve into some of the most common methods.
- Using Transparent Layers: One popular tactic is to overlay a transparent, malicious layer over a legitimate webpage. Because the malicious layer is invisible, when you think you’re interacting with the legitimate page, you’re actually interacting with the hidden layer.
- Iframe Manipulation: Ah, iframes—those handy HTML elements that let you embed one webpage into another. Well, they’re a double-edged sword. In clickjacking, attackers use iframes to overlay malicious content over legitimate pages. Sometimes, these iframes are also transparent or set to low opacity, so the user can’t see them but can unwittingly interact with them.
- Positioning Trickery: Attackers can be quite crafty when it comes to arranging elements on a webpage. They might manipulate the CSS to align the malicious elements perfectly with innocent-looking buttons or links, leading to misplaced clicks.
- Cursor Spoofing: Ever seen your cursor change shape on a webpage? Attackers can change what the cursor looks like or where it appears, throwing off your sense of where you’re clicking.
- Timing Attacks: Sometimes, it’s all about timing. Attackers might momentarily display a legitimate button for you to click on but then quickly replace it with a malicious one in a split second—just long enough for you to fall into the trap.
- Mobile Tapjacking: In the mobile world, tapjacking follows the same principle but exploits the touch interface. It’s the same old wolf, but in a different kind of sheep’s clothing.
Curious about how to defend against these nefarious tactics? Don’t worry, we’ll get there. Just remember, understanding your enemy is the first step in any battle. And in the ever-evolving world of cybersecurity, staying informed is your shield and sword. Ready for the next level? Let’s dive deeper.
X-Frame-Options Header: The First Line of Defense
What is the X-Frame-Options Header?
X-Frame-Options is an HTTP header designed to defend against clickjacking by controlling who can embed your content.
Its Role in Clickjacking Prevention
By setting up the X-Frame-Options header correctly, you can dictate if your site can be embedded in iframes and, if so, where from. This blocks most basic clickjacking attempts right in their tracks.
Properly Configuring the X-Frame-Options Header
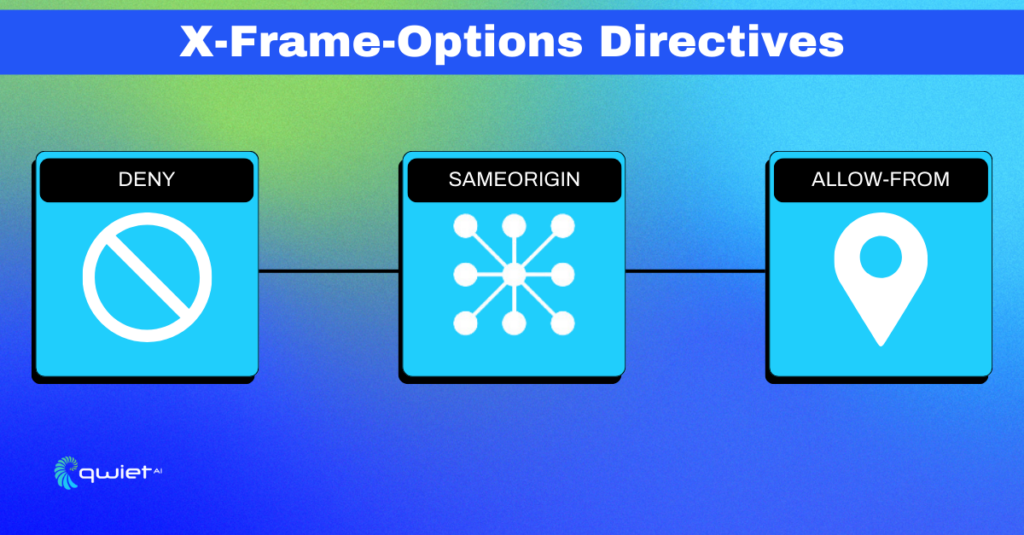
Understanding Directives:
Alright, time to unravel the nuts and bolts. The X-Frame-Options header has three key directives you can use. Let’s give them a more detailed examination.
DENY: When you set this directive, you shout, “Nobody puts Baby in a corner!” Your webpage will refuse to be displayed in an iframe—no exceptions. This is as hardline as it gets.
Example:
| X-Frame–Options: DENY |
SAMEORIGIN: This is like saying, “Family members only, please!” Your content can be framed, but only by webpages originating from the same domain, protocol, and port.
Example:
| X-Frame–Options: SAMEORIGIN |
ALLOW-FROM uri: This directive is like your VIP list at a party. Only sites specified by the URI can frame your content. However, note that this is becoming deprecated and not all modern browsers support it.
Example:
| X-Frame-Options: ALLOW-FROM https://trusted-site.com |
Implementing X-Frame-Options in Different Server Environments
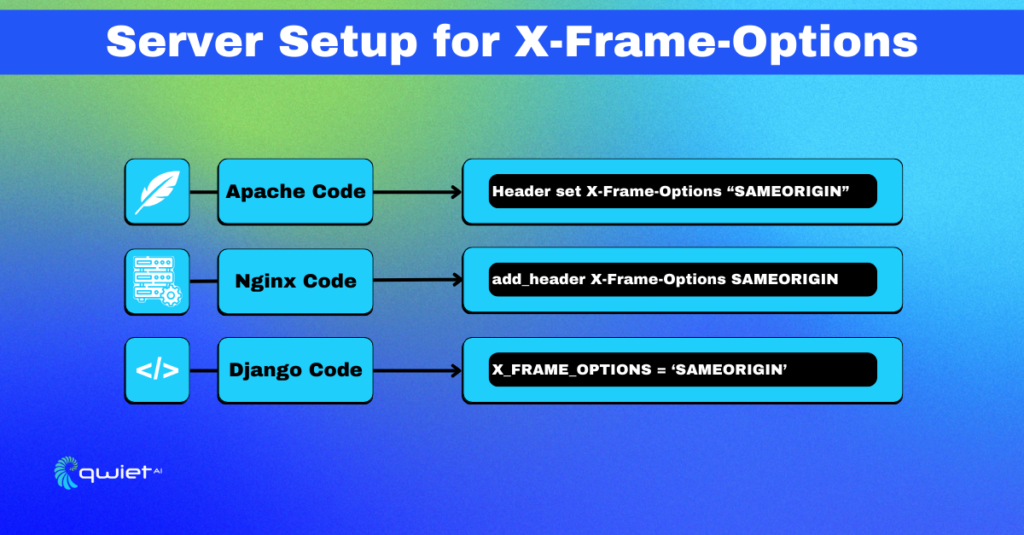
Apache: Old but gold, Apache has been around for ages. To set up X-Frame-Options in Apache, add the following line to your .htaccess file or your Apache config file.
| Header always set X-Frame-Options “SAMEORIGIN” |
Nginx: The rising star of web servers, Nginx has a simpler syntax. Open your Nginx configuration file and add this line in the server block.
| add_header X-Frame–Options SAMEORIGIN; |
Django: Ah, Python’s pride for web development. In your Django settings.py file, you can define the X-Frame-Options directive like this:
| X_FRAME_OPTIONS = ‘SAMEORIGIN’ |
Express.js: Node.js aficionados, this one’s for you. In your Express application, you can set the header using middleware.
| app.use((req, res, next) => { res.setHeader(‘X-Frame-Options’, ‘SAMEORIGIN’); next(); }); |
Testing and Validating Your Configuration
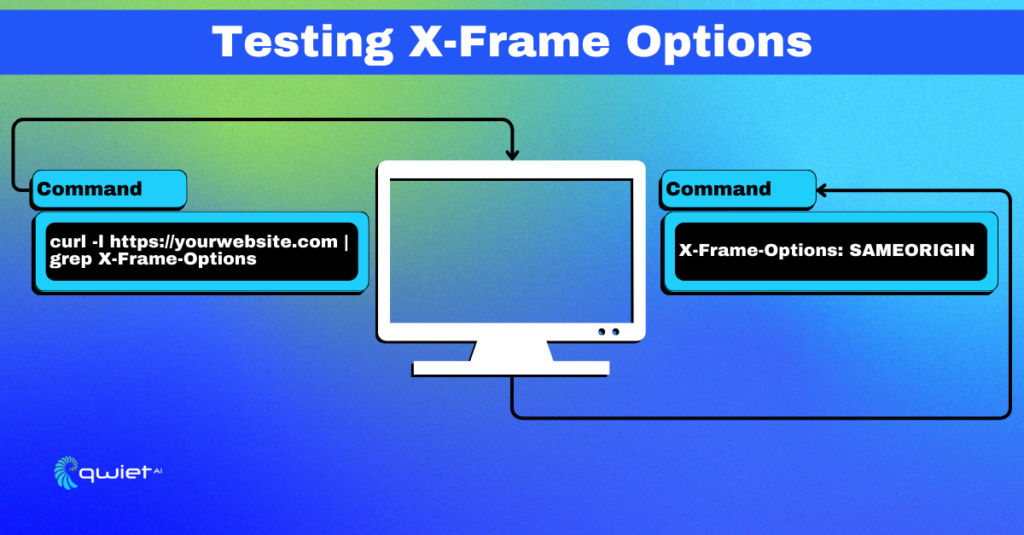
After deploying your defenses, it’s testing time. Pop open your terminal and use curl to inspect the HTTP headers.
| curl -I https://your-domain.com |
Look for the X-Frame-Options header and ensure it’s set to your desired value. In your browser, use developer tools to check the ‘Network’ tab for the same info.
Beyond X-Frame-Options: Comprehensive Clickjacking Defense
While X-Frame-Options is your first line of defense, adding more layers is beneficial. Content Security Policy (CSP) gives you the frame-ancestors directive, allowing you to specify which domains can embed your content.
| Content-Security-Policy: frame-ancestors ‘self’ https://trusted-site.com; |
JavaScript-based defenses, like checking if your site is being framed and breaking out of it, exist, but they’re like training wheels—helpful but not fail-safe.
Conclusion
You’ve dived deep into the complexities of clickjacking defense, from mastering directives to successful implementation and validation across server environments. While X-Frame-Options and other techniques arm you with robust initial defenses, remember that cybersecurity is an ever-changing landscape. If you’re looking to identify clickjacking vulnerabilities and other potential security threats proactively, Qwiet AI is designed to do just that. Don’t wait for an attack; stay ahead by booking a demo with our team today.