Over the last few weeks, log4j has been the focus in most organizations. It continues to dominate tech media as the FTC threatens action against unpatched systems and Microsoft warns of continued exploits of the vulnerability. We have covered it in detail here, here, and here. In this blog, we will focus on how you can easily detect vulnerable versions of log4j in your Java applications using ShiftLeft CORE.
Through February 28th, 2022, new ShiftLeft CORE users will receive our enterprise features free for 60 days for up to 20 applications. Once you create your account and do an upgrade to the premium trial, please follow the steps here to analyze your Java applications.

It’s just three steps — download the ShiftLeft CLI, authenticate, and execute sl analyzeby providing it the path to your JAR or WAR file. This needs to be done from the source code directory so that we can pick up the dependency information as well. In addition to looking for vulnerabilities in your dependencies, this step also analyzes your custom code for OWASP Top 10 vulnerabilities.
Using the ShiftLeft dashboard, you can see details of the vulnerabilities found during the analysis.
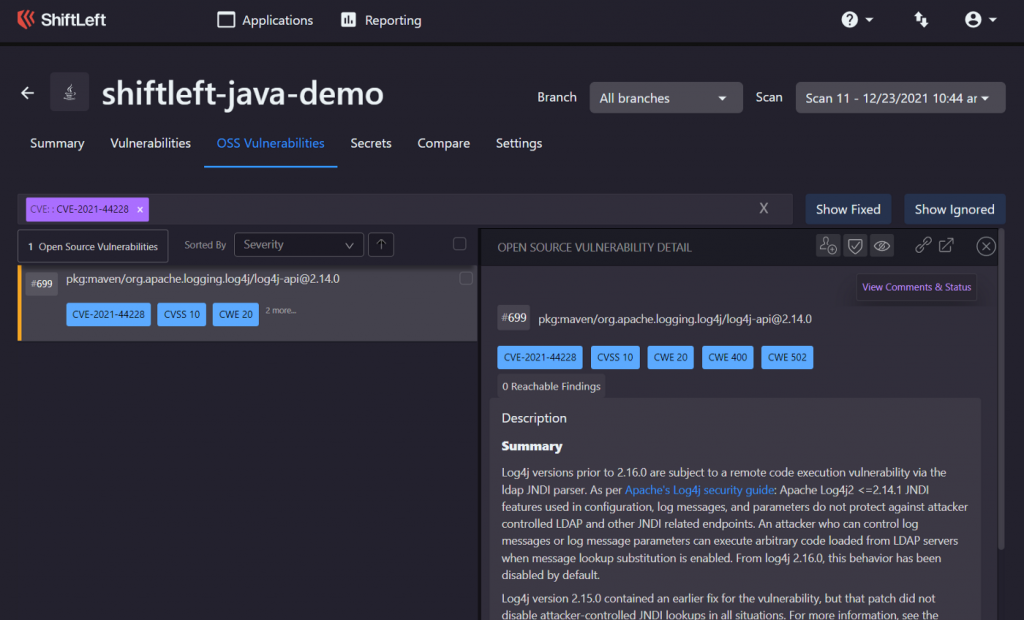
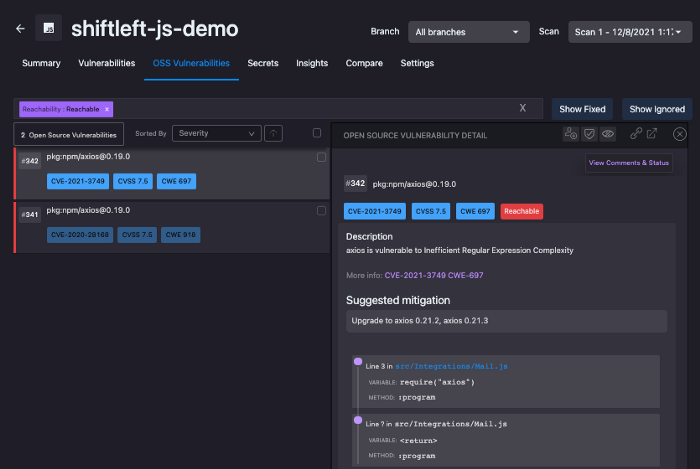
You can also see details of vulnerabilities found in your custom code:
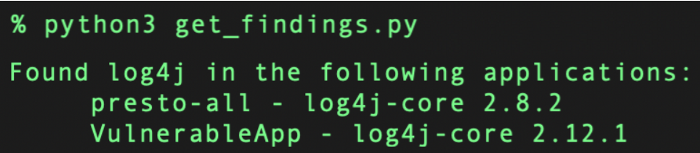
Another use case that we heard from customers is the ability to see which of their applications have vulnerable versions of log4j. Towards this, we have created a simple search API that does exactly this.
https://www.shiftleft.io/api/v4/orgs/{orgID}/findings?search=log4j&search=cve
You can see the full API spec here. For example, one can use the API and easily get an output like this:
Sign up for a free account of ShiftLeft CORE to get enterprise features free for 60 days for up to 20 applications through February 28th, 2022.
Do reach out to us at [email protected] if you have any questions!
