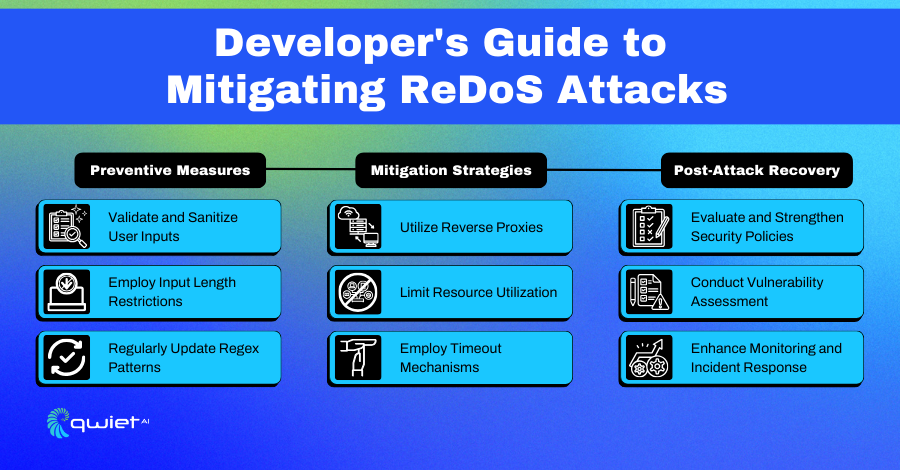
Introduction
In the sprawling expanse of cyberspace, developers diligently weave intricate digital webs, fostering connectivity and enabling the digital experiences that have become integral to our daily lives. Amidst these strands, however, lurk potential threats, one of which stands out due to its silent yet potentially paralyzing impact: the Regular Expression Denial of Service (ReDoS) attack. This discourse endeavors to guide developers through the labyrinthine complexities of Regex and ReDoS, exploring mitigation strategies and protective mechanisms.
Understanding ReDoS
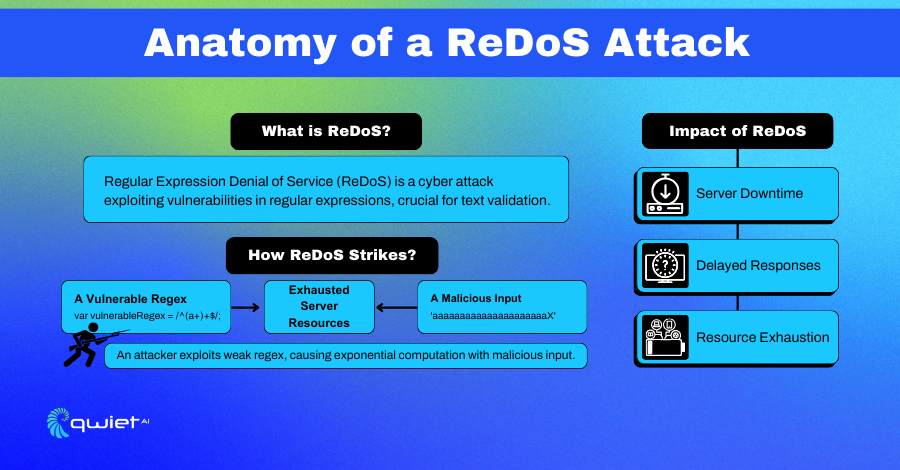
Regular Expression Denial of Service (ReDoS) is a formidable and often underappreciated threat in cybersecurity. It’s a subtle yet destructive attack that capitalizes on the vulnerabilities inherent in regular expressions, a fundamental tool in a developer’s arsenal for text parsing and validation.
At its core, ReDoS attacks manipulate the time complexity of regex processing. Regular expressions, especially those poorly crafted, can be susceptible to causing extensive backtracking.
In simpler terms, given a certain input type, the regex engine might end up checking and rechecking matches, exponentially increasing the computation time. This can be particularly devastating when a regex engine employs a backtracking algorithm.
Consider a regex pattern that matches a simple string but is constructed with nested quantifiers like /(a+)+b/. This pattern, when faced with a string like ‘aaaaaaaaaaaaaab’, forces the regex engine to evaluate a vast number of combinations before arriving at a match or a failure.
For instance, see below:
| // Exploitable Regex var vulnerableRegex = /^(a+)+$/; |
An attacker, exploiting this regex with a string like ‘aaaaaaaaaaaaaaaaaaaaaX’, can bring a server to its knees, delving it into exponential computation time and hindering its ability to serve genuine requests.
In a practical context, a seemingly innocent input string can tie up a server’s resources, preventing it from servicing other legitimate requests. The impact is twofold: it not only disrupts the service but also consumes server resources, leading to potential additional costs and maintenance challenges.
Mechanisms for ReDoS Mitigation
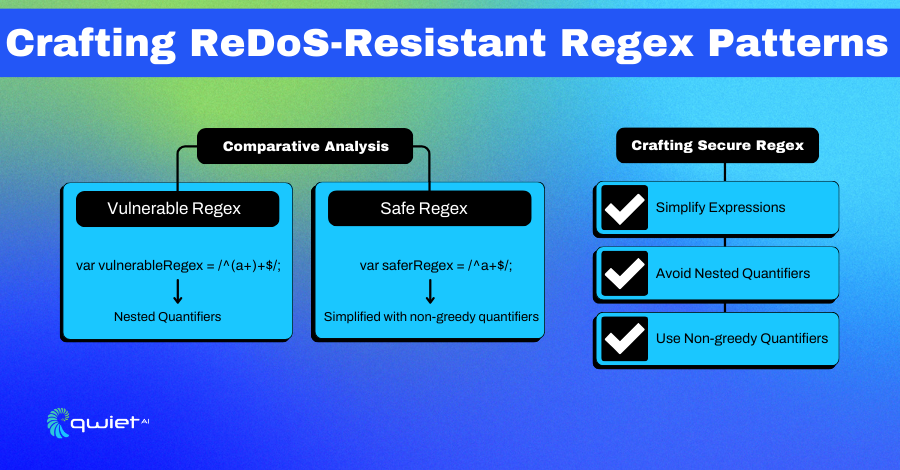
1. Crafting Robust Regex:
Developers stand as the first line of defense, and crafting robust regex expressions resistant to ReDoS becomes paramount.
| // Safer Regex var saferRegex = /^a+$/; |
Simplifying expressions, avoiding nested quantifiers, and utilizing non-greedy quantifiers where feasible can create expressions less prone to exploitation.
2. Employing Timeout Mechanisms:
A reliable safeguard involves incorporating timeout mechanisms that halt regex processing if execution time surpasses a predefined threshold, ensuring service continuity even amidst an attack.
3. Utilizing Regex Analyzers:
Leveraging tools like regex101 or SafeRegex, developers can analyze and evaluate the safety of regex patterns, identifying potential vulnerabilities before deployment.
4. Resilience through Regex Alternatives:
In scenarios where regex usage becomes a discernible risk, considering alternatives like string methods or parser generators, which might be less susceptible to exploitation, can offer secure pathways for text processing.
Adopting Holistic Strategies Against ReDoS
1. Rate Limiting
By implementing rate limiting, developers create a temporal shield, limiting the frequency and volume of requests a single client can make, curbing an attacker’s ability to induce service disruption.
- Types of Rate Limiting: There are several approaches to rate limiting, such as fixed windows, sliding window logs, and token bucket algorithms. Each has its merits and can be chosen based on the application’s specific needs.
- User Differentiation: Rate limits can be applied differently to various user types. For example, regular users might have a lower rate limit than premium users.
- Dynamic Rate Limiting: Advanced implementations can adjust rate limits in real time based on traffic patterns and server load. During peak times or when an attack is suspected, the system can automatically lower rate limits.
2. Caching
Caching mitigates Regular Expression Denial of Service (ReDoS) attacks by storing regex operation results, reducing server load by avoiding repetitive processing for similar requests.
Effective caching involves using in-memory systems like Redis for fast retrieval and carefully selecting cache keys, typically hashes of input strings or patterns, to reduce collisions. Additionally, managing cache lifecycles and using distributed caching in high-traffic environments enhances performance and resilience against ReDoS attacks.
Advanced Mitigation Techniques
1. Employing Adaptive Algorithms:
Adaptive algorithms represent a sophisticated approach to mitigating ReDoS attacks. These algorithms are designed to learn and evolve based on the patterns of incoming requests, allowing them to adjust regex evaluation strategies in response to detected threats dynamically.
How They Work:
- Monitoring and Analysis: Adaptive algorithms start by continuously monitoring incoming requests. They analyze patterns, frequencies, and the computational resources consumed during regex evaluations.
- Pattern Recognition: Using data analytics, these algorithms can identify abnormal behavior that might indicate a ReDoS attack, such as repeated requests with complex strings that are known to cause extensive backtracking in regex evaluations.
- Dynamic Adjustment: Upon detecting potential ReDoS patterns, the algorithm dynamically adjusts regex strategies. This could involve switching to pre-validated or simpler regex patterns, using string methods for specific validations, or temporarily increasing resource allocation for regex processing.
How to Implement
Say you had a web application that uses regex for email validation. An adaptive algorithm could be set up to monitor the time taken for these validations.
Suppose the time exceeds a certain threshold, indicating potential ReDoS. In that case, the algorithm might switch to a more straightforward, more efficient regex pattern or even a non-regex-based validation method for a while.
2. Microservices Architecture: Isolation as a Protective Mechanism:
Microservices architecture offers a robust structural defense against ReDoS attacks by isolating services. This architecture breaks down the application into smaller, independently deployable services, each performing a specific function.
- Isolation of Impact: In a microservices architecture, if one service handling regex operations is attacked, it doesn’t paralyze the entire application. Other services continue to function independently, thereby limiting the overall impact.
- Distributed Load: Since each service is separate, the load caused by a potential ReDoS attack is contained within that specific service, preventing it from overwhelming the entire system.
- Easier Monitoring and Scaling: Individual services can be monitored more effectively for unusual patterns indicative of ReDoS attacks. Additionally, services more prone to such attacks can be scaled independently to handle increased loads without affecting other application parts.
How to implement:
Let’s use the scenario where a user authentication service in an application uses complex regex for password validation. This authentication service is separated from services like user data retrieval or payment processing in a microservices architecture.
If a ReDoS attack targets the authentication service, it will not disrupt the functionality of retrieving user data or processing payments, thereby maintaining overall application integrity.
Conclusion
While a testament to human ingenuity and connectivity, the vast digital ocean hides within it swirling vortices of threats like ReDoS attacks that seek to engulf our creations into abyssal depths. Developers have a potent arsenal ranging from crafting robust regex, employing timeout mechanisms, utilizing analyzers, adopting holistic strategies like rate limiting and caching, navigating through the challenges, and employing advanced mitigation techniques.
To improve your appsec security posture, reach out to our team today to see how Qwiet can help you take a proactive approach to avoid attacks similar to ReDoS attacks.