Introduction
Race conditions linger as elusive threats in the domain of concurrent programming, creating a fertile ground for inconsistencies and unforeseen security vulnerabilities. These subtle programming bugs arise when multiple processes access shared resources simultaneously, leading to unpredictable and undesirable outcomes. This article will journey through the labyrinth of race conditions, exploring their implications on security and offering strategies to navigate and mitigate these treacherous terrains in concurrent programming environments.
Understanding Race Conditions
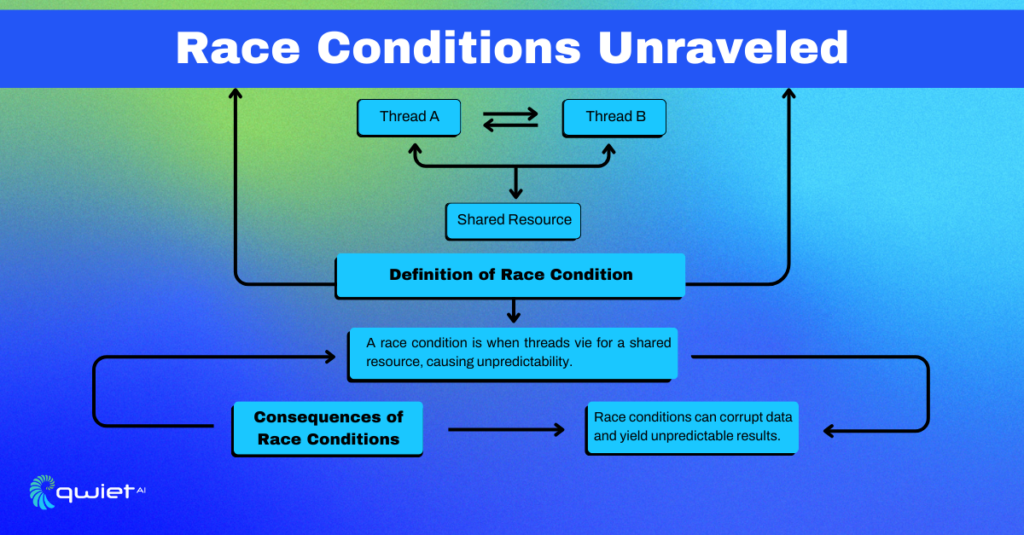
In concurrent programming, race conditions are a common issue that occurs when two or more threads or processes access shared data simultaneously. Let’s explore this concept further with an example and explanation.
Lets look at a simple Java program where a shared resource is accessed and modified by multiple threads concurrently:
| public class RaceConditionDemo { private static int sharedResource = 0; public static void main(String[] args) { Thread thread1 = new Thread(() -> incrementResource()); Thread thread2 = new Thread(() -> incrementResource()); thread1.start(); thread2.start(); } public static void incrementResource() { sharedResource++; } } |
In this example, sharedResource is a shared variable that two threads, thread1 and thread2, are trying to increment. Because these threads operate simultaneously without any synchronization mechanisms, they might not update sharedResource correctly. This lack of synchronization and orderly management leads to race conditions, resulting in unpredictable values of sharedResource.
To understand why this happens, consider this scenario: both threads might read the value of sharedResource at the same time, seeing it as 0. They then both increment it by 1. Instead of being updated to 2, as intended, sharedResource might only be incremented once, resulting in a final value of 1.
Such erratic outcomes are problematic because they lead to data inconsistency and logical errors within the application. These issues highlight the significance of managing access to shared resources meticulously to prevent race conditions and ensure the reliable execution of concurrent programs.
Security Implications of Race Conditions
Data Corruption and Inconsistency:
In concurrent programming, data corruption and inconsistency happen when parts of a program try to modify shared data simultaneously without proper coordination, leading to confusion and mistakes, much like a chaotic group project.
Synchronization is a tool that manages the access to shared data, ensuring it stays accurate and reliable, thereby enhancing the program’s overall functionality and effectiveness. This method keeps the “group project” of a computer program well-coordinated, preventing errors and ensuring accurate outcomes.
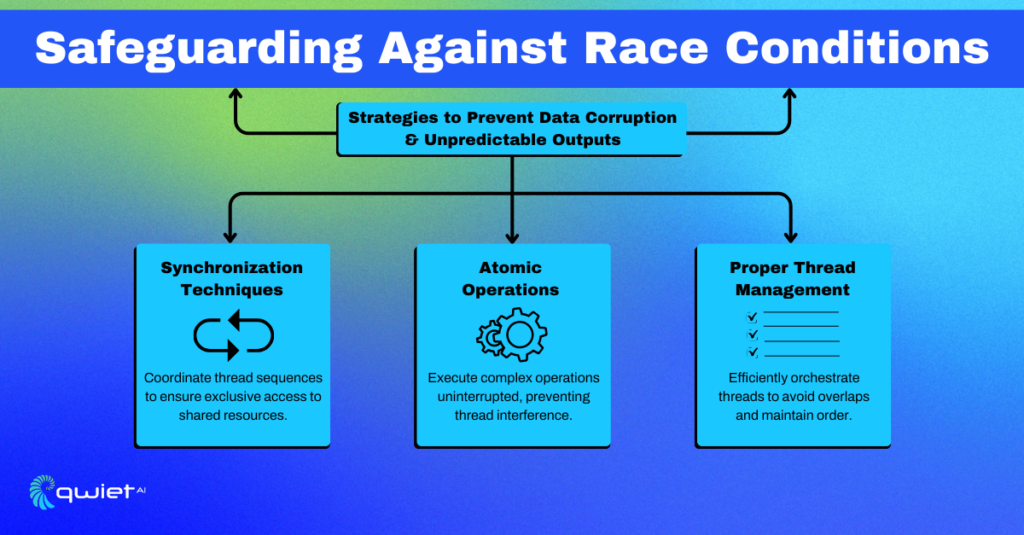
Mitigation Strategies:
- Implement synchronization mechanisms to ensure that only one process can access the shared resource at a time.
- Employ atomic operations and concurrency-safe data structures to preserve data integrity.
| // Synchronized method to avoid data corruption public synchronized static void incrementResource() { sharedResource++; } |
In this revised example, the synchronized keyword is used to ensure that the incrementResource method can only be accessed by one thread at a time, preventing data corruption.
Unauthorized Access and Information Disclosure:
Race conditions can potentially be a weak link in the security of computer systems, allowing unauthorized access to sensitive information. They can create loopholes where typical security checks, such as passwords, are bypassed by attackers.
For example, a flaw in a login system due to a race condition might enable a hacker to access protected parts of a system, leading to the exposure of confidential data. It is essential to identify and rectify race conditions promptly to maintain the security integrity of systems, ensuring that information remains inaccessible to unauthorized users and safeguarded against potential breaches.
Mitigation Strategies:
- Rigorously validate input and enforce access controls to secure sensitive information.
- Regularly audit and update security configurations to patch vulnerabilities promptly.
Best Practices in Confronting Race Conditions
In-Depth Concurrency Testing:
Concurrency testing involves simulating a busy, real-world environment where different parts of a program run at the same time. This helps find and fix issues that could disrupt the program’s smooth operation, ensuring that it works reliably under actual conditions with multiple ongoing processes.
Comprehensive Code Reviews and Static Analysis:
In this step, the code is thoroughly checked by team members and special tools like Qwiet for any overlooked vulnerabilities related to concurrency. This two-pronged approach helps strengthen the program’s defenses, making sure it runs securely and efficiently when performing multiple simultaneous actions.
Strategic Design Principles:
Optimizing software involves improving its design to make it more efficient and secure. A key focus is mutable data—information that can change during the program’s execution. A smart approach to managing mutable data is by isolating and securing it.
Lets look at the following C# code snippet:
| public class Resource { private object _lock = new object(); private int _data; public void UpdateData(int newValue) { lock(_lock) { _data = newValue; } } } |
In this example, the _data is mutable data. To ensure it is safely updated, a ‘lock’ is used. This ‘lock’ acts like a security guard, allowing only one part of the program to access and change _data at a time. By doing this, the code helps prevent mistakes and keeps the data consistent and secure, improving the overall software design.
4. Use of Concurrency Safe Constructs:
Concurrency-safe constructs are specialized tools used in programming to prevent race conditions—errors that occur when multiple operations try to modify data simultaneously. These tools include atomic operations and lock-free data structures.
In Java, the AtomicInteger class is commonly used for this purpose.
| import java.util.concurrent.atomic.AtomicInteger; AtomicInteger counter = new AtomicInteger(0); counter.incrementAndGet(); |
In this Java example, AtomicInteger ensures that the increment operation on counter is completed safely and correctly without interruption from other operations, enhancing the reliability and accuracy of the program.
Conclusion
Race conditions in concurrent programming are complex challenges that can jeopardize the security of applications through unexpected errors and unauthorized access. Managing these issues necessitates precise coordination, rigorous testing, continuous updates to security protocols, and an ongoing commitment to learning and adapting to new threats and strategies.
To further enhance the security of your application, schedule a call with our team to see how Qwiet can help improve your app’s security posture.