Introduction
In software development, third-party libraries are akin to the gears in a well-oiled machine – essential and powerful, yet requiring careful handling. While they bring efficiency and functionality, they also introduce security risks that can compromise your application. This article aims to guide developers through the labyrinth of third-party library security, offering best practices for safe dependency management.
The Risks of Third-Party Libraries

Third-party libraries, though beneficial, can be a double-edged sword. They may contain vulnerabilities or malicious code, which, if exploited, can lead to severe security breaches. For example, a popular npm package could have an unnoticed backdoor, putting thousands of applications at risk.
Best Practices for Managing Third-Party Libraries
1. Vet Your Sources
When selecting third-party libraries, it’s crucial to assess their source. Opt for libraries with a strong reputation in the development community. Evaluate the library’s history: review its release frequency, responsiveness to issues, and community engagement in forums or platforms like GitHub.
Check for endorsements from trusted developers or organizations. Additionally, examine the library’s issue tracker for unresolved security issues or frequent bugs and review its maintenance history to ensure it receives regular updates and patches.
2. Stay Updated
Keeping libraries up-to-date is vital for security and functionality. Implement a routine to regularly update libraries to their latest versions, ideally through automated processes.
However, be vigilant with updates: review changelogs for any breaking changes or security patches. Automating updates can streamline the process, but manual review is crucial for ensuring compatibility and understanding the impact of changes.
3. Understand the Code
Incorporating a library with an understanding of its functionality can be safe. Take time to understand the purpose and implementation of the library.
Review the source code to identify any suspicious elements or unnecessary features that could be potential security risks. This approach helps understand how the library interacts with your application and what data it accesses or modifies.
4. Minimize Dependencies
Adopt a minimalistic approach to dependencies. Scrutinize each library to determine if it’s essential. Employ tools to detect and eliminate unused or redundant libraries, reducing the overall attack surface. This practice not only enhances security but also improves application performance and maintainability.
5. Use Dependency Checkers
Leverage tools like OWASP Dependency-Check or Snyk for regular scans of your dependencies. These tools can identify known vulnerabilities in libraries, helping you make informed decisions about their inclusion or updating. Regular scans, as part of your development process, can preemptively address security issues before they become critical.
6. Implement Version Pinning
Specify exact versions of libraries in your project to control updates. This practice prevents automatic updates that might introduce unexpected breaking changes or new vulnerabilities. While this approach requires more manual oversight, it offers greater control and stability for your application.
Safely Implementing a Third-Party Library
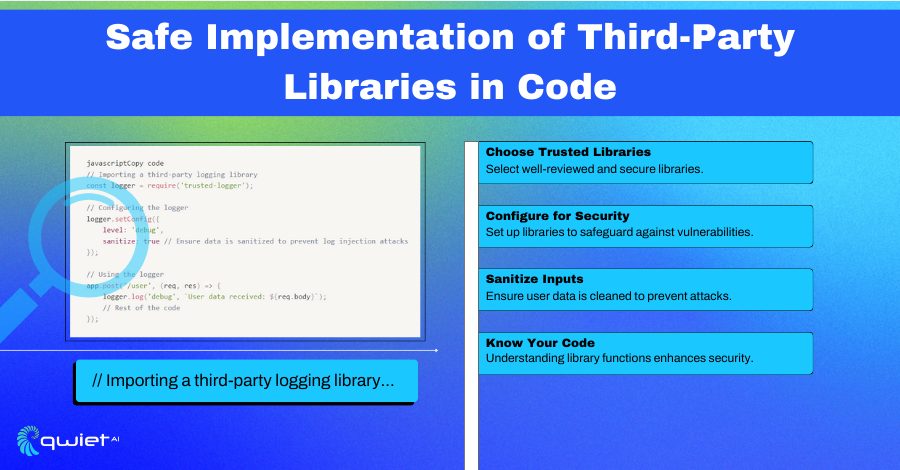
Consider a more detailed scenario of implementing a third-party logging library in a Node.js application. After thorough vetting, the selected library (‘trusted-logger’) is integrated. The configuration is tailored to the application’s needs, ensuring all logged data is sanitized to prevent injection attacks.
This involves setting up appropriate logging levels, data formatting rules, and sanitization processes. The implementation includes rigorous testing to validate the effectiveness of the logging library and its configuration in various scenarios, mainly focusing on security aspects like data handling and error reporting.:
| // Importing a third-party logging library const logger = require(‘trusted-logger’); // Configuring the logger logger.setConfig({ level: ‘debug’, sanitize: true // Ensure data is sanitized to prevent log injection attacks }); // Using the logger app.post(‘/user’, (req, res) => { logger.log(‘debug’, `User data received: ${req.body}`); // Rest of the code }); |
The provided code snippet demonstrates a methodical approach to integrating a third-party library. The ‘trusted-logger’ library is imported and configured with specific parameters to enhance security.
The ‘sanitize’ option in the configuration is critical, as it ensures that all data logged through this library is cleansed of potentially harmful elements, guarding against log injection attacks. This level of detail in configuration showcases a proactive stance in securing applications against sophisticated attack vectors.
Advanced Strategies in Dependency Management
Security Reviews
Implement a structured process for regular security audits of your dependencies. This involves:
- Scheduled Audits: Set up periodic reviews (e.g., quarterly or semi-annually) to evaluate the security posture of all third-party libraries used in your projects.
- Automated Scanning Tools: Utilize automated vulnerability scanning tools to monitor for new threats or weaknesses in your dependencies continuously.
- Manual Code Review: Conduct manual code reviews for critical dependencies to spot potential security issues that automated tools might miss.
- Audit Reporting: Document audit findings and track remediation efforts to ensure vulnerabilities are addressed promptly.
Dependency Isolation
Minimize the risk posed by third-party libraries through isolation strategies:
- Containerization: Use container technologies like Docker to encapsulate third-party code, limiting its interaction with the host system.
- Microservices Architecture: Implement a microservices architecture where third-party libraries are used within isolated services. This reduces the potential impact of a compromised library.
- Restricted Permissions: Assign minimal necessary permissions to the parts of your application using third-party libraries, preventing them from accessing sensitive data or system resources beyond their scope.
Incorporate Dependency Risk Assessment in the Development Cycle
- Risk Assessment Framework: Develop a framework for assessing the risk level of each third-party library before integration. This includes evaluating the library’s security history, update frequency, and potential vulnerabilities’ impact on your application.
- Developer Training: Regularly train your development team to identify and assess third-party libraries’ risks. This can include workshops on the latest security threats, library vulnerabilities, and best practices for secure coding.
- Decision Documentation: Maintain detailed records of the decision-making process for choosing each library, including the assessed risks and justifications. This documentation can be invaluable for future audits and understanding the security posture of your project.
Conclusion
Using third-party libraries in your projects is important for modern software development. However, you should never compromise security. By following these best practices, developers can greatly reduce risks with third-party dependencies. Be alert, keep up to date, and remember that keeping your application safe is an ongoing process, not a one-time task.
Take your dependency management to the next level with Qwiet, which is designed to integrate seamlessly with your development workflow. Book a demo today to see how Qwiet can proactively safeguard your projects against vulnerabilities.
