QWIET AI
AI powered AppSec platform that
your developers will love
AI allows us to quickly and accurately detect vulnerabilities so your dev teams can produce more secure code without increasing production time and tech debt.
Where do the vulnerabilities lie? And what other elements of the app are affected? The Code Property Graph (CPG) shows you by mapping the data flows throughout your entire application and calls out what’s subject to attack.
Accuracy alone is not enough. The preZero platform tells you which vulnerabilities can actually be reached by an attacker, letting you focus your team's effort only on the most critical issues.
Context is key. The risk for an individual vulnerability varies greatly based on its context. Is it reachable? Is it being actively exploited? Qwiet AI's preZero platform helps you put things into perspective so you can prioritize fixes.
We do our scans in your environment, which makes them quicker and provides more accurate detection because it’s using your own configuration and not a mock up in our environment. See how you can start at no cost right now.
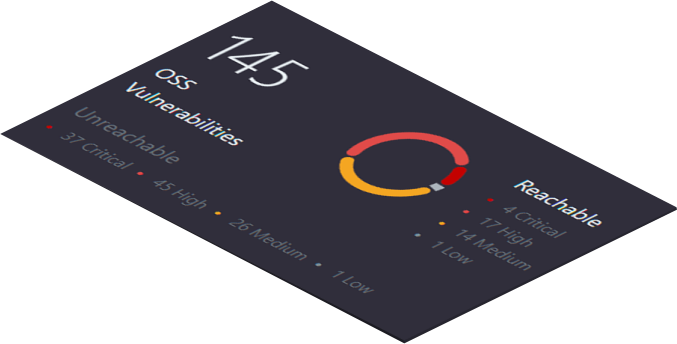
Enhanced vulnerability information helps security become a better partner with the development teams by providing real world insight into the vulnerabilities that are being actively exploited and could potentially lead to a costly post-release patch if not addressed.
Instead of handing down a huge list of issues and saying, “Ok, you need to fix all of these,” you can partner with development to strategically address the issues that have a high probability of being exploited without adding to tech debt.

Engineering leaders want to rapidly release code without worrying about being in the next big attack headlines–think log4j and Kaseya. Enhanced vulnerability information not only provides you with precise information on what security fixes are the highest priority, continual scans can create software bill of materials (SBOM) that highlight what’s being used where–including security insights into containers.
Your reputation, your bottom line, your loyal customers, and your partners, too–all of them are at stake. One breach, hack, or attack can gravely damage the business if a vulnerability in one of the apps gets exploited.
The preZero platform provides that ounce of prevention now versus that ton of costly cure later. By making security a continuous aspect of development rather than an afterthought, the business gains by not losing to the attacks that take others down.

The Code Property Graph turns code into a format that not only makes it machine readable, but also provides a view into the relationships between components and how the data flows through your application.
This provides much richer insight than you can get by just parsing the code with regex, allowing you to spend more time focusing on analyzing and improving code and less time hunting down the information you are looking for.








As a security engineer working with the Dev teams to implement SDLC and Code security standards and compliance, deploying the ShiftLeft for static code testing was a great experience. I enjoyed working with the experts from the ShiftLeft team
We are able to scan our apps more often with the platform because its fast enough to fit into our SDLC process.
Significant realization of operational goals to reduce time of issue discovery to resolution, allowing the app dev teams to stay focused on the production and delivery of high business value products and services versus the older cultural approach of… hunting large quantities of bugs and flaws as the KPI measuring success.
Key Findings The SAIL (Secure AI Lifecycle) Framework outlines AI-specific risks across the lifecycle, but lacks implementation details. Qwiet AI fills this gap with direct, technical controls focused on code and configuration-level vulnerabilities. Qwiet AI aligns with SAIL Phases 2 and 3 by identifying hidden AI assets, detecting hardcoded secrets, auditing third-party AI components, and […]
Key Takeaways Claiming that AI alone is not sufficient proof is one thing; real value comes from demonstrating how AI actually functions, not merely stating that it exists. AI-washing erodes trust. Vague claims or superficial integrations damage credibility across the AppSec space. Agentic, transparent systems win. Teams should look for tools that integrate AI deeply, […]
Key Takeaways Impact: CVE-2025-20281 (CVSS 10.0) lets an unauthenticated attacker send a single API request and gain root-level access, all without credentials or user interaction. Cause: The root cause of the vulnerability is insufficient input validation, confirming yet again that validation logic is still inadequate in many popular services. Fix: Defenders should implement fixes ASAP […]
Key Takeaways Shift left overburdened developers without giving them the right tools or support. The intention was solid, but the execution often left devs overwhelmed and security goals unmet. Shifting to the middle means shared responsibility, not shifted burden. With security integrated contextually into dev workflows, both speed and protection improve. Developer-security collaboration thrives when […]