Introduction
Directory Traversal Attacks: they’re like the pickpockets of the web, sneaking around your server’s file system, looking for something valuable to snatch. But don’t worry; we’ve got the tools and techniques to catch these digital thieves red-handed. So, let’s get into the nitty-gritty of securing your file handling operations and making your server a no-go zone for directory traversal mischief.
What is a Directory Traversal Attack?
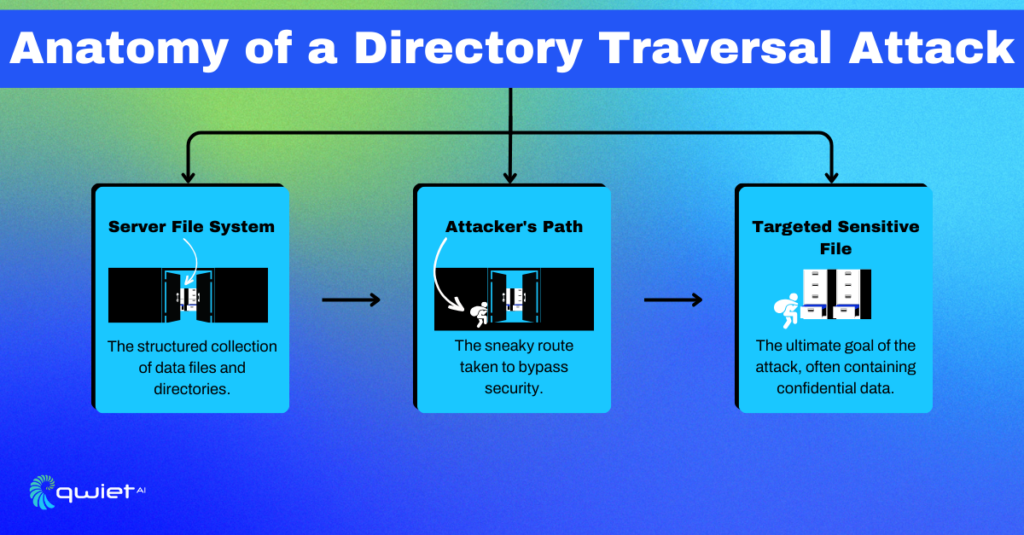
In a Directory Traversal Attack, an attacker manipulates file paths in a way that allows them to access files and directories that should be restricted. Imagine someone trying to sneak backstage at a concert by finding a hidden path; only, in this case, the backstage holds sensitive data and system files.
The Fundamentals: Understanding File Paths
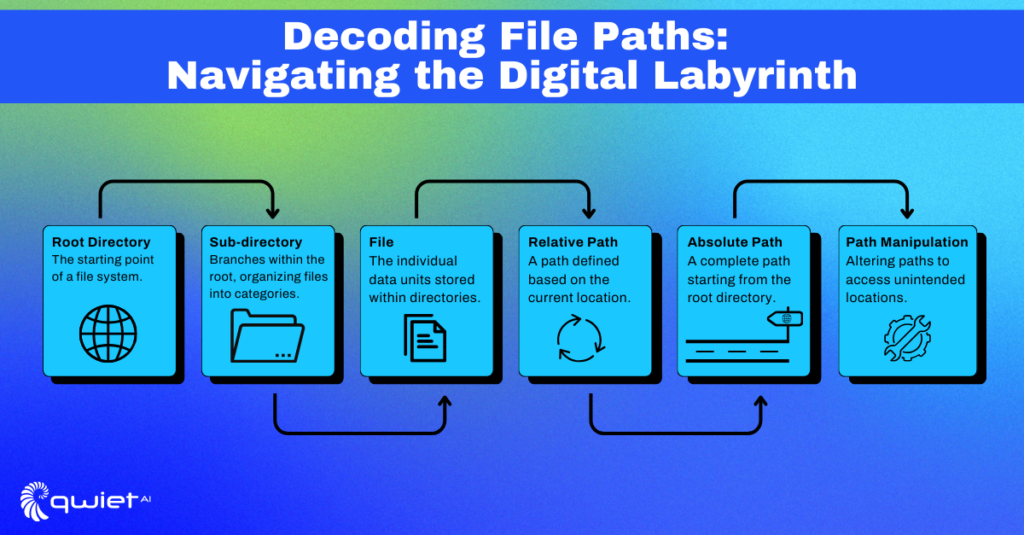
Before we dive into the solutions, let’s get the basics right. Understanding how file paths work is crucial for securing them. A file path like ../../etc/passwd can be a red flag, signaling an attempt to move up directories to access sensitive files.
Code Snippet: Basic File Path Handling in Python
| import os # User-provided file name user_file_name = input(“Enter the file name: “) # Construct the full file path full_file_path = os.path.join(“/app/data/”, user_file_name) # Open the file with open(full_file_path, “r”) as file: content = file.read() |
In this Python snippet, we’re using os.path.join to construct a file path. The user provides a file name, which is then appended to the /app/data/ directory. This is a basic example and not secure as-is, because a crafty user could input something like ../../etc/passwd to access restricted files.
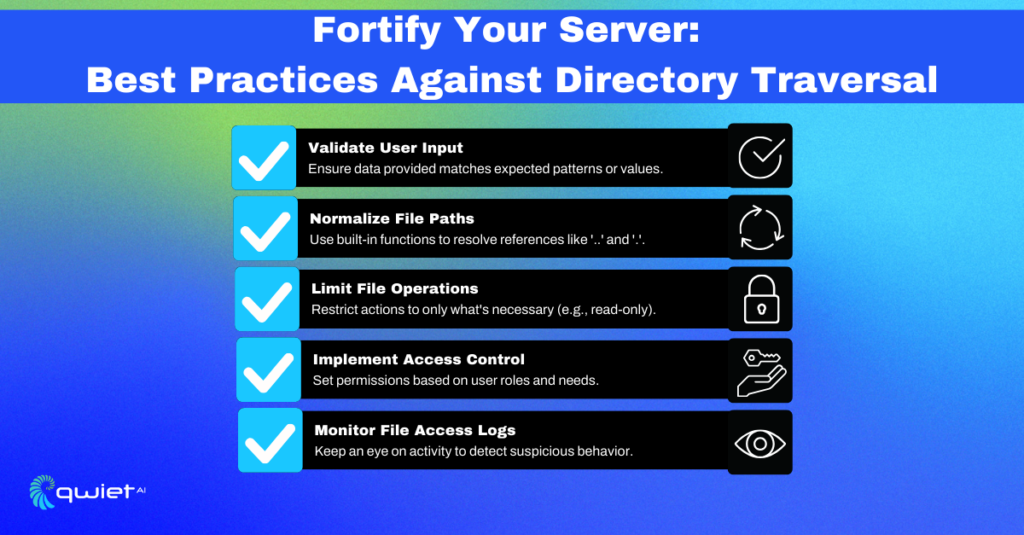
Best Practices for Secure File Handling
Validate User Input
The first line of defense is always validating what the user has provided. Make sure the input matches a certain pattern or set of allowed values.
| import re # Validate user input if not re.match(“^[a-zA-Z0-9_]*$”, user_file_name): print(“Invalid file name!”) |
We’re using Python’s re module to check if the user-provided file name contains only alphanumeric characters and underscores. If it doesn’t, we flag it as invalid.
Use Built-in Functions for Path Normalization
Many programming languages offer built-in functions to normalize file paths, effectively resolving “..” and “.” references.
| # Normalize the file path normalized_path = os.path.normpath(os.path.join(“/app/data/”, user_file_name)) # Check if the normalized path is within the allowed directory if normalized_path.startswith(“/app/data/”): with open(normalized_path, “r”) as file: content = file.read() else: print(“Access denied!”) |
In this Python example, os.path.normpath is used to normalize the file path. We then check if the normalized path starts with the allowed directory /app/data/. If it does, access is allowed.
Limit File Operations
Restrict the types of operations that can be performed. If a feature only requires reading files, there should be no option to delete or modify them.
| # Only allow read operations if operation not in [“read”]: print(“Operation not allowed!”) |
We’re explicitly checking if the operation is “read” before proceeding. Any other operation is flagged as not allowed.
Advanced Techniques
Implement Access Control
Access control mechanisms can be implemented at the application level to ensure only authorized users can access certain files.
| # Example: Role-based access control if user_role != “admin”: print(“You do not have permission to access this file.”) |
In this snippet, we’re checking the user’s role before allowing access to a file. Only users with an “admin” role are granted access.
Logging and Monitoring
Keep an eye on file access logs to detect any suspicious activity.
| import logging logging.basicConfig(level=logging.INFO) logging.info(f“User {user_id} accessed file {normalized_path}”) |
Here, we’re using Python’s logging module to log file access, including the user ID and the file path. This can help in auditing and identifying suspicious behavior.
Conclusion
Directory Traversal Attacks are deceptive but can be countered with the right strategies and tools. To bolster your defenses and ensure against directory traversal attacks, it’s essential to stay vigilant and consistent in your security protocols. Want to see how a tool like Qwiet can help you secure your security posture? Book a demo with us today.