Why does software security matter?
From the rise of the internet to an entirely interconnected world
The last 30 years have seen remarkable developments in computer technology and the emergence of the internet. It’s incredible to think about how much more connected and pervasive the internet has become since the turn of the century. Nowadays, all activities on the planet are related, in one way or another, to the web.
Early in its history, computer science was seen as something only hardcore geeks would be interested in. Nonetheless, much work has been done to get it out there and make its virtues available to everyone. Companies like Microsoft have opened our eyes to the possibilities of these hitherto enigmatic developments. Apple’s invention of the iPhone, which allows anyone, from the youngest to the oldest, to access the global web with the slide of a finger, was the most crucial step toward adoption (C. Wong, A. Stearn, D. Schleen 2018. Epic Failures in Devsecops). As a result, the software’s importance has reached new heights. Indeed, the software connects the user to the machine; it is the cornerstone of the information era we live in.
Undoubtedly, the rise of the internet thanks to software has brought humanity plenty of progress. But with benefits also come threats. The internet has made previously inaccessible resources, such as private communications and critical information, available to everyone on the planet for the first time in mankind’s history.
On the importance of security
Safety checking is at the heart of the design process in many domains. Car manufacturers, for instance, incorporate safety into the design. You don’t wonder if the security has been assessed when you buy a car as safety features are one of the benchmarks of a car’s quality. Furthermore, drivers are trained to follow the rules of the road, ensuring their and others’ safety.
The software industry is of course concerned with security. Most major organizations and governments recognize its vital role. However, flaws are frequently discovered, and too many businesses and governments continue to face high-cost data leaks and cyberattacks.
“There is a pressing need to implement more rigorous and predictable mechanisms for ensuring that products function securely, and as intended.”
Executive order on improving the Nation’s Cybersecurity.
U.S. President Joe Biden
User errors account for a sizable portion of vulnerabilities, but developers and software designers must nonetheless deliver safe and robust products. Indeed, malicious hackers exploiting a vulnerability can have disastrous consequences for businesses, organizations, or governments. Millions of computers might be compromised if an exploitable weakness in a critical system is ever used (Votipka et al., 2018). The stakes for security are incredibly high when we consider the importance of the computer and software industries in our global economy.
Despite the threats and the widespread knowledge of the benefits of a rigorous approach to implementing security methods, this priority is often overlooked. The prevalence, scope, and seriousness of attacks exploiting software flaws are all on the rise (Yuan et al., 2022). The lack of security stems from the technological and budgetary challenges associated with assuring the security of big software programs. Ensuring program security takes effort, expertise, and resources, most of the time for intangible and unpriced aspects of software products. Due to time constraints and factors mentioned above, vulnerability testing is typically performed after the core features of a program have been developed.
Addressing security at the end of the process or not frequently enough during software development is by no means the optimal solution. The repercussions of discovering a vulnerability can be disastrous for a business. It is highly probable that fixing particular vulnerabilities will necessitate a radical rethinking of the software’s architecture, which would delay the product’s release indefinitely and lead to dire and unforeseen consequences. Thus, the importance of safety cannot be overstated.
Moreover, the number of people who regularly use the internet and other forms of software continues to rise, and all of these users must be given the protections they need.
The proper course of action is to make security a primary design consideration. Naturally, there are current development frameworks and approaches available to do this.
How to handle software security?
Integrate security in the software development cycle.
In the early days of software development, security was addressed at the end of the process, if at all. The problem was that if the detected vulnerabilities required extensive modifications to the source code, it could take a long time and cost a lot of money, putting small businesses at risk of bankruptcy. The solution is to implement the “DevSecOps” development practice.
DevSecOps refers to incorporating security considerations at every stage of the software development cycle, from the architecture design to the deployment and operation.
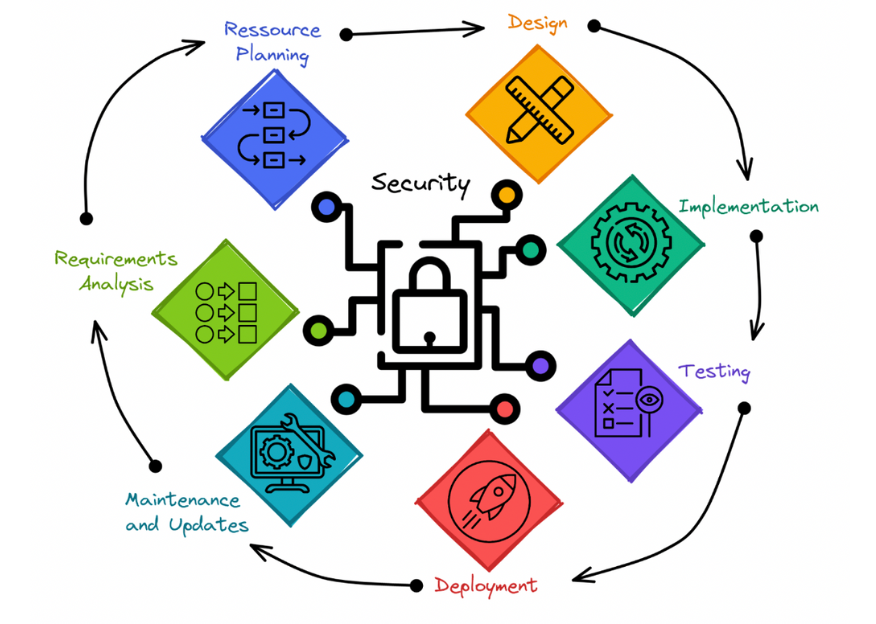
Security-centered software development cycle – Security should be prioritized throughout the development process. It should be seen as the common denominator of all development stages.
Even with a solid and robust design, mistakes and unanticipated weaknesses can occur as a project grows. That is why it is critical to scan and review the code regularly. Thus, developers need support tools that make their work easier and encourage them to evaluate the code’s security thoroughly.
ShiftLeft provides such tools thanks to a revolutionary technology in static code analysis: the Code Property Graph (CPG).
The main force of CPG is to transform source code into a queryable data set. ShiftLeft CORE, powered by CPG, allows representing code entities by nodes (e.g., a function or a variable) and entities interaction by edges (i.e., linking arguments to function or conditions needed to reach a statement). The basic example in the figure below illustrates the notion of converting a piece of code to a graph.
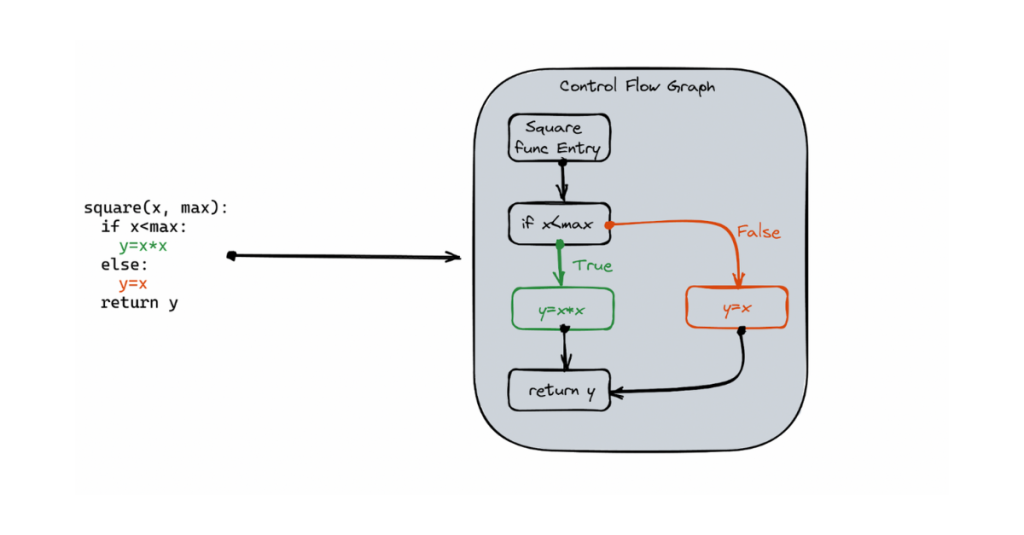
A basic example of a Control Flow Graph (CFG) – CFG is one of three graphs that constitute a Code Property Graph (CPG). Edges represent the paths taken by the program, while nodes stand in for the statements and predicates. The other two Graphs are the Abstract Syntax Tree (AST) and the Program Dependence Graph (PDG). See F. Yamagushi et al., 2014 for details.
CPG reaches its full potential when used on large source code. This technology, associated with graph traversal algorithms, is exceptionally efficient in detecting dependencies, identifying control flow, and data life cycle through a program only by performing static analysis.
Using specific requests on the graph database representing the source code makes it possible to detect vulnerabilities in the source code and its dependencies. Even more relevant, ShifLeft CORE functionalities allow identifying, describing, categorizing, and prioritizing vulnerabilities, which make the fixing easier. The objective is not to be finicky and flawless; rather, the output must be rapid while remaining free of critical flaws. In the past year, ShifLeft identified 97% of discovered vulnerabilities as false positives, which allows teams to focus on the 3% of high-priority vulnerabilities. At the same time, the Mean Time To Remediate (MTTR) is, thanks to precise identification and location of threats, of only 12 days on average. Teams who have used DevSecOps diligently from the beginning of a project can reduce their MTTR even more.
Secure code at scale
The icing on the cake, as CPG representation of source codes is stored as a graph database, the query speed does not slow with the size of the graph. One reason is that there is no need to compute relationships on querying because they are directly stored in the graph. Consequently, the efficiency of graph databases and ShifLeft technology made it possible to scan source code quickly and at scale. In 2022, ShiftLeft customers performed, on average, one scan of their entire source code a day for a 1 minute 30 seconds scan duration.

Most common vulnerabilities – The vulnerabilities discovered are frequently of the same type. Here are the 15 most frequent vulnerabilities discovered by ShiftLeft in 2021 and 2022. See the guide to the OWASP top 10 for more information about vulnerabilities.
It is the mission of ShiftLeft to assist businesses in enhancing the level of application security they possess by testing applications as a whole along with their dependencies in an efficient manner so as not to impede the development process. ShiftLeft frequently identifies vulnerabilities of the same type. The table above summarizes the most frequent vulnerabilities discovered in the previous two years. Because the same vulnerabilities are frequently encountered, it enables for the development of more efficient fixing procedures that can lower the MTTR.
As we have seen previously, early consideration of security is required. Shifting left entails correcting requirements in advance rather than discovering problems later. Of course, more than code scanning is required to ensure the safety of a program. Architecture, for example, is also extremely important. Ideas as fundamental as “defense in depth” can be stated explicitly: While no security system is foolproof, Defense in Depth is based on the simple idea that more barriers make it more challenging for an attacker to overcome them (C. Wong, A. Stearn, D. Schleen 2018. Epic Failures in Devsecops).
Overall, a secure application results from a conglomeration of good development and teamwork practices; it will resist attacks and have no vulnerabilities due to dependencies; it will be built and maintained by a team that can respond quickly to fixes and changes in security paradigms. There is no other way to efficiently design robust software that can scale to mass adoption but to embrace security.The best investment a software company can make is in establishing a proper security-driven workflow. The goal of ShiftLeft is to make this journey easier.