Safe exception handling is an indispensable ally for developers venturing into the depths of robust application development. A seamlessly functioning application enhances user experience and safeguards sensitive data during untoward incidents, such as errors and exceptions. Let’s unveil the stratagems to ace safe exception handling without spilling the informational beans to the outside world.
Understanding Exception Handling
Exception handling acts like the safety net of your application, preventing it from crashing and providing diagnostic insights during unforeseen errors. While these insights (like stack traces or debug information) are crucial for developers, they can inadvertently leak sensitive information if exposed to users or external entities.
| try { // Potentially erring code } catch (error) { console.error(error); // Caution: Exposing sensitive data } |
In the example above, revealing complete error objects in a production environment can equip malicious actors with critical information, escalating to security vulnerabilities.
Crafting a Robust Exception Handling Mechanism
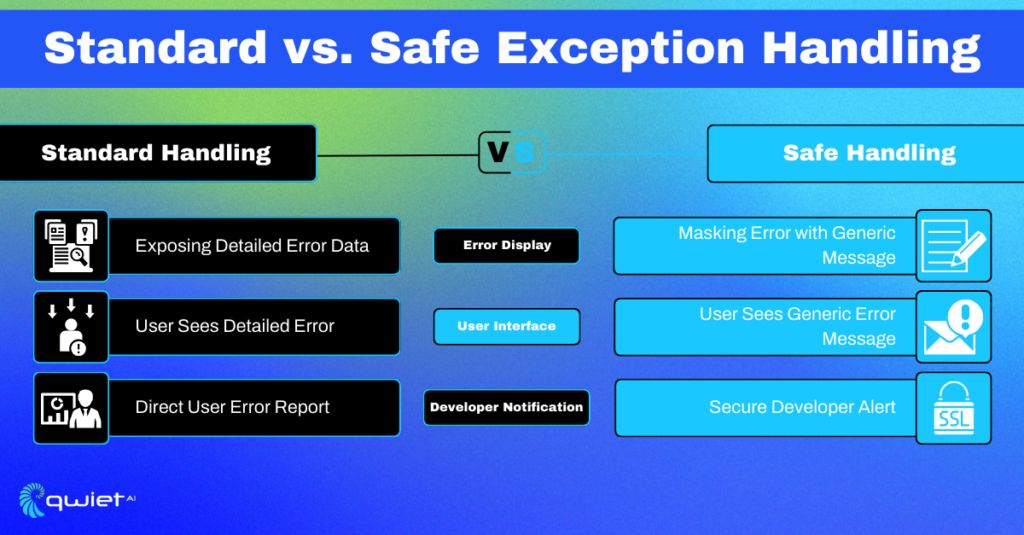
1. Masking Information with Generic Messages:
While the intrinsic details of an error are invaluable during debugging, exposing them to users or logs can be risky. Adopt a practice of showing generic error messages to the users while securely logging the detailed error information server-side for further analysis.
| try { // Code that might trigger an exception } catch (error) { console.error(error); // Log detailed error internally alert(‘An unexpected error occurred.’); // Show generic message to user } |
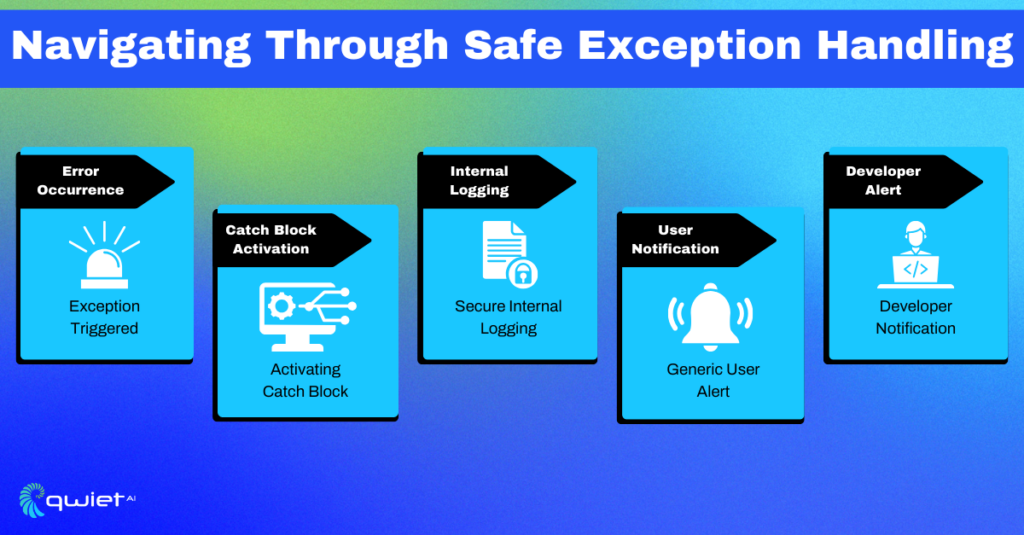
2. Implementing Centralized Exception Handling:
A centralized exception-handling mechanism acts as a singular catchment area for all errors, ensuring exceptions are dealt with uniformly, adhering to a consistent error-handling protocol.
| function globalErrorHandler(error, origin) { // Log error details internally // Display generic error message to user // Optionally, alert the development team } window.onerror = globalErrorHandler; // Assign global error handler |
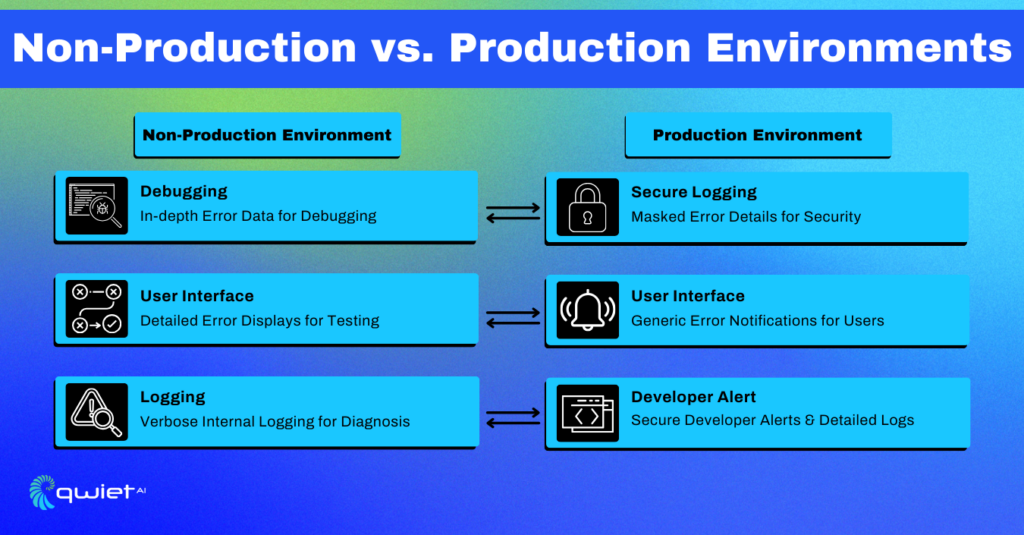
3. Thoughtful Logging:
Ensuring that logs do not disclose insightful error details, especially in a production environment, restricts valuable information from becoming accessible to potential attackers.
| try { // Potentially problematic code } catch (error) { if (process.env.NODE_ENV === ‘production’) { // Log only generic message in production logs console.error(‘An error occurred.’); } else { // Detailed logging for non-production environments console.error(error); } } |
Best Practices and Advanced Protective Measures
1. Establishing a Detailed Logging Strategy:
A comprehensive logging strategy is vital for diagnosing and resolving issues without compromising application security. This approach captures detailed error data internally while presenting only general, non-sensitive messages to end users. Internal logs should include error types, stack traces, and contextual information to facilitate root cause analysis. These logs are critical for developers to trace and understand the origins and implications of the errors.
On the user side, displaying detailed logs can pose security risks. Therefore, user-facing error messages should be generic, providing necessary information without exposing sensitive data. This protects the application and ensures that users are informed about issues without being overwhelmed with technical details.
2. Employing Monitoring and Alerting Systems:
Effective exception handling requires proactive monitoring and alerting systems. These systems continuously watch for errors and anomalies, providing real-time insights into the application’s health.
By setting up alerts for unusual or repetitive error patterns, developers can be immediately notified of issues, allowing for swift resolution. This proactive approach not only minimizes downtime but also helps in identifying potential security threats.
Incorporating comprehensive monitoring tools that track various aspects of the application, from server performance to user interactions, can offer a holistic view of the application’s health. Integrating these systems with incident management tools ensures that any detected issues are promptly addressed.
3. Regular Audits and Simulations:
Conducting periodic audits of the exception-handling mechanisms ensures they remain effective and secure. These audits involve reviewing and testing the entire error-handling process, from detection to resolution, and identifying areas for improvement.
Employing chaos engineering principles, where errors and failures are intentionally simulated, tests the resilience and robustness of the exception-handling system. This proactive approach helps uncover hidden vulnerabilities and ensure the system’s preparedness for real-world scenarios.
In conjunction with chaos engineering techniques, regular simulations, and drills can also help train the development and operational teams to respond effectively to unexpected errors and outages.
This practice not only refines the error-handling process but also fosters a culture of continuous learning and improvement, ensuring that the application remains resilient and secure against evolving threats and challenges.
Conclusion
With safe exception handling firmly ingrained, it safeguards your application and its sensitive data from unwanted exposures. By masking informational insights from users and external interfaces, centralizing error handling, and implementing a secure logging strategy, developers armor their applications against many potential threats. With consistent audits, advanced monitoring, and adopting best practices, let’s elevate our applications into fortresses, unyielding to informational exposures and security threats.
To help catch these types of information leakages, having a tool like Qwiet can help catch these early in the development process. To learn more, book a demo with our team today.