Introduction
Remote Code Execution (RCE) is a term every web developer should be intimately familiar with. It’s the dark cloud that could spell disaster for your meticulously crafted application. An RCE attack can lead to unauthorized access and manipulation of your application, giving attackers the leverage to exploit your system’s vulnerabilities. Let’s dive into the intricacies of RCE attacks and explore robust strategies to fortify your web applications against them.
Understanding Remote Code Execution
Remote Code Execution (RCE) is a prevalent security vulnerability that every developer must comprehend to secure web applications effectively. It occurs when an attacker identifies a vulnerability within an application, enabling them to execute arbitrary code on the server where the application resides.
For example, look at the code below:
| eval(req.body.code); |
In this code, the function eval() takes user input and executes it. This is problematic because it opens a gateway for attackers to execute harmful code, giving them the potential to access, steal, or manipulate sensitive data, and even control over the server’s functionality.
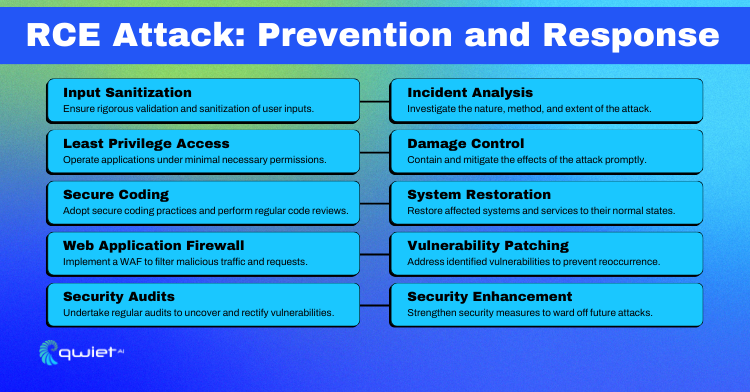
Fortification Strategies against RCE Attacks
Input Validation and Sanitization:
Input validation and sanitization are fundamental to web application security. These processes involve scrutinizing and cleaning user input to prevent malicious or erroneous data from entering the application, which could lead to various security vulnerabilities, including RCE.
Here’s an example of how to do it:
| const userInput = req.body.code; if (!isValidInput(userInput)) { throw new Error(‘Invalid input!’); } |
This example illustrates a safeguard where user input is examined against specified criteria to ensure it’s safe and valid before the application processes it. By doing so, it reduces the likelihood of harmful data slipping through, which could lead to malicious code being executed within the application.
Least Privilege Principle:
The Least Privilege Principle is a security concept where a user or process is given the minimum levels of access or permissions required to perform its function, and no more.
| const secureExec = require(‘secure-exec’); secureExec(‘command’, { uid: ‘limitedUser’ }); |
This concept helps contain the potential damage from an RCE attack. Even if an attacker gains access, the limited permissions can prevent them from executing harmful commands or accessing sensitive areas of the application or system.
Secure Code Practices:
Secure code practices involve continuously reviewing and updating code to patch vulnerabilities, adopting coding practices that prioritize security, and staying updated with the latest security trends and threats.
Here is a practice to keep your code’s dependencies updated:
| const updater = require(‘dependency-updater’); updater.checkForUpdates(); |
By ensuring that an application’s dependencies are current, you help in protecting it against known vulnerabilities, enhancing its defense against potential threats, and making sure that the application operates securely and effectively.
Enhanced Security Measures
Web Application Firewall (WAF):
Implementing a Web Application Firewall (WAF) is a crucial strategy in enhancing the security of a web application. A WAF helps protect web applications by monitoring and filtering the incoming traffic between a web application and the Internet.
It identifies and blocks any malicious traffic, ensuring that unwanted and potentially harmful requests are prevented from reaching the application. The WAF works by establishing a set of rules known as policies, to identify and manage suspicious activities.
These policies are designed to recognize common attack patterns, such as SQL injection and Cross-Site Scripting (XSS), allowing the WAF to stop attacks before they reach the web application, adding a robust layer of security.
Regular Security Audits:
Conducting regular security audits is another essential aspect of maintaining a secure web application. A security audit involves a systematic evaluation of the application’s security, aiming to identify any vulnerabilities or weaknesses that might be exploited by attackers.
Security audits help in understanding the effectiveness of the existing security measures and strategies, allowing for the identification and rectification of vulnerabilities, and ensuring the application’s defenses are always up-to-date and capable of thwarting potential attacks.
Regular audits facilitate the continuous improvement and adaptation of the application’s security posture in response to emerging threats and vulnerabilities.
Monitoring and Alerting:
A vital component of safeguarding applications is the continuous scrutiny of their operation, known as monitoring. This process diligently observes the application, pinpointing unusual or suspicious activities, and proactively identifying potential threats.
The alerting process complements monitoring by acting as a vigilant communicator. When a risk is spotted, the alerting system swiftly notifies the appropriate personnel, ensuring that rapid and effective actions are taken to neutralize threats. It works seamlessly, ensuring that the integrity of the application is maintained and that security protocols are upheld promptly and efficiently.
This combination of monitoring and alerting constructs a resilient defense, keeping applications secure and operational.
Conclusion
Remote Code Execution (RCE) attacks are a big threat to web applications, capable of causing a lot of damage. But there are strong security practices that can protect your application against these attacks. Implementing solid security steps like careful input validation, using secure coding practices, and performing regular security checks are essential. These actions build up the defenses of your application, making it resilient against attacks. Interested in strengthening your application’s security? Schedule a call with our team today to secure your applications security posture.