Avoid supply chain risk
SBOM
Understanding what's in your code
Our SAST scanner provides a comprehensive Software Bill of Materials (SBOM) showing every component of your software inventory–not only open source libraries, but also proprietary code. By identifying all dependencies and potential vulnerabilities, Qwiet AI empowers you to secure your applications against emerging threats.
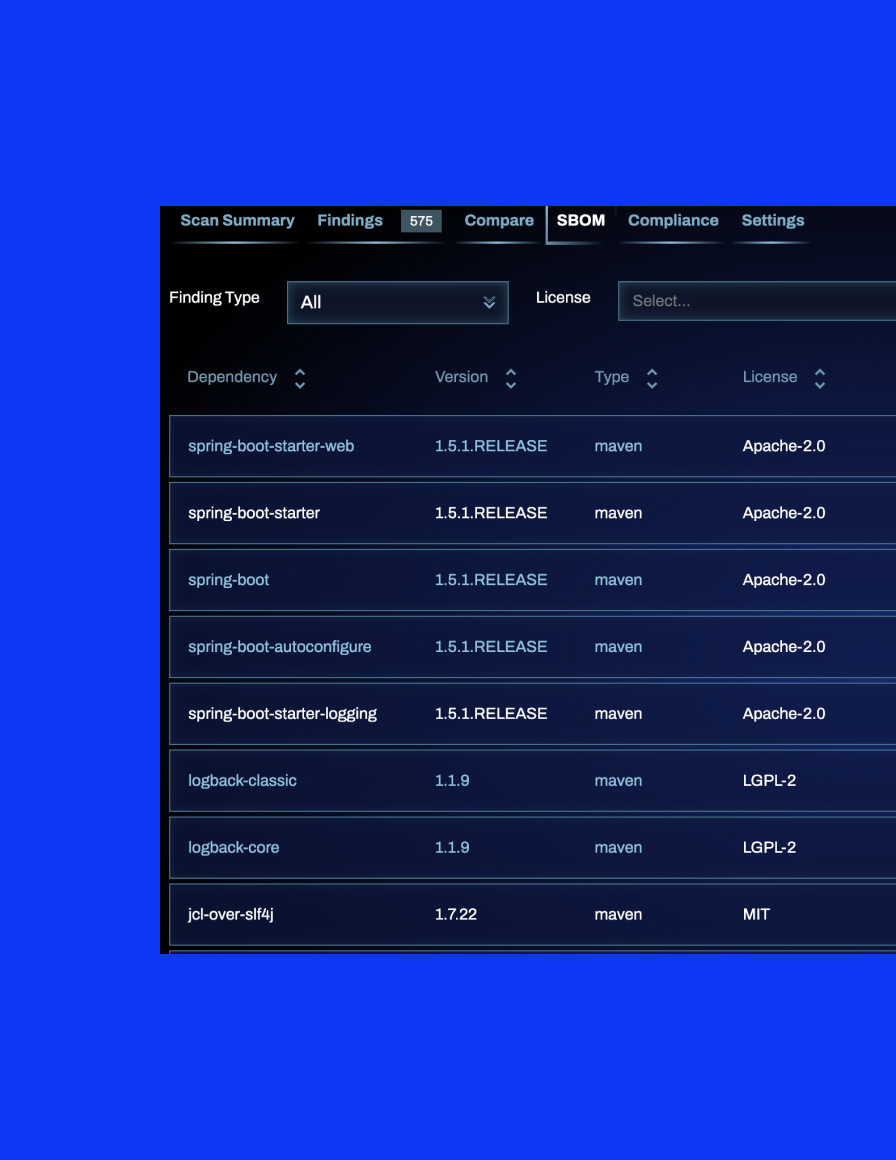
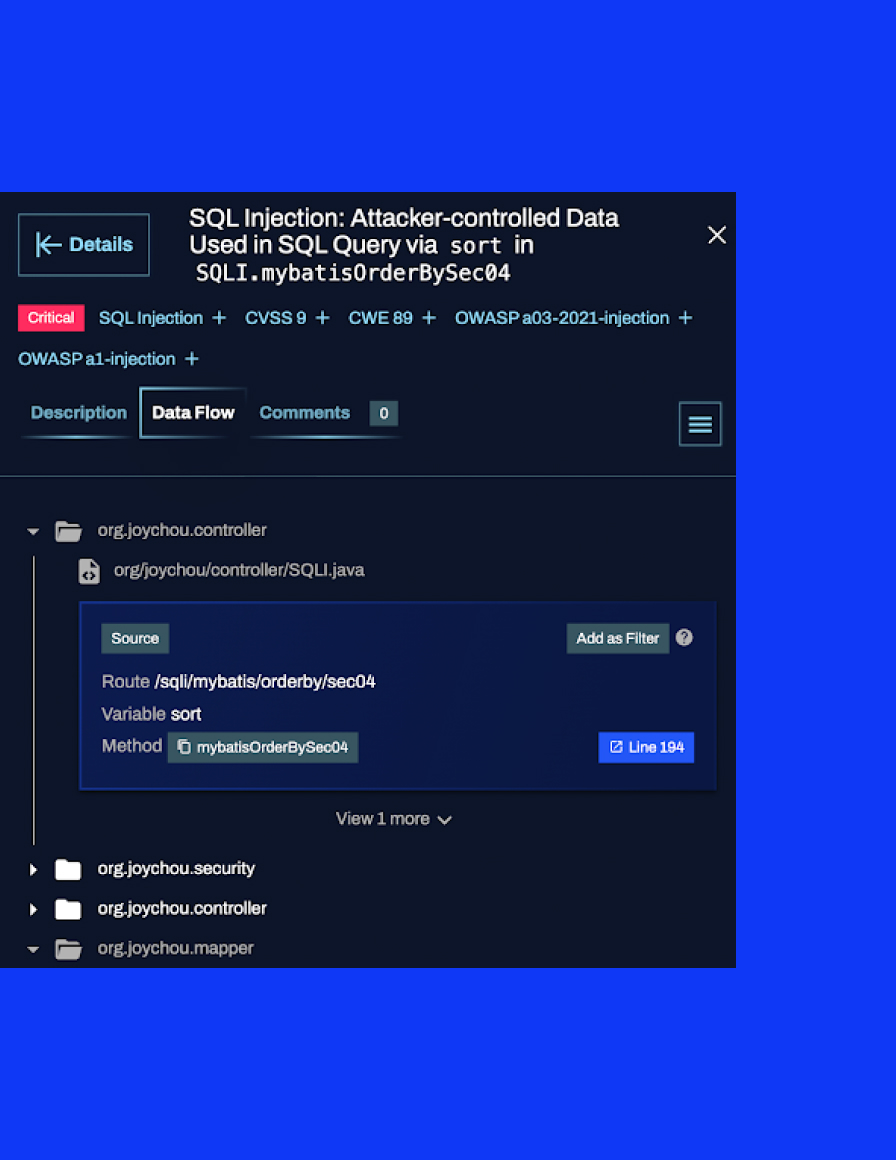
Detailed security information
Click on any reported package to see an in-depth explanation of related security issues in the SBOM, along with recommendations from Qwiet AI for mitigating security risk.
Criticality and reachability
When reviewing the SBOM, preZero uses AI scans of the Code Property Graph (CPG) to tell you if a package is even reachable by an attacker. This helps you prioritize issues and determine acceptable risk levels.
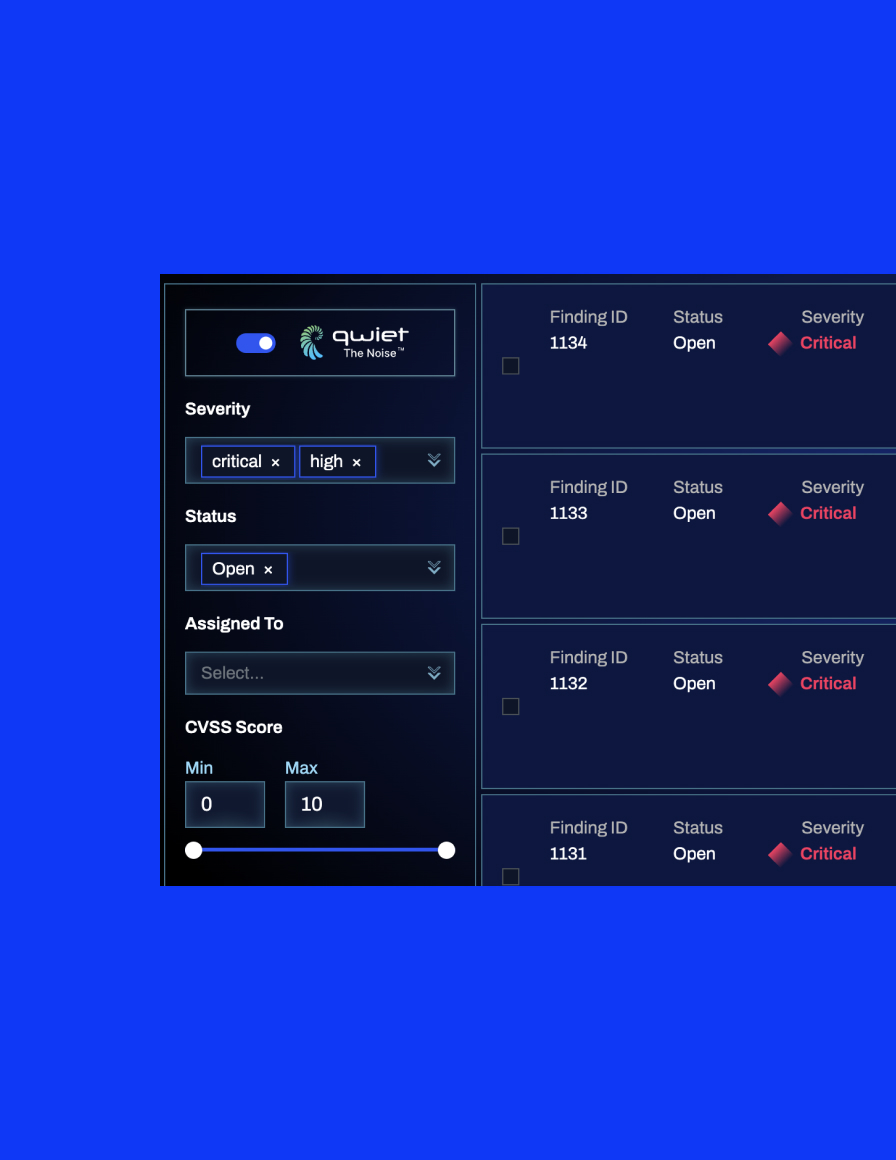
Find out what's really in your supply chain
Security pros have understood the importance of SBOMs for years: they help you know what’s really in your apps, which is essential for effective vulnerability management—as we saw with log4j, Kaseya, and Solarwinds, to name a few prominent examples. Executive Order (E.O.) 14028 has suggested that SBOMs be a requirement for applications used by the US Federal government, making them extremely important.
The combination of our patented Code Property Graph and proprietary AI allow us to compile SBOMs with unparalleled accuracy, enabling you to improve your AppSec posture both proactively and reactively.