Introduction
DevSecOps isn’t broken, but under stress as AI-generated code accelerates delivery. It’s also injecting complexity and risk into development pipelines, often without clear visibility. Developers are now expected to integrate security scanning into CI/CD, interpret ambiguous findings, and deliver clean code at machine speed. In this article, you will learn where traditional DevSecOps workflows are falling short, how modern threats require context-aware security practices, and which technical strategies, like reachability analysis and intelligent triage, can help teams catch up.
The Real Developer Pain Velocity Without Visibility
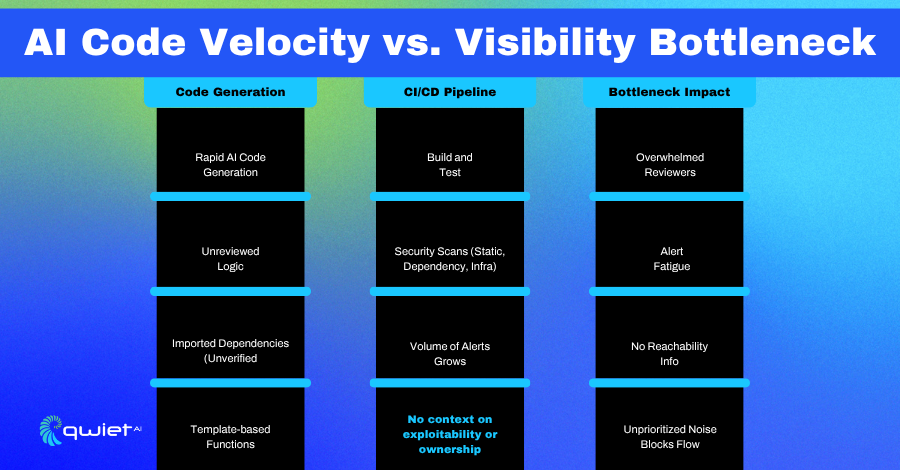
Code Volume Outpaces Review Capacity
AI tooling has made it easier to generate code, but that increase in output doesn’t come with a matching increase in oversight. While suggestions from tools like Copilot can be helpful, they’re not vetted for context or security. Developers are moving faster, but also inheriting logic and dependencies that weren’t carefully reviewed. This includes insecure patterns, outdated APIs, and third-party libraries pulled in without proper scrutiny.
The volume of code entering repositories, especially in teams adopting generative tools, makes it unrealistic to review everything manually. Most of it gets merged based on passing tests, not security guarantees. Even well-meaning teams end up with code paths no one fully understands. And if something breaks or exposes data, it’s often unclear how the issue managed to slip through review in the first place.
What’s missing is a clear line of sight into what’s being added, how it connects to the rest of the system, and whether it introduces new risks. Code might appear fine, but pulling in libraries with known CVEs, deprecated functions, or unsafe behaviors that trigger under specific conditions is a concern.
Signal Buried Under Scanning Noise
Once that unvetted code hits CI, it triggers scanners SAST, DAST, dependency checks, and more. The result is often dozens of findings per pull request, many missing context. Security tools may surface issues in unreachable paths, flag low-severity findings that the team has already accepted, or detect deprecated libraries used in non-exploitable ways.
This overload slows developers down. Most teams don’t have time to parse every alert, and without a clear path to exploit or a stack trace, it’s hard to know what should be fixed versus what can wait. Even worse, real risks can get lost among the noise, primarily when every PR generates a flood of alerts.
Reviewers are left trying to make sense of raw outputs. They lack the tools to trace how an input might move through nested functions or determine whether a flagged vulnerability is reachable from user-controlled data. Without that depth, even experienced teams rely on guesswork, which undermines trust in the entire scanning pipeline.
Tool Sprawl Without Context Is DevSecOps Noise
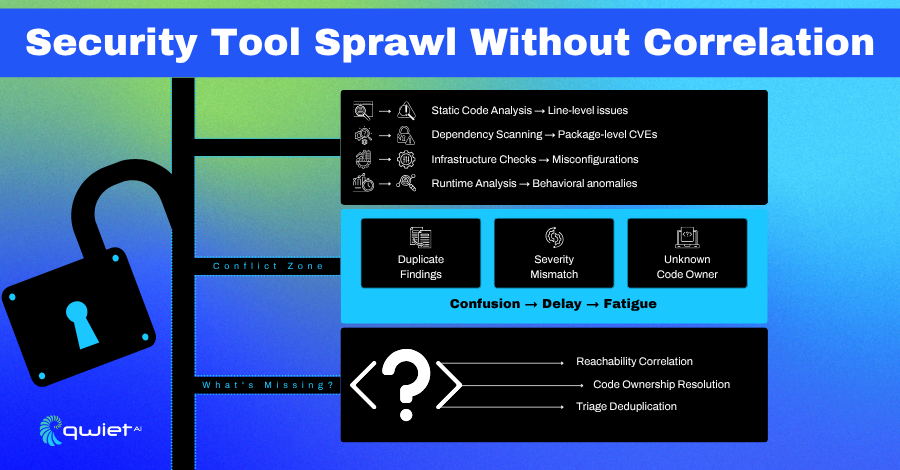
Too Many Scanners, Not Enough Alignment
Today’s security stacks often include multiple scanners running in parallel: SCA for dependencies, SAST for code, DAST for runtime, and IaC checks for cloud configuration. These tools each have their strengths, but without a coordination layer, they operate in silos.
One might flag a library vulnerability, another a code pattern, and another a misconfigured secret. The alerts land in different dashboards or PRs, and there is no clear way to connect the dots.
For developers, it’s not just noise, it’s fragmentation. You might see the same issue flagged twice from different angles, or get five separate alerts that all trace back to the exact root cause.
Fix instructions are often generic or missing. And without metadata like runtime path, exploitability, or code ownership, you’re stuck figuring out whether the finding matters or who should deal with it.
Context Is the Missing Layer
Reachability analysis through tools like Code Property Graphs (CPG) changes the game. Instead of dumping a list of all possible issues, you get a filtered view of what’s reachable from entry points and user input.
That helps teams focus on what’s exploitable instead of treating every finding equally. When those insights are layered with Git blame data, ownership becomes clear, and alerts can be directed directly to the person who last modified the vulnerable file or method.
Correlation and deduplication also matter. Teams waste time triaging the same problem multiple times across tools without them. A coordinated system that consolidates alerts, filters by exploitability, and maps findings back to responsible teams doesn’t just cut noise; it makes the alerts actionable. Without that context, it’s easy to miss real risk or waste cycles on issues that don’t affect your runtime. Developers need fewer tools and more innovative outputs.
Scaling Secure Code – From Pipeline Chaos to Prioritized Action
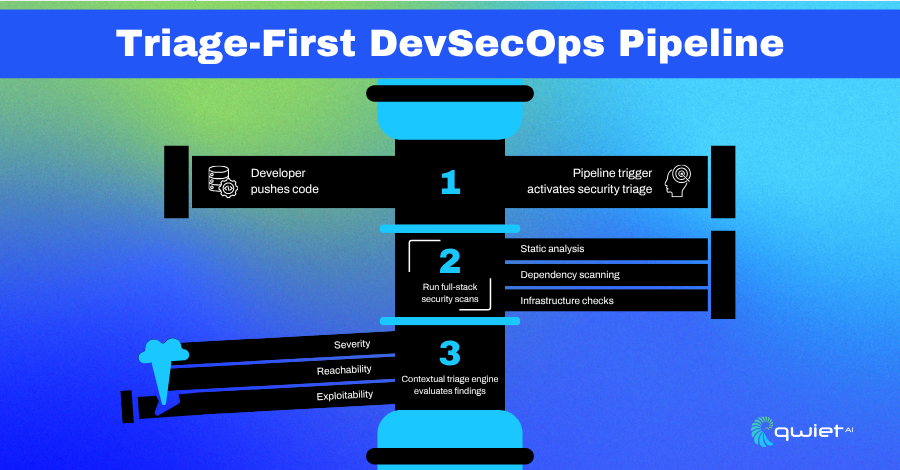
Build a Triage-Driven Security Workflow
Shifting DevSecOps left isn’t enough unless you control the signal. Modern pipelines require a triage-first model that ranks vulnerabilities based on their behavior within your codebase, rather than just their appearance on a CVE list. Start by automating classification using reachability analysis, exploitability assessment, and context from your repo.
- Integrate Code Property Graph (CPG) analysis to determine whether a vulnerability has a valid path from input to sink (e.g., user-controlled input reaching a vulnerable function).
- Map findings to their Git history using git blame or commit metadata to tag responsible authors or teams.
- Score vulnerabilities using runtime context, considering how data flows, control paths, and function usage patterns influence exploitability, not just static severity.
This filters out noise from alerts that aren’t reachable or relevant, ensuring developers only see what they’re in a position to fix.
Automate Contextual Blocking Inside CI/CD Pipelines
Enforcing secure code without creating PR gridlock means blocking with precision. Context-aware validation can be integrated directly into your CI/CD stack, enabling pipelines to react based on severity, exploitability, and reachability, rather than just the presence of a CVE.
- Use webhook-based enforcement on merge or push to trigger scans through GitHub Actions, GitLab CI, or custom runners tied into Qwiet AI or similar engines.
- Only block PRs when a vulnerability is exploitable at runtime, based on data/control flow analysis, not just static inclusion.
- Add inline annotations to code reviews with stack traces, exploit paths, ownership mappings, and fix recommendations embedded directly into the PR.
- Automatically route findings to responsible teams via Git metadata and Slack, JIRA, or GitHub Issues integration, eliminating cross-team ping-pong.
With this setup, you get security enforcement that fits DevOps velocity, no manual bottlenecks, no false positives slowing down delivery, and a direct path to resolution from within the developer workflow.
AI-Aware DevSecOps – Architecture for the Future
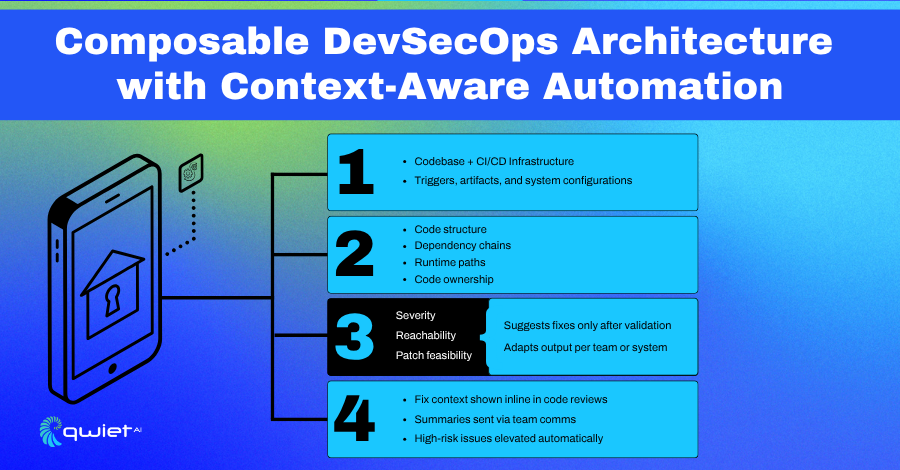
Security as Code: Reasoning, Context, and Action
DevSecOps practices are evolving toward security as code built into infrastructure, wired into pipelines, and structured to adapt. That means leveraging AI not to mimic human triage, but to automate reasoning over code structure and behavior. When paired with a Code Property Graph (CPG), Agentic AI enables this by tracking data flow, control flow, and execution paths within an application.
This level of intelligence shifts analysis from static pattern-matching to real validation. Instead of flagging every usage of a vulnerable function, an AI model can determine if a data flow leads to that function under real-world execution paths. That reduces noise and provides developers with findings tied to actual risk. The goal isn’t more alerts, it’s precision that leads to action.
Once validated, fix recommendations can be automatically generated. At this point, large language models (LLMs) step in not to guess but to offer secure patches only after the exploit path and severity have been confirmed. AI enhances developer workflows without creating more guesswork or false confidence when used this way.
Infrastructure for Intelligent, Context-First Security
Making AI-aware DevSecOps actionable requires infrastructure that supports real-time insights and delivers findings in the tools teams already use. That starts with integrations across messaging, version control, and build systems, and ends with intelligence that can connect the dots between code, context, and ownership.
- Slack and ChatOps integrations deliver daily or per-PR summaries of exploitable findings, tagged with severity, ownership, and fix status, reducing alert chasing and letting engineers act quickly.
- GitHub PR annotations place contextual findings directly into code reviews, with call traces, impacted files, and remediation suggestions tied to the vulnerable code.
- SBOM + CPG pipelines allow teams to correlate known package-level risk with dynamic application-level behavior, surfacing vulnerabilities that matter based on how the code runs.
Together, these layers make security less reactive and more operational. Developers receive timely, contextual, and validated alerts, eliminating the need to leave their workflow or interpret generic scan reports.
Conclusion
Shifting left helped put security earlier in the dev process, but without context and automation, it added friction instead of clarity. Developers are overwhelmed by the volume and vague findings that don’t align with actual risk. To fix that, DevSecOps must be smarter, driven by exploit-aware prioritization and integrated into daily workflows. Qwiet AI was built for this kind of environment. Book a demo to see how it can reduce security noise and help your team deliver safer code more quickly.
FAQs
What are the biggest challenges of DevSecOps in the AI era?
Due to the use of AI-generated code, DevSecOps teams face increased code volume, ambiguous vulnerability reports, and alert fatigue. Without context-aware tools, developers struggle to prioritize what needs fixing.
Why is reachability analysis critical in DevSecOps?
Reachability analysis determines whether a vulnerability can be triggered at runtime. This helps teams avoid wasting time on false positives and focus on real, exploitable security issues.
How can AI improve DevSecOps workflows?
AI can trace exploit paths, validate whether a vulnerability is reachable, and recommend secure fixes. Tools like Qwiet AI utilize agentic models to surface only actionable threats, reducing noise and accelerating triage.
What makes traditional security tools ineffective at scale?
Legacy tools often lack coordination and context, generating overlapping or irrelevant findings. Without exploitability data or code ownership mapping, teams struggle to respond efficiently.
How do you scale secure coding without blocking developers?
Implement triage-first workflows, use contextual filtering in CI/CD, and block merges only for verified, high-priority risks. This enables developers to move forward while still effectively managing security risks.
