Introduction
RESTful APIs are the linchpins of software communication, facilitating data exchange between diverse systems. Their ubiquity and accessibility, however, make them prime targets for exploitation. This article aims to fortify your approach to API security by providing practical tips and shedding light on common vulnerabilities.
The Security Landscape of RESTful APIs
RESTful APIs are crucial in web services, mobile apps, and cloud computing, but their open nature exposes them to cyber threats.
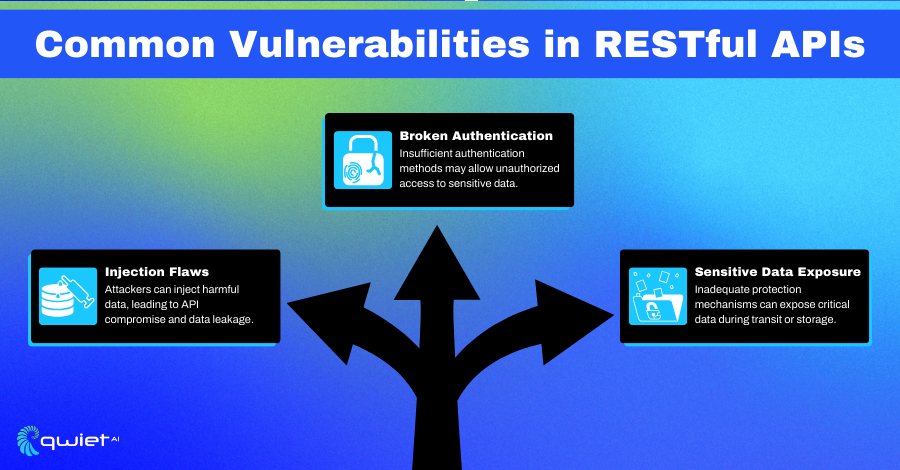
Common Vulnerabilities Include:
- Injection Flaws: Attackers exploit these flaws by injecting malicious data, such as SQL, NoSQL, or command injections. This can compromise the integrity of the API and the underlying systems. For example, SQL injection can manipulate or steal data from your database.
- Broken Authentication: Insecure implementation of authentication mechanisms can result in unauthorized access. This includes flaws like insufficient session management, where session tokens are not properly protected, making them vulnerable to hijacking.
- Sensitive Data Exposure: Poor encryption or inadequate protection mechanisms during data transfer or storage lead to exposure of sensitive data like personal information, credentials, and financial details.
- Misconfigured Security: Inadequate configurations of security settings in the API or its environment can expose the API to various attacks. Common issues include unnecessary HTTP methods, verbose error messages, and insecure default settings.
- Broken Access Control: This occurs when users can access data or perform actions outside of their intended permissions. For instance, a regular user might access administrative functions due to improper enforcement of access controls.
- Cross-Site Scripting (XSS): XSS vulnerabilities allow attackers to inject client-side scripts into web pages viewed by other users. This can hijack user sessions, deface websites, or redirect users to malicious sites.
- Cross-Site Request Forgery (CSRF): Here, unauthorized commands are transmitted from a user that the web application trusts. CSRF attacks can force an end user to execute unwanted actions on a web application to which they are currently authenticated.
- Security Misconfiguration: Security misconfiguration can happen at any level of an application stack, including network services, platforms, web servers, application servers, databases, and custom code.
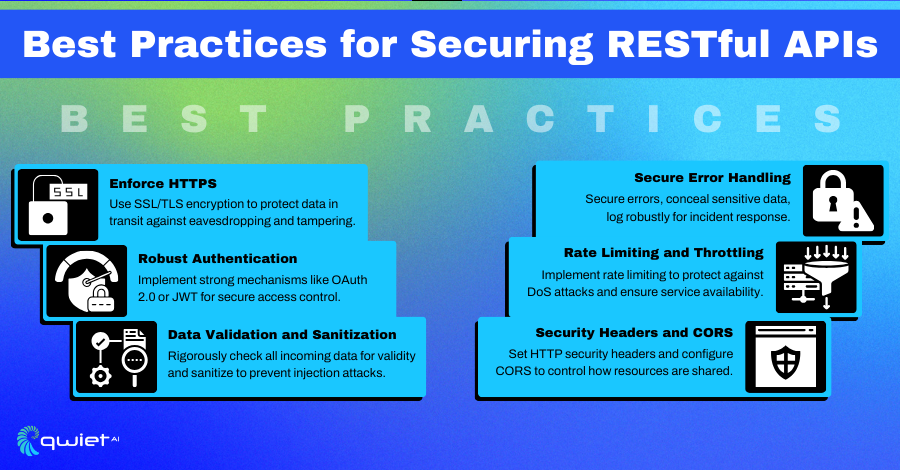
Best Practices for Securing RESTful APIs
1. Robust Authentication and Authorization
Authentication and authorization are the cornerstones of API security. They ensure that only authenticated and authorized users can access the API. Implementing robust authentication mechanisms prevents unauthorized access, ensuring only legitimate users and systems can interact with your API.
Implementing JWT Authentication:
| const jwt = require(‘jsonwebtoken’); // Function to verify token function verifyToken(req, res, next) { const bearerHeader = req.headers[‘authorization’]; if (typeof bearerHeader !== ‘undefined’) { const bearer = bearerHeader.split(‘ ‘); const bearerToken = bearer[1]; req.token = bearerToken; next(); } else { res.sendStatus(403); } } |
The provided JWT authentication code snippet demonstrates how to verify a token in an Express.js application. When a request is made, it checks for an ‘Authorization’ header. The request can proceed if the header is present and the token is valid.
Otherwise, it sends a 403 (Forbidden) response. This method is essential for verifying the identity of users and ensuring that requests are legitimate. It’s a fundamental aspect of securing an API, as it effectively prevents unauthorized access.
2. Data Validation and Sanitization
Data validation and sanitization are crucial for protecting an API from malicious input, which could lead to vulnerabilities like SQL injection. Validating and sanitizing all incoming data ensures that it adheres to the expected format, type, and size, thereby reducing the risk of attacks.
Example of Input Validation in Express.js:
| app.post(‘/api/data’, (req, res) => { const { error } = validateData(req.body); if (error) return res.status(400).send(error.details[0].message); // Proceed with processing the valid data }); |
This code snippet shows an example of how to validate incoming data using Express.js. Before processing the data, it’s checked for validity.
An error is returned to the user if the data does not meet the predefined criteria. This practice is vital for preventing malicious data from entering the system and causing harm or unauthorized actions.
3. HTTPS for Data Encryption
HTTPS ensures that the data transmitted between the client and the server is encrypted. This is crucial for protecting sensitive information from interception and tampering during transit, a common attack vector.
Enforcing HTTPS in Node.js:
| const https = require(‘https’); const fs = require(‘fs’); const options = { key: fs.readFileSync(‘key.pem’), cert: fs.readFileSync(‘cert.pem’) }; https.createServer(options, (req, res) => { res.writeHead(200); res.end(“secure connection”); }).listen(8000); |
This code snippet demonstrates setting up an HTTPS server in Node.js. It involves reading SSL/TLS certificates and creating a secure server that listens for requests.
Implementing HTTPS is a fundamental practice for securing data in transit, as it encrypts the data, making it difficult for attackers to intercept or tamper with it.
4. API Rate Limiting and Throttling
Rate limiting and throttling are important for protecting APIs against abuse, such as brute-force attacks or Denial of Service (DoS) attacks. They help manage the server load and ensure the API remains available to all users.
Setting Up Rate Limiting in Express.js:
| const rateLimit = require(“express-rate-limit”); const limiter = rateLimit({ windowMs: 15 * 60 * 1000, // 15 minutes max: 100 // limit each IP to 100 requests per windowMs }); app.use(limiter); |
This code snippet shows how to implement rate limiting in Express.js. It restricts the requests a user can make within a specified time frame.
This is crucial for preventing abuse and overloading of the API. Controlling the request rate helps maintain the service’s availability and performance.
5. Error Handling and Logging
Proper error handling and logging are key for diagnosing and responding to issues in an API. Secure error handling ensures that errors do not reveal sensitive information while logging record activities for monitoring and incident response.
Secure Error Handling:
| app.use((err, req, res, next) => { console.error(err.stack); res.status(500).send(‘Something broke!’); }); |
In this snippet, a middleware for handling errors in Express.js is shown. It logs the error and sends a generic error message to the client. This approach is important for security because it prevents the exposure of sensitive error details, which attackers could exploit.
6. Security Headers and CORS
Implementing security headers and correctly configuring Cross-Origin Resource Sharing (CORS) is vital for protecting against specific web-based attacks. These settings help control how the API interacts with other websites and ensure it does not inadvertently expose itself or its users to risks.
Setting Security Headers in Express.js:
| const helmet = require(‘helmet’); app.use(helmet()); |
This code snippet demonstrates the use of the ‘helmet’ package to set HTTP security headers in Express.js. Security headers like Content Security Policy (CSP) and X-Frame-Options help mitigate clickjacking and cross-site scripting risks.
Proper CORS configuration is also crucial in defining how resources can be shared with different origins, which is essential for the security of web applications.
Conclusion
To secure RESTful APIs, you need a multi-step plan. This plan includes strong authentication, careful data handling, and proactive security measures. By incorporating these practices into your API development and maintenance, you can protect your data from cyber threats. Remember, being watchful is crucial for API security.
Discover how Qwiet can enhance your API’s safety. Book a demo to explore Qwiet’s capabilities in identifying and addressing vulnerabilities in RESTful APIs.