Detect and address logic vulnerabilities in your software before they pose a threat.
Uncover Business Logic Vulnerabilities
What are business logic flaws?
Business logic flaws arise from vulnerabilities in an application’s operational procedures, not from typical coding errors. They result from overlooked scenarios or incorrect assumptions about user interactions, often bypassing traditional security checks. Examples include:
- Price Manipulation: Changing product prices in an e-commerce cart
- Bypassing Workflows: Skipping approval processes in financial transactions
- Misusing Promotions: Exploiting discount codes more times than intended
- Elevated Access: Gaining unauthorized privileges due to weak role checks

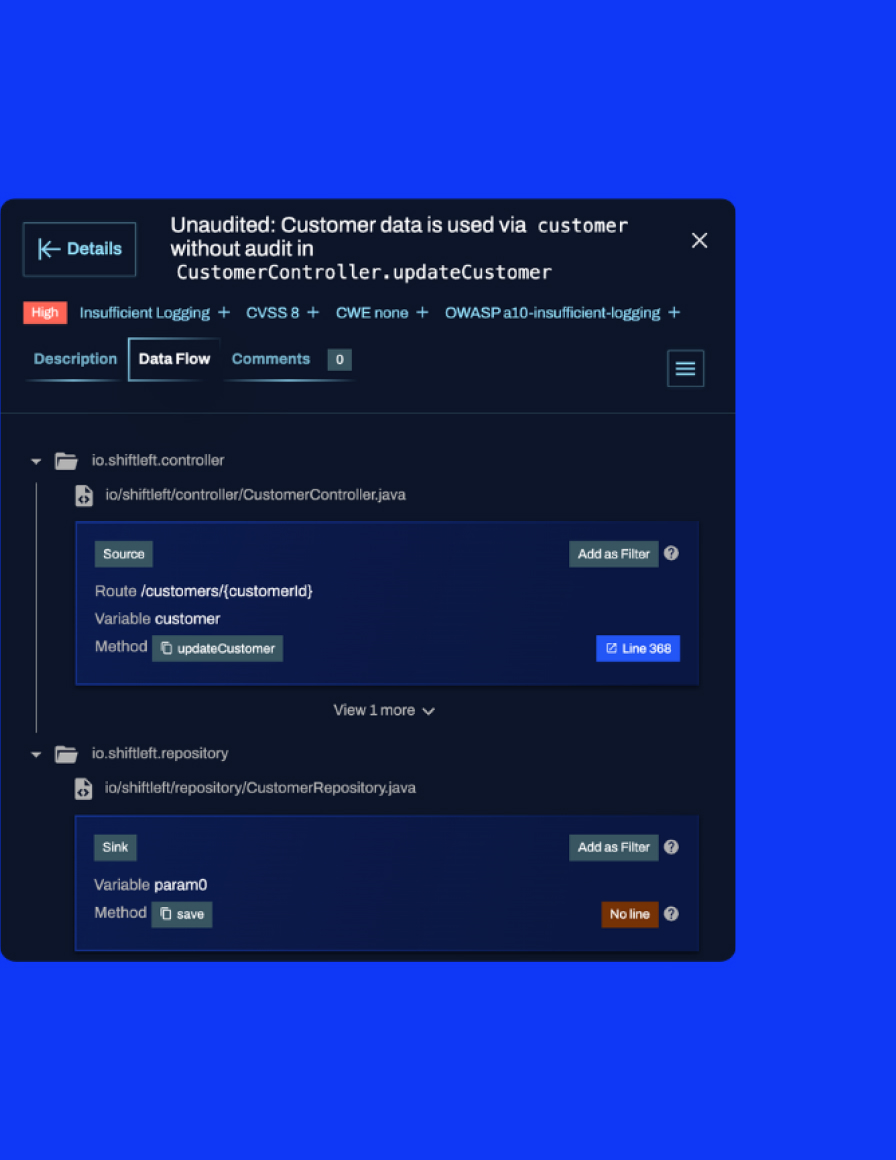
Deep dive with application awareness
While tools like static analysis and grep engines excel at detecting common coding issues like SQLi and XSS, they falter when it comes to custom application logic. Their limitations include not identifying:
- Lapses in authorization checks, leading to privilege escalation
- Mishandling of confidential data within workflows
- Breaches in intricate validation logic for transactions
- Bypassing of multi-phase processes via backdoors
Such tools excel for standard coding errors. However, business logic flaws, being unique to each application, elude these traditional scanners. A more nuanced approach is required to truly understand the developer’s intent.
Deep dive with application awareness
True logic flaw detection demands code analysis resembling human comprehension. Our solution achieves this by:
- Charting data movement across modules
Directing control paths that drive program execution - Extracting insights from code frameworks and interdependencies
- Deciphering business protocols and multi-stage processes
By being attuned to the application, we reveal vulnerabilities that escape conventional tools. Leveraging a graph database, we monitor data compromise and authorization pathways to unveil concealed risks.

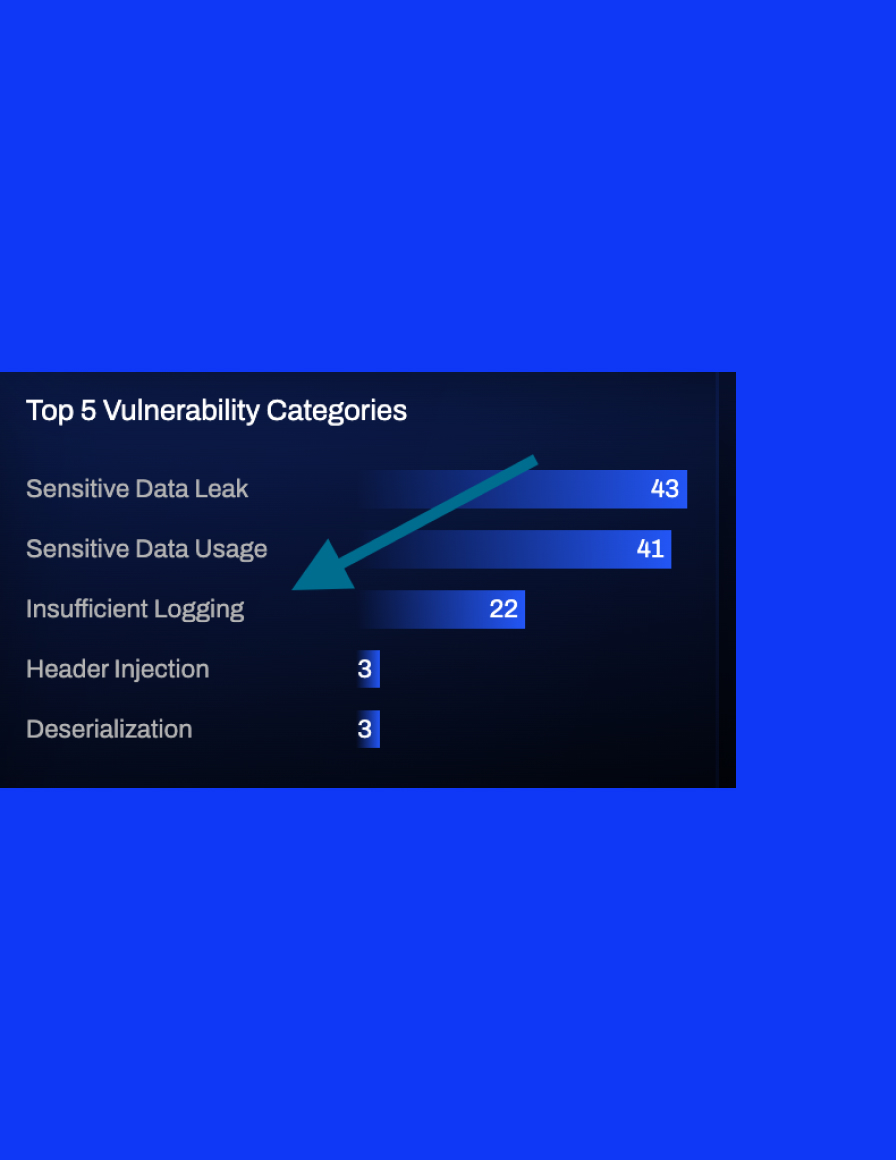
Rectify and reinforce
Locating vulnerabilities is merely step one. Addressing business logic flaws demands a distinct strategy since:
- Logic frequently spans multiple distributed microservices
- Some antiquated processes resist reconfiguration
- Remedies involve architectural changes, not merely code tweaks
- Ensuring the accuracy of intricate logic is a meticulous task
Our platform offers precise recommendations to safely rectify flaws. We fortify validation, enhance data management, seal authorization loopholes, and remain vigilant for anomalies.
In a nutshell: reduce the risk of business logic flaws with Qwiet ai
Qwiet’s Qwiet appsec experts work with your team to understand your applications and their intended functionality. After careful analysis, Qwiet can help to create and implement custom policies around your code to ensure that your application functions as intended without any unintended logic flaws, and continuously monitor the application with Qwiet AI’s application security testing platform.
Don’t allow flawed logic to drain business value. Get started with a demo showing how our platform finds and fixes costly logic vulnerabilities.
Contact us now to see how we can help
