Introduction
SQL Injection: It’s like the pesky mosquito of web security, always buzzing around, looking for a way to suck the life out of your database. But don’t break out the bug spray just yet; we’ve got two powerful tools to swat this bug: Parameterized Queries and Stored Procedures. So, let’s roll up our sleeves and get down to the nitty-gritty of SQL Injection defense.
What is SQL Injection?
SQL Injection is a type of cyber-attack that targets the vulnerabilities in a web application’s database layer. Attackers exploit these vulnerabilities by inserting malicious SQL code into a query, which can then be executed by the database. The implications of such an attack can be severe, ranging from unauthorized data access, data manipulation, to even database structure alterations.
For developers, understanding the mechanics of SQL Injection is crucial, as it underscores the importance of implementing secure coding practices from the outset.
The Two Contenders: Parameterized Queries and Stored Procedures
Parameterized Queries
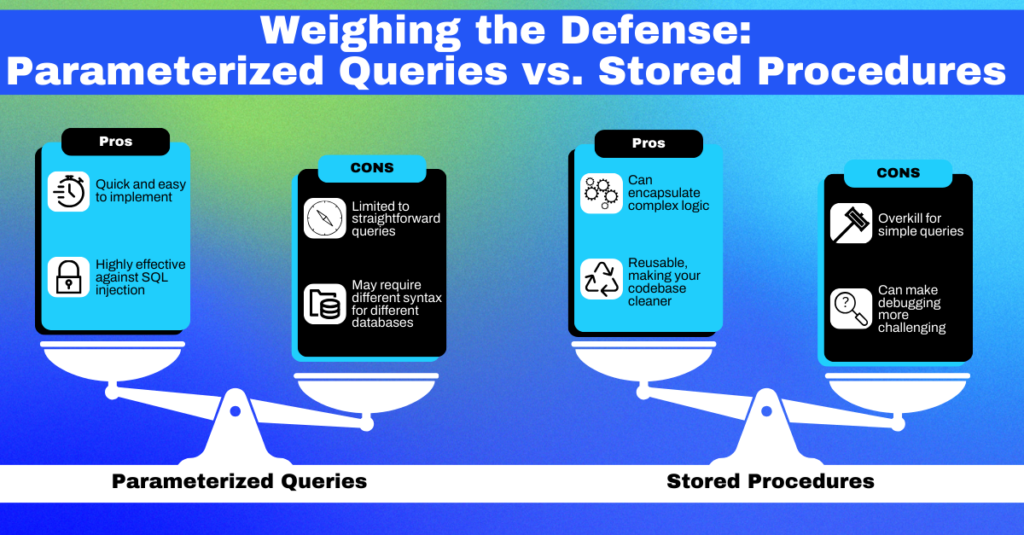
Parameterized Queries offer a robust defense mechanism against SQL Injection. At its core, this method separates SQL logic from the data being passed. Using placeholders instead of directly embedding user input into queries, the database strictly recognizes the input as data.
This means that even if an attacker tries to insert malicious code, the database won’t execute it as a command. As a developer, adopting parameterized queries is not just a best practice; it’s a fundamental shift in how user input is processed, ensuring a higher level of security.
Code Snippet: Parameterized Query in Python using psycopg2
| import psycopg2 # Connect to the database conn = psycopg2.connect(“dbname=test user=postgres password=secret”) # Create a cursor object cur = conn.cursor() # Use Parameterized Query query = “SELECT * FROM users WHERE username = %s AND password = %s;” cur.execute(query, (‘username’, ‘password’)) # Fetch results results = cur.fetchall() |
In this Python code snippet, we’re using the psycopg2 library to connect to a PostgreSQL database. The SQL query string contains %s as placeholders for the username and password. When we execute this query using cur.execute(query, (‘username’, ‘password’)), the psycopg2 library ensures that these placeholders are replaced with the actual username and password in a safe way that prevents SQL Injection.
Stored Procedures
Stored Procedures serve as another layer of protection against SQL Injection. These sets of SQL statements have been predefined and stored in the database. When a stored procedure is called, it executes without requiring the application to build an SQL statement with user input.
This reduces the risk of any malicious input being executed. Developers should note that while stored procedures can enhance security, they should still be combined with other security practices, like using parameterized queries within the procedures, to ensure maximum protection.
Code Snippet: Stored Procedure in SQL Server
| CREATE PROCEDURE GetUser @username nvarchar(50), @password nvarchar(50) AS BEGIN SELECT * FROM users WHERE username = @username AND password = @password; END; |
In this SQL snippet, we’re defining a stored procedure named GetUser. It takes two parameters: @username and @password. The SQL query within the stored procedure uses these parameters to fetch data from the users table. Because the query is pre-compiled and stored on the database server, it’s less susceptible to SQL Injection attacks.
Pros and Cons
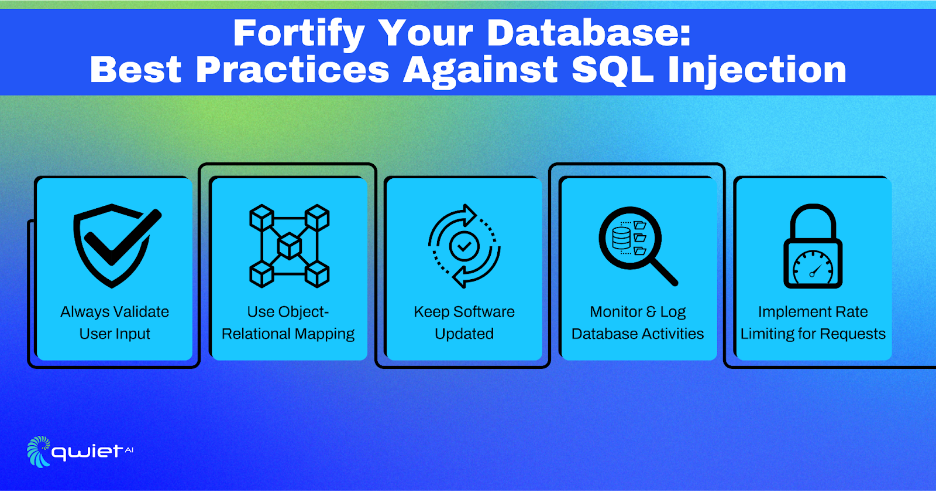
Best Practices
Always Validate User Input
Input validation is a cornerstone of secure coding. Ensuring that every piece of data entering your system conforms to expected parameters reduces the risk of malicious input wreaking havoc.
Developers should implement stringent validation checks, considering length, type, format, and range, to ensure that only legitimate data gets processed.
Use Object-Relational Mapping (ORM)
Object-relational mapping (ORM) is a technique that lets developers interact with their database as they would with SQL. But, instead of writing SQL code, they can use the ORM system to interact with the database using their preferred programming language. ORM systems often have built-in protections against SQL Injection, making them a valuable tool for developers aiming to write secure applications.
Keep Software Updated
Software updates often address known vulnerabilities. Developers can shield their applications from known threats by ensuring that all software, including databases and web application frameworks, are regularly updated. It’s essential to monitor for updates and patches actively and apply them promptly.
Advanced Techniques
Logging and Monitoring
Effective logging and monitoring can serve as an early warning system for potential security threats. By keeping track of database queries and monitoring for unusual patterns, developers can detect and respond to potential SQL Injection attempts swiftly.
Implementing a robust logging system that captures detailed information can be invaluable in both preventing attacks and diagnosing any breaches..
| # Example: Logging query in Python import logging logging.basicConfig(level=logging.INFO) logging.info(f“Executing query: {query}”) |
This Python code snippet uses the logging library to log the executed query, helping you track what’s happening in your application.
Rate Limiting
Rate limiting controls the rate at which your application processes requests. By implementing rate limiting, developers can prevent automated scripts from bombarding the application with a high volume of requests, which could indicate an attack.
This helps mitigate potential threats and ensures that genuine users continue to have a smooth experience.
| # Example: Rate limiting in Python using Flask-Limiter from flask_limiter import Limiter limiter = Limiter(app, key_func=get_remote_address) @limiter.limit(“5 per minute”) def login(): # login logic here |
Here, we’re using Flask-Limiter to limit the login attempts to 5 per minute per IP address. This helps in mitigating brute-force SQL Injection attacks.
Conclusion
SQL Injection is a formidable opponent, but it’s not unbeatable. You can secure your database and keep your data safe with the right techniques. Whether you choose Parameterized Queries or Stored Procedures depends on your specific needs, but either way, the key is to be consistent and vigilant. So fortify your database, and let your queries flow like a well-secured river of data. Interested in taking your application security to the next level? Book a demo with us today and explore how Qwiet can help!