Top ten OWASP resources that improves your application security
Employee cybersecurity training is ranked as one of the top three categories where many companies are increasing security spending. This demand for better training highlights the incredible value offered by OWASP, the Open Web Application Security Project. OWASP is a non-profit organization dedicated to improving software security. The organization offers several security-focused resources to developers, including tools, social events, and training opportunities.
OWASP has hundreds of chapters across the globe, supported by tens of thousands of members. The organization also enjoys the sponsorship of several corporations including Adobe, Atlassian, Symantec, and GitLab, among others. Individuals wishing to become more involved with the direction of OWASP are encouraged to join one of the organization’s committees.
OWASP provides several low-cost (or free) AppSec resources to anyone wishing to improve the security of their code. This top ten list of OWASP offerings can help organizations determine which resources are best for them.
Top Ten OWASP AppSec Resources
Virtual Training Events
OWASP hosts year-round training events covering a wide range of AppSec topics. The OWASP Virtual Training Courses occur on two consecutive days, each consisting of a four-hour session. The low-cost training is available to everyone, members are offered a discount. The topics covered at these events are continuously changing, but some recent examples include:
- Applied Data Science and Machine Learning for Cyber Security
- Bootstrap and Improve Your SDLC with OWASP SAMM — ASAP!
- DevSecOps — Automating Security in DevOps
- Security for Web Developers — an Offensive Approach
The OWASP Top 10 Lists
OWASP researches and publishes top ten lists outlining the direst security risks app developers face. Examples include the OWASP Top Ten Web Application Security Risks, the API Security Top Ten, and the OWASP Mobile Top Ten. These lists help developers identify and avoid common security issues that plague application development. Project managers can use these lists to proactively ensure risks are addressed during the SDLC.
The OWASP Mobile Security Resources
OWASP created the Mobile Security Testing Guide as a comprehensive reference for testing mobile applications. The guide covers “processes, techniques, and tools used during a mobile app security test”, and includes several test cases for developers to analyze. Both iOS and Android platforms are included in the guide. It is available for a voluntary donation to interested parties.
The Mobile Application Security Verification Standard (MASVS) is a collaborative reference guide for creating secure mobile apps. It is available in several languages and can be found on GitBook. OWASP also offers multiple mobile security presentations.
OWASP Web Security Resources
The OWASP Web Security Testing Guide offers a complete security framework for testing web apps and services. The guide is focused on integrating app security testing into the SDLC. It contains detailed effective techniques for app testing useful for devs, pen testers, and software-related organizations.
OWASP also offers the Benchmark Project, a testing framework for gauging the performance of automated testing tools. The project includes a web app that contains thousands of CWE-mapped vulnerabilities. Devs can run SAST, DAST, and IAST tools on the app to determine how well each detects problems. The Benchmark Project generates performance scorecards for many popular testing tools as well.
The OWASP Dependency Track
The OWASP Dependency Track is a tool that aims to help devs identify and reduce risks in the software supply chain. The Dependency Track helps developers track the third-party components by creating Software Bill of Materials (SBOM).

- Screen capture of the OWASP Dependency Track tool available at_ https://dependencytrack.org/
The Software Bill of Materials is essentially an inventory of software components that an application uses, and offers component-level transparency of an application — similar to the way a list of ingredients identifies the contents of a recipe.
Generating an SBOM is the first step to gaining insight about the open source security risks in that application. OWASP offers access to the Dependency Track tool at https://dependencytrack.org/. For additional security coverage over third-party code, ShiftLeft.io offers an intelligent SCA tool that scans your third-party components for vulnerabilities.
Juice Shop Non-Secure App
Juice shop is an intentionally non-secure app that contains all the flaws listed in the OWASP Top Ten along with several other vulnerabilities. Devs can use Juice Shop to identify security flaws in code, test security tools, and perform other kinds of AppSec related training. The interactive nature of Juice Shop may appeal to those who prefer interactive learning and acquiring hands-on experience.
Lightning Conferences
OWASP Lightning Conferences are periodic virtual events held throughout the year. The conferences feature topics pertinent to AppSec professionals and are led by sponsors or featured speakers. Events run 90 minutes or less, and may be free of charge for attendees. The current schedule of Lightning Conferences is available at https://lightning.owasp.org/.
OWASP ModSecurity Core Rule Set
The OWASP ModSecurity Core Rule Set (CRS) provides pre-made attack detection rules for “ModSecurity or compatible web application firewalls”. The ruleset is engineered to protect apps from the OWASP Top Ten and other threats. In particular, the ModSecurity CRS protects against:
- SQL injection
- Cross site scripting
- Local file inclusion
The CRS is streamlined to maximize protection while minimizing false alerts. There are a number of tutorials available to assist with setting up, understanding, and using ModSecurity on the OWASP site.
The OWASP Software Assurance Maturity Model (SAMM)
The Software Assurance Maturity Model (SAMM) was created to help organizations improve their ability to design, develop, and deploy secure software. It provides self-assessment tools that organizations can use throughout the SDLC to analyze security performance. The SAMM is designed to be both “technology and process agnostic”, making it useful to a broad range of readers and developers.
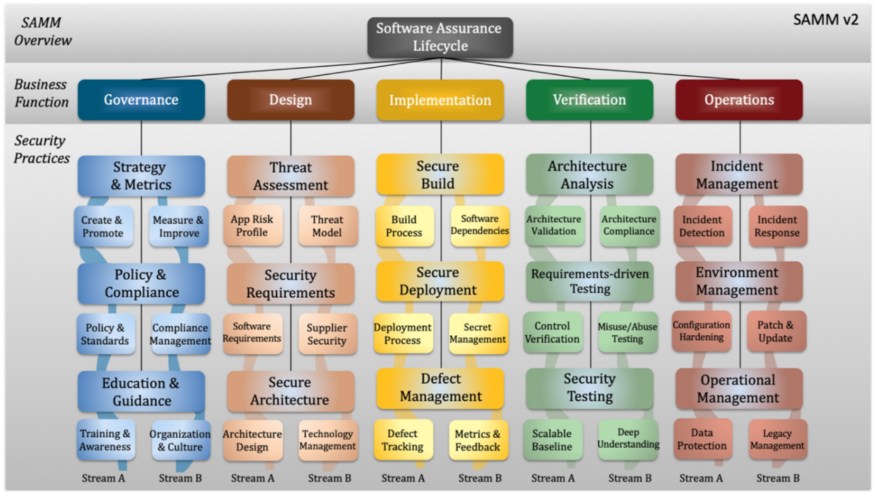
2. Screen capture of the main sections and components of the OWASP Software Assurance Maturity Model (SAMM)_
The SAMM model has been evolving for over ten years. Updates to the model are often made to ensure the content reflects current best practices and to accommodate more organization types. The most recent version of SAMM was released in January of 2020.
The OWASP Security Knowledge Framework
The OWASP Security Knowledge Framework (SKF) was created to help developers learn and adopt securing coding principles. It is an open-source project that offers secure software development training in multiple programming languages. The SKF trains developers to be more security-conscious by providing sample projects accompanied by security checklists, labs, and code examples.
Benefits of Using OWASP Resources
There is a well-known adage that encapsulates the value of OWASP — it goes “an ounce of prevention is worth a pound of cure”. OWASP aims to prevent insecure code from being written and released, saving organizations from the massive costs incurred by a software breach. In addition, developers who learn to code more securely gain lifelong skills that will continuously benefit themselves, their employers, and their users.
OWASP offers so many security training resources it can be difficult to know where to begin. The OWASP Benchmark Project Quick Start provides a good introduction for developers interested in diving directly into application security testing. For devs seeking effective app testing tools that detect the OWASP Top Ten vulnerabilities, consider using ShiftLeft CORE, a next-generation application security testing platform. Shiftleft’s Next-gen Static Application Security Test (NG-SAST) achieved best-in-class OWASP benchmark performance scores with data and information flows.
